Wi-Fi is a wireless network between laptops through which you can exchange files at a distance, play computer games with friends and neighbors, and connect to Wi-Fi hotspots cafes and metro.
Range wifi signal is about 100 meters of line of sight, without obstructions and about 15 meters passing through the stone walls of a residential building.
These indicators may vary depending on the model of the Wi-Fi device built into your laptop.
Usage wireless network will solve all the problems associated with laying network cables between several users. Previously, in order to connect 3 or more computers, you needed to purchase Switch or Hub devices, using a Wi-Fi wireless network, you do not need to connect others additional devices. Setting up the parameters for creating a wireless network is quite simple and does not take much time. On each operating system, the location of the options for setting up the network is different, so we will consider the method of setting up Wi-Fi in the newest Windows 7 operating system, which is most often used on laptops.Before you start entering the settings to create a network, you need to make sure that the device is turned on. To do this, in the window Control Panel->, Network and Internet->, Network Connections, you can see the wireless network connection adapter. If the sign of the wireless network connection is colorless, you need to right-click on it and turn on the adapter.
The same thing needs to be checked on all laptops to which we want to connect. Now it is necessary to register the same name of the working group on all machines. The default names can be "MSHOME" and "WORKGROUP". Select any name and write it on all machines in the computer properties (right-click on the "My Computer" icon). After that, go to Control Panel->, Network and Internet->, Network and Sharing Center. On the left side of the tab, you see the following subsections: "Manage wireless networks", "Change adapter settings", "Change advanced settings" public access". First you need in the subsection "Changing adapter settings", in the properties wireless adapter write "Internet Protocol Version 4 (TCP/IPv4)". In the properties of this protocol, enter the IP address: 192.168.0.1, where the last digit "1" indicates the number of your laptop in the wireless network and it should not be repeated by other users. On the second laptop, enter the IP address: 192.168.0.2, on the third, enter the IP address: 192.168.0.3, and so on, changing only the last digit of the IP address. In general, the meaning of these numbers may be different (for example: 010.010.010.1, 144.123.34.1), but for an illustrative example, we will use the one proposed above. Next, click in the "Subnet Mask" field, and we get the standard 255.255.255.0. Do the same for other laptops. So, we have entered the necessary parameters and we can start creating a new Wi-Fi network. When the device is turned on, in the lower right corner, next to the volume control, you can see the current connections and Wi-Fi networks that are in range.
For creating new network it is necessary on the first laptop in the "Wireless Network Management" subsection, select "Add", and "Create a network profile manually". In the window that appears, enter the name of the profile, "Security Type", ->, No Authentication and check two checkboxes for "Start this connection automatically", and "Connect if the network is not broadcasting". After creating a network, other users will see in the lower right corner of the taskbar, among the current connections, the name of your network. By connecting by double-clicking on it, you will be on the same network and can start exchanging files. To share files, you need to open access to folders and files on your laptop. To do this, on the required folder in the properties, selecting the "Access" tab, clicking the share, you will see a window in which you need to select "ALL", ->, "Add", ->, "Sharing".
To check network performance and quick access to other users' files, you need to write 192.168.0.2 in the address bar of any open window to enter the second computer, 192.168.0.3 on the third & hellip, 192.168.0.10 on the tenth. You will not be able to access the files of other wireless network users if they do not share any of the folders. Wireless Wi-Fi networks are already widely used, so you can easily connect to others. open networks that you can catch with your Wi-Fi device.
The documents
The pcQuality.ru team works under the Fruktus LLC brand.
What qualitatively What sets our team apart from others?
- All our employees are highly qualified specialists with over 7 years of experience.
- Many of our valued customers have been served by our experts for over 20 years (the process of working with customers began before the formation of the brand).
- Over the past 5 years, not a single client has left us, which is confirmed by the reviews.
We strive to maintain a focus on the quality of the services provided, we will be glad to see you among our customers!
Bookmarking
To add this page to your favorites, press CTRL + D
1.Connecting a computer to a ZyXel Keenetic Lite router:
Before settingZyxelKeeneticLite, You plug the router's power adapter into an electrical outlet, connect the provider's cable to WAN router interface, and one of LAN ports, connect the yellow patch cord to the network card of your computer. Then you need to change the settings TCP/IP from the network card to automatically receive values(DHCP client). You can do this in the following way:
Windows XP: Start - Control Panel - Network Connections -( right click on) Connection via local network(if there is no "local network connection" icon (see Figure 1), then this either indicates that it has been renamed or the driver for the network card is not installed.) - Properties - Internet Protocol(TCP/IP) -Properties- further see fig. one
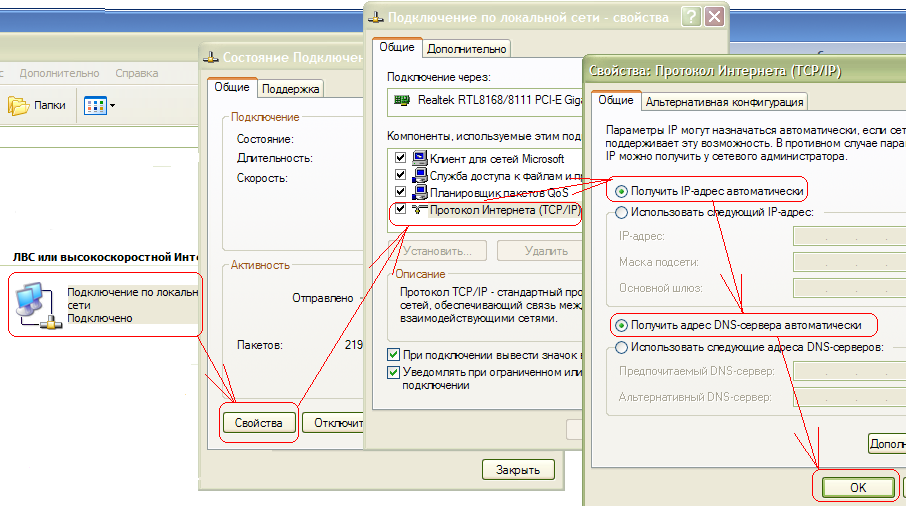
rice. one
Windows 7 : Start —> Control Panel -> Network and Internet -> Network and Sharing Center -> (left column) Change adapter settings -> (right click on) Local Area Connection -> Properties -> Internet Protocol Version 4 -> Properties ->further see fig. 2
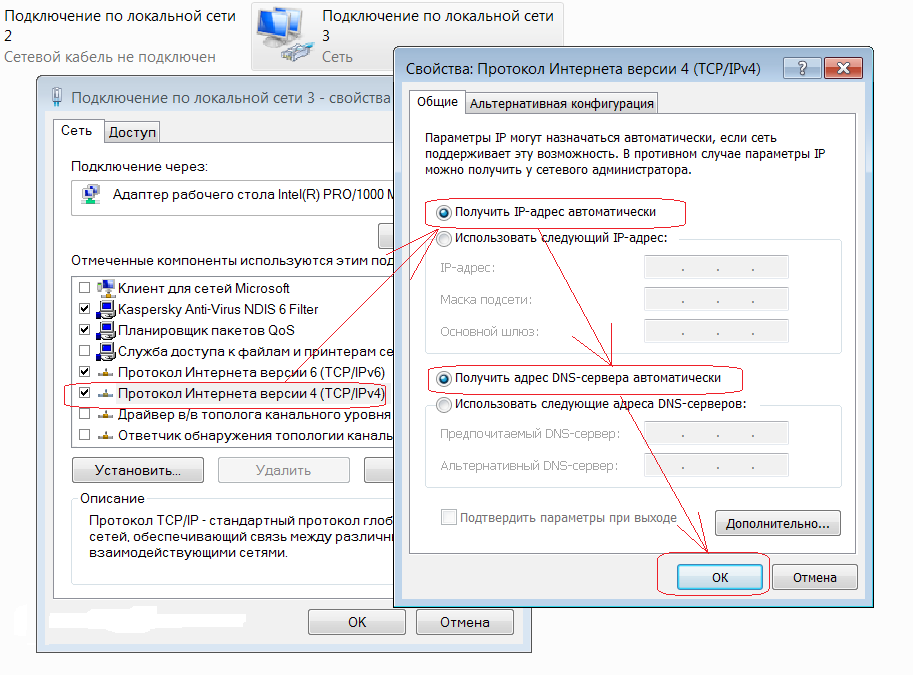
rice. 2
Then open a browser (Opera, Internet Explorer, Mozilla, ...), in the address bar go to: http://192.168.1.1 , a window should appear:
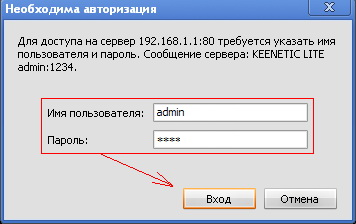
fig.3
username: admin, password: 1234
2. Configuring the WAN interface (that part of the router that "looks" towards the provider):
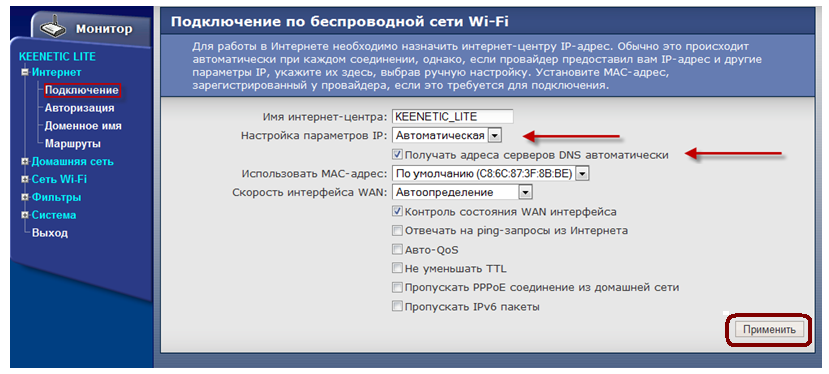
3. Setting up a wi-fi connection:
Router setting:
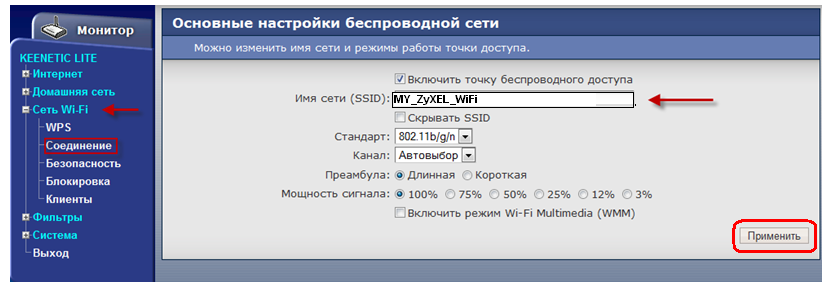
Network name (SSID) - the name of your wi-fi network. An arbitrary name written in Latin letters, for example, as in the figure MY_ZyXEL_WiFi.
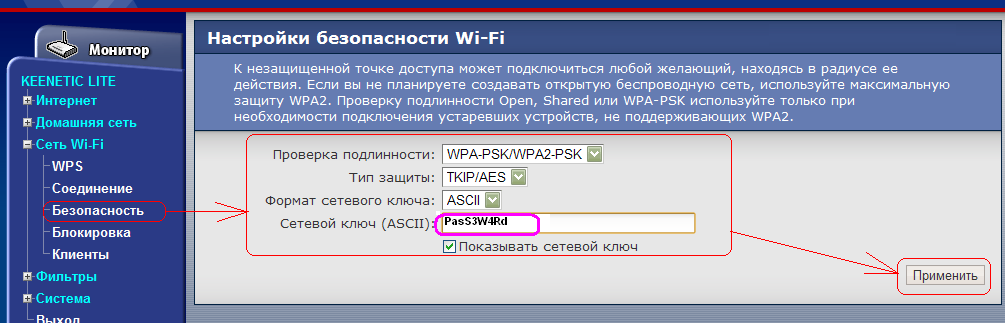
network key (ASCII) a password you have arbitrarily thought up (written in the English layout), which you need to write down in the future, it will come in handy. Click Apply. Wi-Fi router setup is complete. It remains to configure the wireless card of your computer (laptop).
WiFi card setup:
WindowsXP: Start - Control Panel - Network Connections.
Windows 7 : Start —> Control Panel —> Network and Internet —> Network and Sharing Center —> (left column) Change adapter settings.
Make sure you have the "Wireless Network Connection" icon (if the icon is missing, this either means that it has been renamed, or the driver for the wi-fi card is not installed.)
If you have Windows XP:
Next, you need to understand which application in Windows XP is responsible for connecting to WiFi networks. It may be a special utility from the manufacturer WiFi module that comes with the adapter driver wireless communication or maybe Windows itself. The fact is that such special utilities intercept control over the wireless communication module from operating system, then Windows XP just won't see wireless WiFi networks, about which the system will not be slow to inform you:
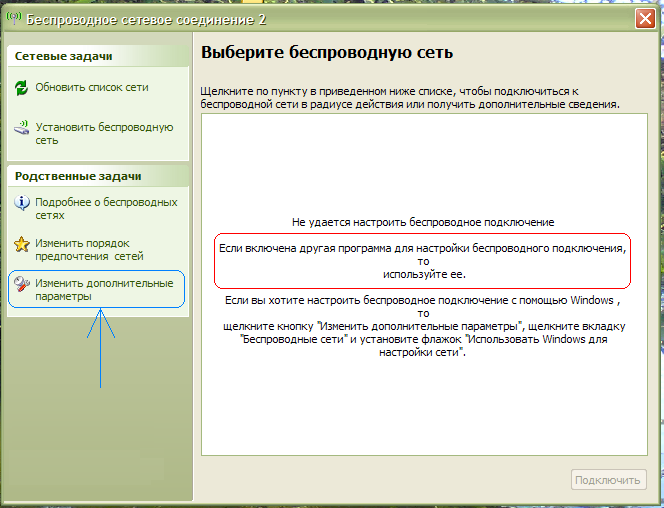
In principle, you can return control of wireless networks back to the operating system, for this you need in the window in Fig. click on the link on the left Change advanced options. Next, open the " Wireless networks' and check the box there. "Use Windows for network settings" :
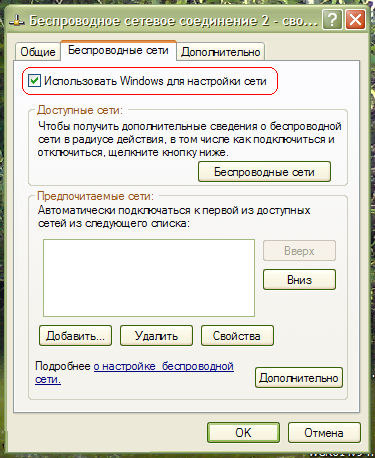
click OK.
To connect to your wireless network (MY_ZyXEL_WiFi) from wifi router in windows xp You need to follow the following path: Start- (settings) - Control Panel - Network connections- then double click on the icon Wireless network connection. Next, select your network from the listand double-click on it with the left button, see fig.
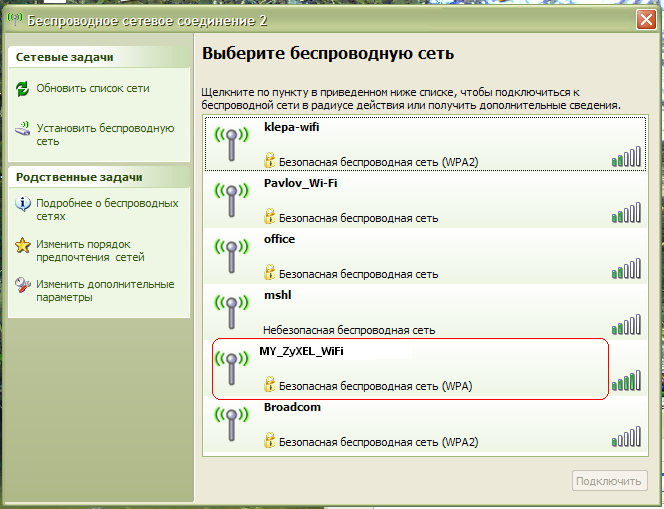
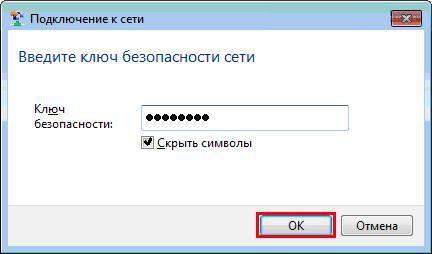
Then Windows XP will ask you for a password to connect to the wireless wifi networks(see fig.). Here you need to specify, which is used for the security of the wi-fi network in your router. Enter the key, its confirmation (i.e. the same key is re-entered) below and press To plug.
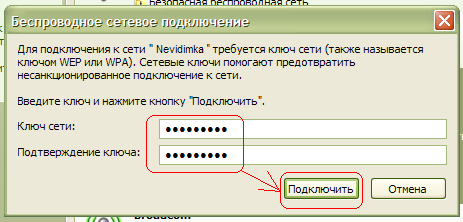
Setup completed.
If you have Windows 7:
Click: Start —> Control Panel —> Network and Internet —> Network and Sharing Center —> (left column) Change adapter settings—>"Wireless Network Connection":
Then right click on , select item "Connect / Disconnect" :
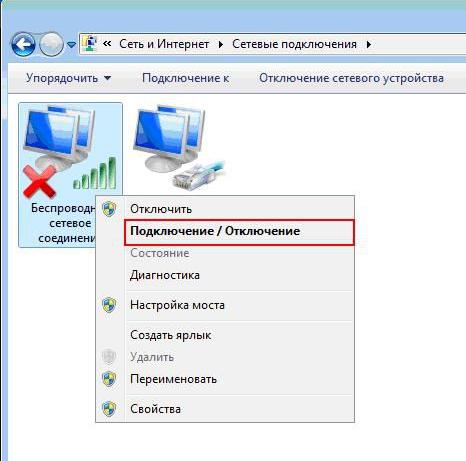
In the list of found wireless networks, find and select your network - MY_ZyXEL_WiFi. Then we press the button "Connection" .
![]()
In the next window, you must enter, which was invented when setting up wifi in the router. Enter the key and press the button Ok .
Upon successful connection "Wireless Network Connection" will look like this.

Setup completed.
Check with a browser. Is the internet working? If the Internet is working, then as a result of the configuration you have received a configured router with a secure wi-fi channel.
Sometimes you need to reset the adapter. To perform this task, you must enter the network connections section. This is done in the following order: you need to go to the control panel from the Start command menu. Using the search system, find the adapter, then in the section for managing sharing and networks, select "Display network connections". Right-click on the adapter icon and select the "Disable" command before resetting the wireless network settings. If you need to enter or confirm an administrator password, you must enter the password or confirm it.
By clicking on the right mouse button on the icon of the network adapter, you must select the enable command. If you are prompted to enter an administrator password or require confirmation, you must enter the password (confirm). The network adapter has now returned to its default settings. You can read about how to connect the DVR to the network in the corresponding section of this site. Now that the settings have been changed, you should try to connect to the network again. You can also use a dedicated network troubleshooter to verify that the adapter is working properly.
The sequence of actions is as follows: you need to open the troubleshooter. To do this, right-click the mouse to select the network icon located in the notifications, click the troubleshoot command. Information on how to send a message over the network and others helpful tips available to visitors to this site. If, after performing the steps to reset the network adapter, as well as updating the drivers in the network troubleshooter, it still indicates that there are problems with the adapter, you still need to replace the adapter.
Buy network adapter available in specialized stores. Its installation is not difficult. On special sites, you can find information on how to install the adapter, how to set up a vpn network, and much more. The device also comes with instructions with which you can install the network adapter yourself. In case of problems, you should seek the help of a specialist. If it is decided that the adapter should not be used, then it must either be removed from the system or simply disabled. Many users are interested in how to enter social networks. By clicking on the link or using the search engine, you can get the necessary information.
When an adapter is disabled, it will become inactive, i.e. it will not be used. The sequence of actions is as follows: from the "Network Connections" component (opens when you click on "Start" and go to the section for managing networks and sharing) through the search system, you need to find the adapter (type "adapter" in the search box) and click on the item "Show network connections" in the network control center. It remains to click on the "disable" command. If a password or confirmation is required, the password (confirmation) must be entered.
The Multi-SSID tab (Multi SSID) is used to configure additional SSIDs, with which you can organize virtual networks and differentiate connections to an access point at the guest SSID level, which can be done due to the presence of a corresponding mechanism in the D-Link DWL-2100 AP than can boast not every access point (Fig. 15.20).
Rice. 15.20. Multi-SSID Tab Contents
The tab contains a group of parameters that is repeated three times, but for different SSIDs. Thus, up to three different guest SSIDs can be configured. Set different SSIDs after setting the master SSID using the following settings.
Enable VLan Status - By default, the ability to use multiple SSIDs is disabled. To enable it, you must check this box.
– Master SSID (Main SSID) - the parameter does not change, since the value of the access point's SSID, which is configured earlier, is used. In fact, this field displays the current SSID assigned to the access point.
– Security - The parameter is also not editable and displays only the current security mechanism, such as Open or Shared.
– VLan Group ID (Virtual Group ID)—The created virtual groups are distinguished by their number. More than 4000 numbers are available for their numbering, starting from one. As a rule, the main group, that is, the one that contains the main SSID, is designated by the very first number, that is, one, as shown in Fig. 15.20.
Enable Guest SSID1 Status - This check box contains options that describe the optional SSID, specifically SSID1. To enable this feature, you must check this box.
– SSID—the parameter contains a unique identifier, in particular SSID1, when selecting which you must follow the same rules as when selecting the main SSID. This is especially important if the SSID broadcast is disabled and you need to know exactly this SSID to connect to the network. In this case, you can easily weed out unwanted connections from the outside.
– Security - This parameter describes the authentication method. However, additional authentication method configuration is possible only if the Security parameter in the Enable VLan Status area is set to Open or Shared. At the same time, None, Open, or Shared values become available for selection.
– Webkey - You can select the length of the encryption key (64, 128 and 152 bits) that will be used to encrypt data transmitted over the network between devices that use Guest SSID1. Having chosen the key length, you must immediately set the type of character string (HEX or ASCII) representing the key, and the key itself.
– VLan Group ID (Virtual Group ID) - as in the case of the main virtual group, the created virtual group must also have its own unique number - any number of interval 1-4095 different from the main virtual group number. In our example, the main virtual group is numbered 1, and the group with guest SSID1 is numbered 2.
– Key Index - as usual, up to four keys of different or the same length can be used to encrypt data. To switch between them, use the Key Index parameter.
Similarly, you can configure two more guest SSIDs, if, of course, this is necessary.
Once you've set up your access point, you'll need to set up your other access points and wireless adapters accordingly.
Configuring Wireless Adapter Settings
After installing the driver for the D-Link DWL-G122 wireless adapter, an icon in the form of the letter "D" appears in the notification area on the Taskbar.
In the future, you can configure the adapter by right-clicking on it and selecting in the appeared context menu item Wireless Network (Wireless network) (Fig. 15.21) or simply by double-clicking on it with the mouse button.
Rice. 15.21. Configuring the adapter through the item Wireless Network (Wireless network)
By default, even if you run the native adapter configuration utility, the standard Windows configuration wizard will open. Naturally, since there is a "native" configuration utility, you can configure the adapter using it. Moreover, the “native” utility allows you to configure many more different parameters than the standard Windows hardware setup wizard.
The following shows examples of using both options and how to switch between them.
Using the Standard Configuration Mechanism
By default, the adapter is always configured using Windows mechanisms, unless the user specifies a configuration option. wireless connection.
To launch the configuration mechanism, just double-click on the D-shaped icon in the notification area on the Taskbar. In the future (when it is indicated that by default you need to use the “native” utility for configuration), in order to launch the standard adapter configuration mechanism, you will need to open the wireless connection properties window (see Figure 15.1), in which you can configure it. Here you can also set the parameters of the adapter itself.
To change the adapter settings, click the Configure button - the wireless adapter properties window will open, containing several tabs with settings and useful information.
Let's go to the Advanced tab, which contains the parameters that affect the operation of the device on the network (Fig. 15.22).
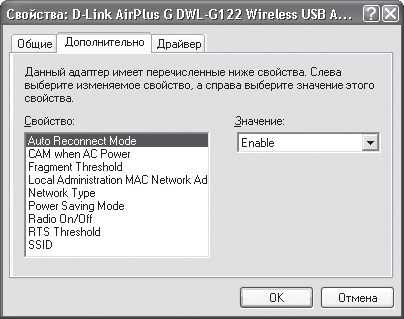
Rice. 15.22. Contents of the Advanced tab
Among the parameters that will probably have to be adjusted are the following.
Network Type - the mode in which the network will operate. Two parameter values are available: 802.11 Ad Hoc (Ad-Hoc mode) and Infrastructure (infrastructure mode).
SSID is a unique network identifier used to create a group of computers that can work together. The SSID can be any phrase or a set of numbers and letters. The main thing is that you can then repeat it when another wireless adapter, access point, router and other wireless equipment designed to work in a group is configured.
Using the "native" configuration mechanism
To configure your wireless adapter using the native utility, you need to make some additional changes.
Going to the Wireless networks tab, you need to uncheck the Use Windows to configure the network box (Fig. 15.23), after which the utility supplied with it will be used to configure the wireless adapter.
![]()
Rice. 15.23. Uncheck Use Windows to set up network
To check this, double-click the D icon in the notification area on the Taskbar - a setup program window will open containing five tabs. By default, the Link Info tab opens, containing information about the current connection: network mode, wireless standard used, current link speed, SSIDhap. (Fig. 15.24).
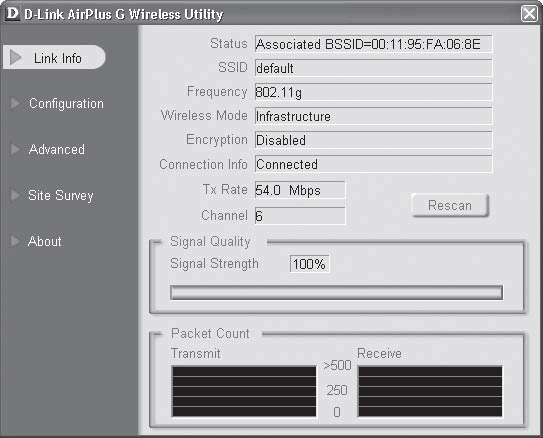
Rice. 15.24. Link Info tab
Device operation parameters are controlled on the Configuration and Advanced tabs. In addition, you can configure connection settings for all found access points on the Site Survey tab. Let's consider them more carefully.
If it is not clear which cipher type to choose, it is best to leave it to the access point itself and set the Cipher Type field to Auto.
If you do not plan a RADIUS server on your wireless network, but still want to use the capabilities of the WPA protocol, then select WPA-PSK as the Authentication parameter. In this case, it will also be necessary to determine the type of cipher and specify the encryption phrase.
Reducing transmitter powerAs you know, to transmit data on the air, each wireless device is equipped with a receiver and transmitter of radio waves. The radius of the wireless network depends on the power of the transmitter, and the quality of the signal reception depends on the sensitivity of the receiver. Since radio waves are an uncontrollable thing and you can never predict who can receive them, a good option to protect the network is to select such a transmitter power that is quite enough to cover all the devices on the network. This can cut off all ill-wishers who can “attach” to the network, for example, behind the wall of a neighboring house or in a car in the parking lot next to the office.
Another plus of such an enterprise is energy savings, which is critical for portable computers and devices.
To select the signal strength level, you need to run the access point configuration utility and go to the tab Wireless (Wireless network) (Fig. 15.34).
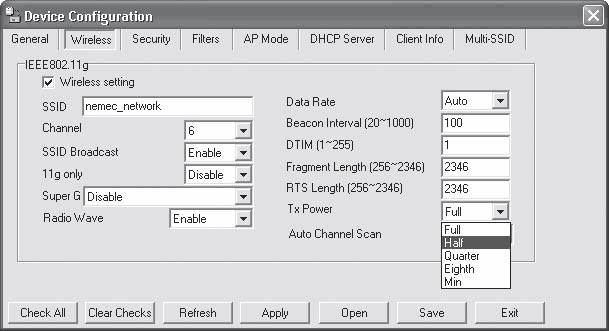
Rice. 15.34. Adjusting transmitter power
This tab contains the Tx Power (Signal Power) field, in which you can select the following values: Full (Full power), Half (Half power), Quarter (Quarter power), Eighth (Eighth of power) or Min (Minimum power).
It is not worth setting too low power immediately, as this can “cut off” the connection with some remote computers. Therefore, reduce the power gradually, but do not set the one at which the threshold operation of the device is observed, since under certain conditions the signal may weaken even more, which, again, will lead to the shutdown of some remote computers.
Chapter 16
Network setup in Windows XP
As practice has shown, the operating system Microsoft Windows XP is used much more often than other operating systems. Good security and fault tolerance, ease of use, great features and much more - all this is pleasant to users. Since this operating system is used for networking, you need to know and be able to install and configure protocols, services, etc. You should also be able to create shares, connect and use them.
Connect to a domain or workgroup
First of all, you need to configure the network settings, for which you need to use the information about the IP addressing in the network and the name (s) of the workgroup or domain.
To get started, set up a domain or working group, by right-clicking on the My Computer icon and selecting Properties from the menu that appears, the system properties window will open (Fig. 16.1), containing several tabs.
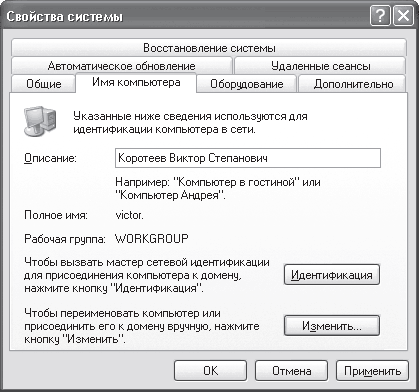
Rice. 16.1. Contents of the Computer Name tab
We are interested in the Computer name tab, where in the Description field you can change the description of the computer that will be displayed in the Explorer window next to the name of the computer on the network.
There are two ways to join a computer to a domain or workgroup: simple and complex. At the same time, a simple path is suitable for users who have already encountered this kind of action more than once. The complex path is replete with rather confusing steps and incomprehensible words, so novice users often prefer the simple setup path. On the other hand, if you already have all the necessary data for registering on the network, then it is better to choose the first option, since it is more understandable. On the Computer Name tab, you need to click the Change button - a window will open (Fig. 16.2), in which you will need to specify the necessary data.
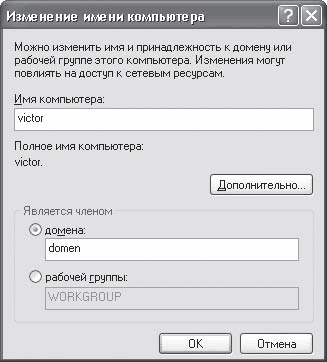
Rice. 16.2. Specify the name of the domain or group
For example, if the network has a domain, then you will need to indicate that the computer is a member of the domain, and enter the domain name. Otherwise, indicate that the computer belongs to a workgroup and specify the group name. However, first of all, if necessary, you should change the name of the computer under which it will be visible on the network.
If a domain system is used, then after pressing the OK button, a window will appear asking you to enter the login and password for accessing the user who has the right to connect to the domain (Fig. 16.3). This means that this user must already be registered in Active Directory. If you are not registered yet, then you can connect to the domain using any other account, for example, ask your network administrator for this service.
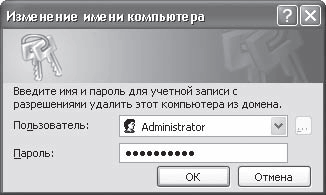
Rice. 16.3. Connecting to a domain
If the entered data is correct, then in a few seconds you will find yourself in the domain, as evidenced by the corresponding message (Fig. 16.4).
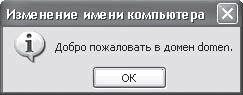
Rice. 16.4. Successfully connected to the network domain
If you are connecting to a workgroup, then no additional windows will appear, and as a result, a message will appear that you have connected to a group with the specified name.
To fully enter the domain or group, you need to restart the computer, which will be indicated by the inscription at the bottom of the window (see Fig. 16.1).
Protocol setup and ping
By setting up a connection to a domain or group, you thereby prepare the computer for joining a network workgroup, but nothing more. If the network has static addressing, then you will not be able to fully enter it and work. To do this, you will have to additionally configure the IP protocol.
First of all, you need to open the network connection properties window, for which you should right-click on the Network Places icon located on the Desktop and select Properties from the menu that appears - a window with a list of network connections will appear (Fig. 16.5).
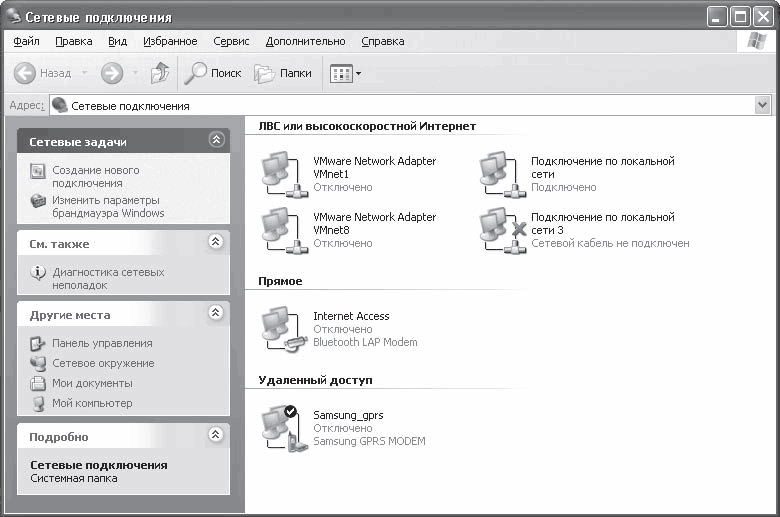
Rice. 16.5. List of network connections
Note
If there is no Network Neighborhood icon on the Desktop, then select Start > Control Panel and double-click the Network Connections icon in the window that opens.
The number of network connections may vary depending on how the computer was connected to the network or to another computer. For example, network connections are created automatically if a Bluetooth adapter is connected, Internet access via a modem is used, or a user connects to another computer using any type of connection. Therefore, do not be surprised if, when you open the Network Connections window, you see several network connections, including inactive ones.
Note
If no network devices were connected to the computer and no connections were made to other computers, then there will be only one network connection in the network connections window.
If you right-click on an active network connection and select the Properties item from the menu that appears, the properties window for this connection will open (Fig. 16.6).
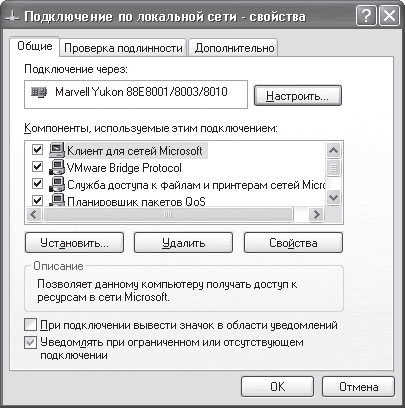
Rice. 16.6. Properties of the selected network connection
To configure the IP protocol, you need to find it (Internet Protocol (TCP / IP)) in the list among other protocols and connection services and double-click on it or click the Properties button - the protocol properties window will open (Fig. 16.7).
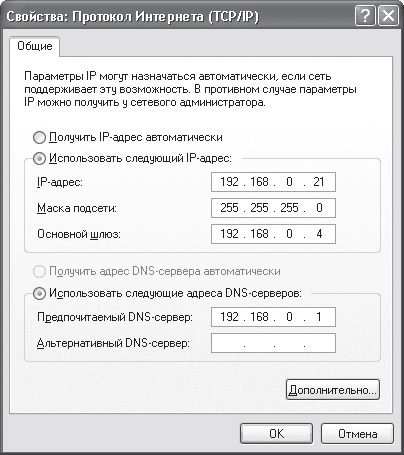
Rice. 16.7. Set up the IP address, subnet mask and other parameters
The IP address and Subnet mask fields are used to enter the IP address and subnet mask.
If a DNS server is configured on the network, then you need to set the switch to Use the following DNS server addresses and enter the IP address of the DNS server in the Preferred DNS server field.
If a DHCP server is configured on a network with a domain and addresses are issued automatically, then you must set the switch to Obtain an IP address automatically.
In principle, this protocol settings can be completed, since they are quite enough for normal operation on a local network. If required, you can also add the addresses of gateways (routers), if any, which will allow you to access network segments with different addressing. To do this, use the Advanced button and enter the required IP addresses using the Add button.
After connecting your computer to a network and configuring network settings, you may not be able to connect to it after you restart your computer. This could be caused by a network setup error or a physical network error such as a badly crimped cable, a broken cable, a bad port on a hub or switch, etc.
The easiest way to check the connection is to use the ping system utility.
First of all, you need to open the command prompt by running Start > All Programs > Accessories > Command line and typing the following in the line: ping 192.168.0.1 (Fig. 16.8).
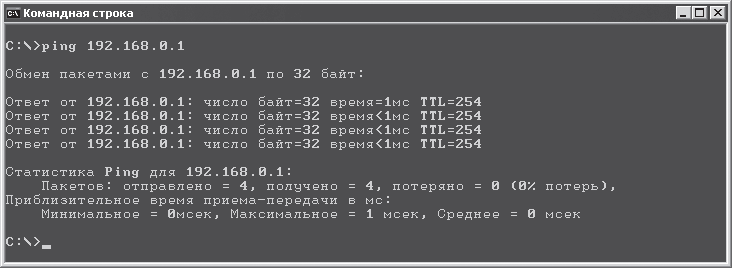
Rice. 16.8. Successful command execution
Attention!
The address in the example is the address of the network domain. You can also enter any other address that is used on your network, such as the address of the switch you are connected to.
If there is a physical connection to the specified address, that is, the cable is not damaged and the equipment is working, then the result will be positive. By default, the program sends only four packets to the specified IP address, which is quite enough to check the connection. In the presence of communication, the response time in this example is less than 1 ms. It is also possible that this indicator fluctuates over a wide range. This means that there is a connection, but it is far from being the most stable and fast, which, in turn, means that the segment length is too long or there are collisions in the network. In this case, you can try connecting the cable to a different port on the hub or switch.
If there is no connection with the specified device, then the result will be negative (Fig. 16.9).
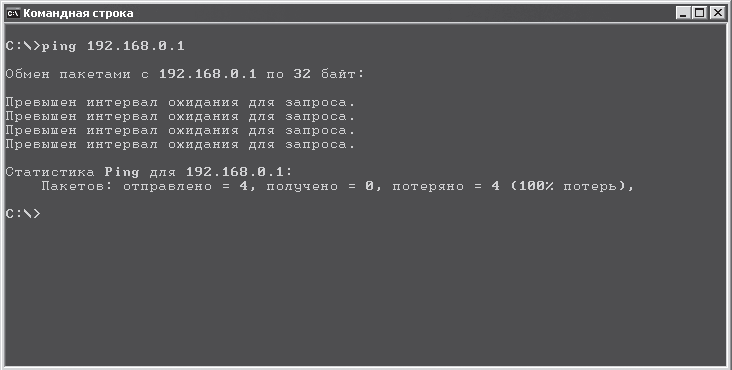
Rice. 16.9. Command failed
In this case, you need to check the following:
IP address;
subnet mask;
Working group or domain;
The correct installation of the network card (use the Device Manager);
If the network card is not integrated, then a pin in the slot with an adapter or a port (if a USB adapter is used);
Adapter performance (the link indicator on the rear panel should be on);
Correct crimping of connectors on the cable;
The status of all ports used to connect the computer.
Access to file resources
Regardless of what type of network you have - peer-to-peer or server-based network, sooner or later you will need to share some folders on your hard drive. Of course, if the network is server-based, then it is better to resort to the help of a file server. However, if you put necessary files the file server does not work or is impossible, then you will have to set up general access to the computer.
To make the computer's file resources publicly available, Windows XP has a special service that starts automatically when a network card is installed. All you need to know is how to correctly create a resource and configure access rights.
First of all, open an Explorer window. In the Windows XP system, sharing is set separately for each folder, so you need to immediately decide which folders you need to give to network users to be "torn to pieces".
Having selected the folder that you want to share, you need to right-click on it and select Sharing and Security from the menu that appears - a window containing several tabs will open.
To manage access, use the Access tab. Depending on whether you are connected to a domain or not, the contents of this tab may be different. Let's consider both cases.
Without using a domain(Fig. 16.10).
Rice. 16.10. Setting up access to a file resource on a network without a domain
You control network access using the Network Sharing and Security area. To share a folder, select the Share this folder check box. If the resource is to be mutable, be sure to select the Allow modification of files over the network check box. After pressing the 0K button, the operating system will begin to change the access rights to the folder, as evidenced by the appearance of a small window with animated content.
Using a domain(Fig. 16.11).
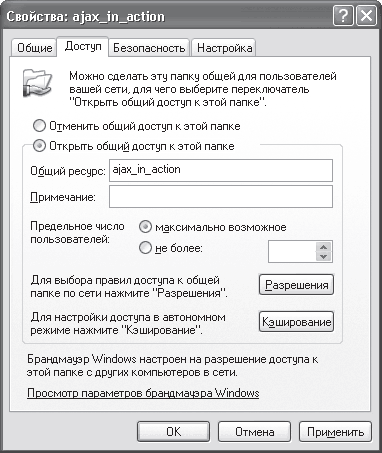
Rice. 16.11. Setting up access to a file resource on a network with a domain
On the Access tab, which is open by default, you need to set the radio button to Share this folder and specify access rights to this resource by clicking the Permissions button. By default, access to the folder is open to all users with the same rights - read only (Fig. 16.12).
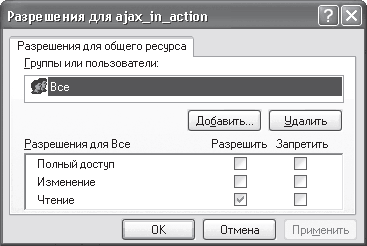
Rice. 16.12. List of users who have access to the resource
If this bothers you, then no further action is needed. If you want to configure different permissions for individual users, then click the Add button - a window for adding users from the domain will open (see Chapter 14, section "Configuring access to file resources", Fig. 14.29).
To cancel sharing a resource, in the windows for accessing file resources (see Figure 16.10 and Figure 16.11), uncheck the Share this folder option and set the switch to Cancel sharing this folder, respectively.
Similarly, you can set sharing on any number of folders.
Access to printers
Often someone needs to print information, but he does not have a printer at hand. If you are connected to a network and have a printer, then you can be a real lifesaver if you share it. Moreover, it is not difficult to do this. The main thing is not to overdo it with print permissions.
First of all, you should execute the Start> Control Panel command, click on the Printers and Faxes icon, right-click on the printer and select Sharing from the menu that appears (Fig. 16.13) - a window with several tabs will open.
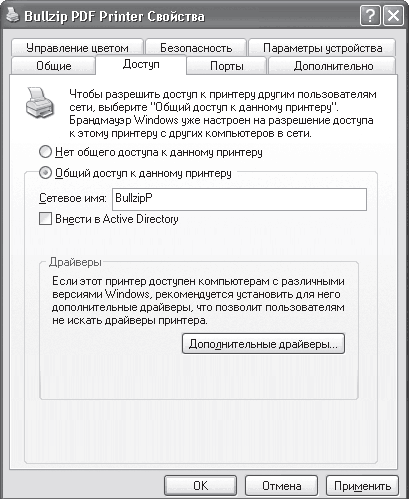
Rice. 16.13. Access tab in the printer properties window
To configure access to the printer, use the Access tab, the contents of which may also differ depending on whether you are connected to a domain.
So, if the domain system is not used, then it is enough to check the Share the printer box and specify its name.
If the network uses a domain, then you need to set the switch to the Share this printer position and enter the name under which this printer will be displayed in the network environment. In addition, here you can specify that the printer information should be added to Active Directory by selecting the Add to Active Directory check box.
Note
Information from Active Directory is sometimes required when connecting a network printer. However, the most commonly used option is a direct connection to a computer, so checking the Add to Active Directory box is not so important and critical.
If you need to configure access rights to the printer, then go to the Security tab.
By default, everyone can use the printer, with one limitation - users will not be able to manage other people's print jobs. You can also assign different rights to users by first adding them to the printer user group (for how to do this, see Chapter 14, section “Setting up access to file resources”).
This completes the printer sharing setup.
Let's say you recently found out that on your network - corporate, office or "home" - there is a computer on which there is a shared folder with a batch of new movies, and you really want to review them. So what's the deal?
Open File Explorer and select the Network Neighborhood option on the left side. Knowing the name of the desired computer, find it in the network environment and select it. In this case, in the right part of the Explorer window, all the resources that this computer gives to the public will be displayed.
Presumably the movie folder will be called Video. Right-click on it and select Connect from the menu that appears. network drive– a window for connecting a network drive will open (Fig. 16.14).
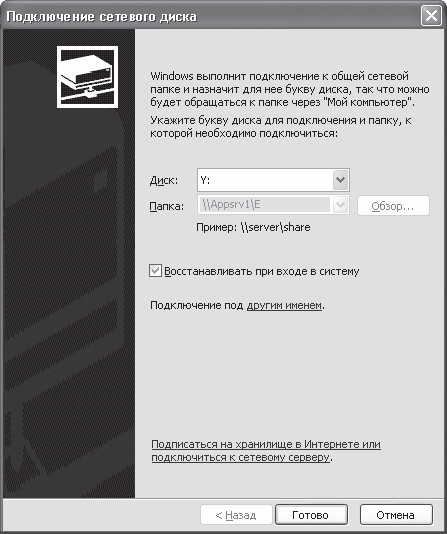
Rice. 16.14. Connecting a network drive
In this window, you are asked to select a drive letter under which the contents of the Video folder you have selected will be displayed. If you want this drive to be connected every time you log on to Windows, select the Restore at logon check box.
That's all - enjoy watching your favorite movies.
Connecting to a network printer
If you need to print some information, and the printer is not connected to the computer, then it is not necessary to run with a disk to a neighbor if a network is established between your computers. It is enough to connect his printer as a network one. Of course, provided that the neighboring printer is set to be shared (see the "Sharing Printers" section of this chapter above).
The easiest way to connect a network printer is as follows. Open Network Neighborhood in Explorer and place the mouse pointer on the computer that is accessing the printer. Then double-click on the printer on the right side of the Explorer window or right-click on the printer and select Connect from the menu that appears (Fig. 16.15).
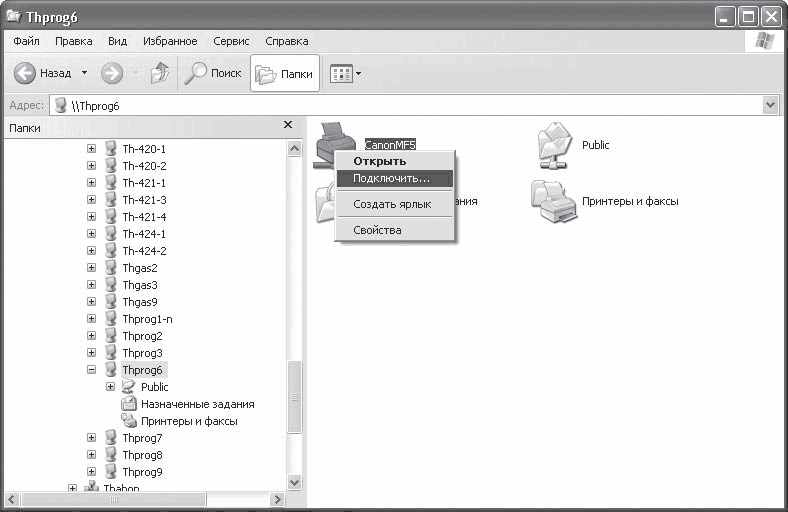
Rice. 16.15. Connecting a network printer
After that, the printer will be connected.
Chapter 17
Network setup in Windows Vista
Operating system Windows Vista begins to infiltrate users' computers, and it is no longer possible to stop it. Anyone who has enough powerful computer, even just for the sake of interest puts this system and tries to work with it. Those who have been using this system for a long time are used to it and are not going to part with it.
If you have an operating Windows system Vista in any version, then you need to know and be able to connect a computer to a network and learn how to use shared resources and share your resources.
Network connection and protocol setting
It is worth saying that as soon as you connect to a computer network cable and turn on the computer, Vista immediately detects the network and saves information about it. However, she will not want to connect to it right away and will offer to go through a certain connection path. Now about everything in order.
First of all, execute the Start > Control Panel command, find the Network and Internet icon and follow the link View network status and tasks - a window will open (Fig. 17.1), which displays the current connection status to the found network. There are also mechanisms for configuring access to computer file resources and its printers.
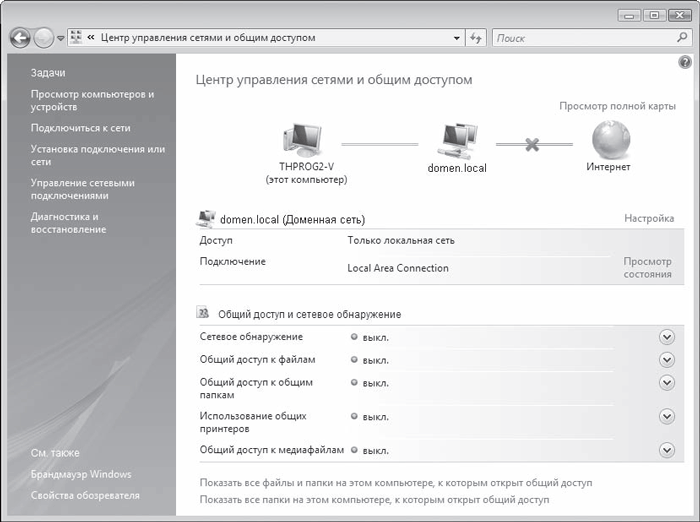
Rice. 17.1. Network and Sharing Center
The next step is to configure the IP protocol by specifying the computer's IP address, subnet mask, DNS server IP address, etc. Of course, if you are using a network with dynamic address assignment, then such a configuration may not be necessary.
If you still need the setting, then in order to change the specified settings, you need to follow the link Manage network connections - a window with a list of network connections will open.
By clicking on the required connection with the right mouse button, select the Properties item in the menu that appears - the properties window of the selected network connection will open (Fig. 17.2).
Rice. 17.2. Properties of the selected network connection
Unlike a similar window in Windows XP, this window contains many more protocols and services, but this does not change things.
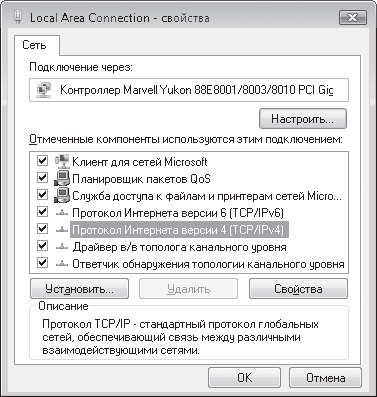
We will be interested in the Internet Protocol Version 4 (TCP/lpv4) position, double-clicking on which will open the IP protocol settings window (Fig. 17.3). Having on hand all the necessary data, we enter them in the appropriate positions.
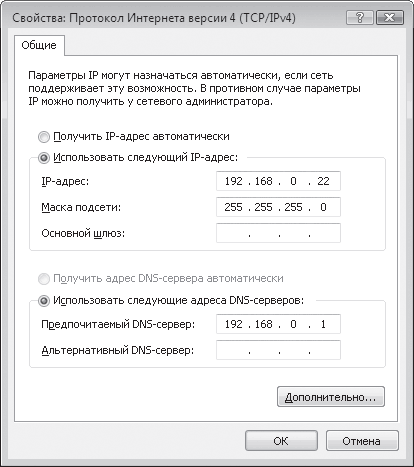
Rice. 17.3. Enter the required data
After entering the information and clicking OK, you will be able to fully join the domain or workgroup.
Setting up network discovery
Even though the network connection is already set up, you still won't be able to see the computers on the network. To make this possible, you must additionally configure the network environment.
Need to go back to dialog box Network and Sharing Management (see Figure 17.1) and click the arrow button next to Sharing and Network Discovery - this item will expand and two options will appear. To allow the computer to see other machines on the network and, in turn, to allow itself to be seen, set the radio button to Enable network discovery (Figure 17.4) and click the Apply button. The service will start its work, which will be indicated by the green indicator on. opposite the inscription Network discovery.
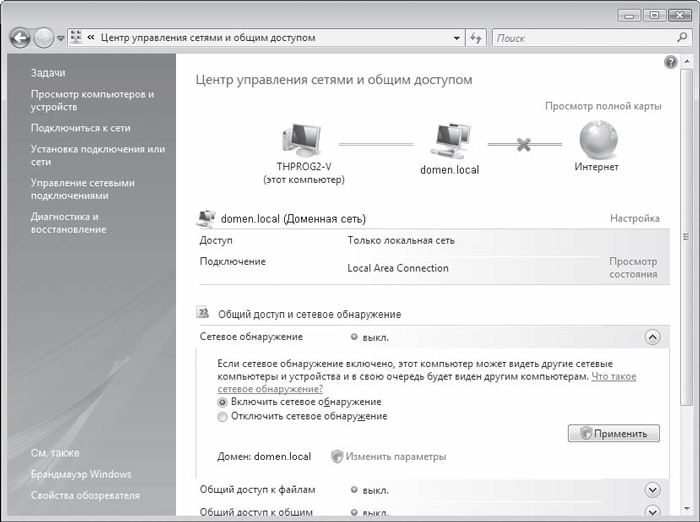
Rice. 17.4. Activate the network discovery service
This completes the network setup.
If, after setting up the operating network, you cannot get into the network, then it means that you entered incorrect data when setting up the protocol or there is some kind of physical damage.
Connection with a server or other network device is checked in the same way as in the Windows XP operating system (see Chapter 16, section "Protocol Configuration and Communication Check").
Configuring access to file resources
By default, even if you are already connected to the network, the ability to access your resources is blocked, which is done for the sake of increased system security.
To share a file share, you must do the following:
Run the command Start > Control Panel > Network and Internet > Network and Sharing Center - a window will open (Fig. 17.5), in which you should click the arrow button opposite the File Sharing inscription.
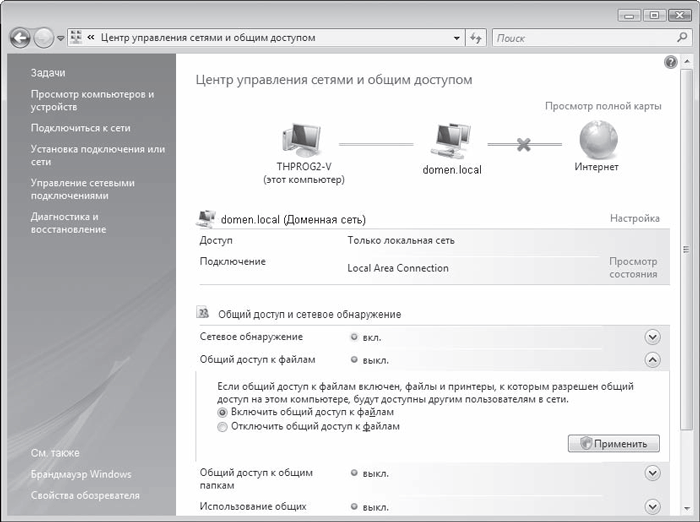
Rice. 17.5. Set up file sharing
As a result, the required section will expand, resulting in the appearance of two parameters. To activate the file sharing function, you need to set the switch to the Enable file sharing position and click the Apply button - this function is activated, as indicated by the green light next to File Sharing.
Let's look at how to set up shared access to a specific folder.
Using Explorer, find the folder that you plan to share. By clicking on it with the right mouse button, in the menu that appears, select the Sharing item - a window will open (Fig. 17.6), which displays users and groups that have access to your resource.
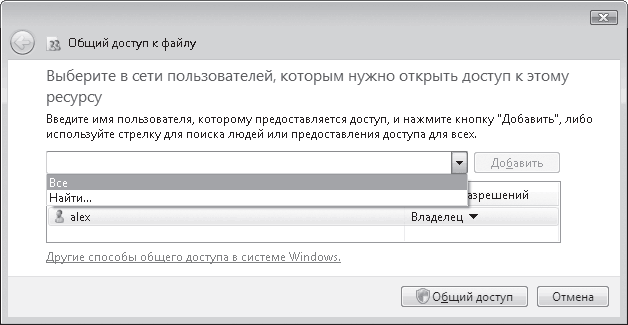
Rice. 17.6. Adding access rights
By default, no one except the owner of the computer has access, but this is very easy to fix. For example, when you open the list, you can select the Everyone group, which will allow everyone to see your access. Use the Add button to add this group to the list.
It is not clear why, but the creators of Windows Vista do not allow you to set rights in this window more clearly than by choosing one of the access options: Reader, Contributor or Co-owner. However, this can be done later. By default, a group or user is added with Reader permissions. If you already know in more detail what each of the options means, then you can change the access rights right here by right-clicking on a group or user.
After clicking the Share button, the system will perform some manipulations, as a result of which the shared access to the folder will be opened, as reported by the window that appears (Fig. 17.7).
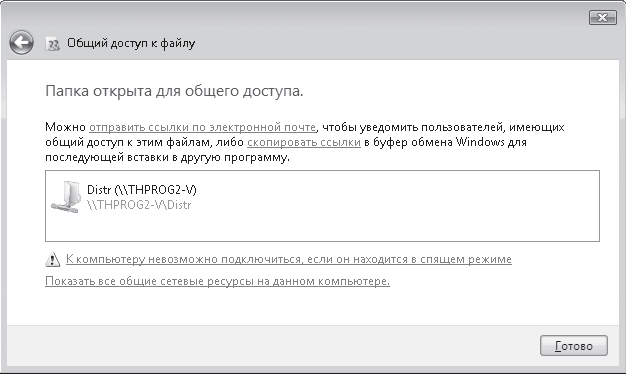
Rice. 17.7. Folder is shared
If you need to configure the rights of some users more precisely, then you need to use the Explorer again by right-clicking on desired folder and selecting the Properties item in the menu that appears, a window will open in which you should click the Additional access button (Fig. 17.8).
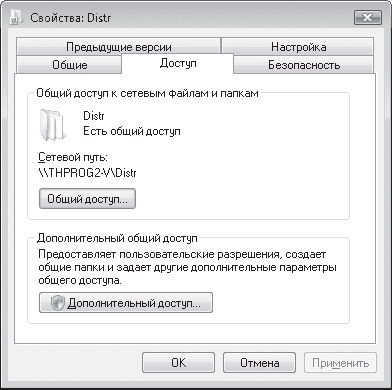
Rice. 17.8. Setting up additional access
As a result, a window will appear (Fig. 17.9), in which you can configure permissions for each of the users and groups that are allowed access to this folder.
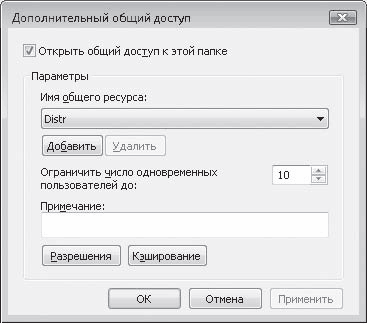
Rice. 17.9. Setting Access Permissions
Before configuring these rights, note that you can limit the number of simultaneous connections. This setting will come in handy when you see a noticeable slowdown in your computer, which means a resource is being abused. In this case, simply reduce the number of simultaneous connections to a minimum, for example, to two or three people.
To configure permissions for specific users or groups, use the Permissions button - a window will open (Fig. 17.10) containing a list of all users who are allowed access to this resource.
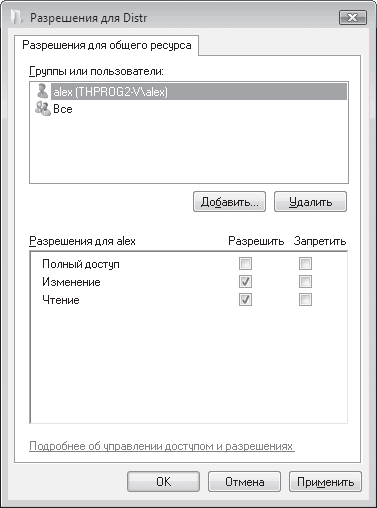
Rice. 17.10. Set permissions for each position
To add new users, click the Add button. For the process of adding users, see Chapter 14, section "Configuring Access to File Resources".
Disable access to shared folder possible in several ways. For example, uncheck the Share this folder box (see Figure 17.9) or click the Share button (see Figure 17.8) - a sharing window will open (Figure 17.11), in which you will need to select the Stop access option.
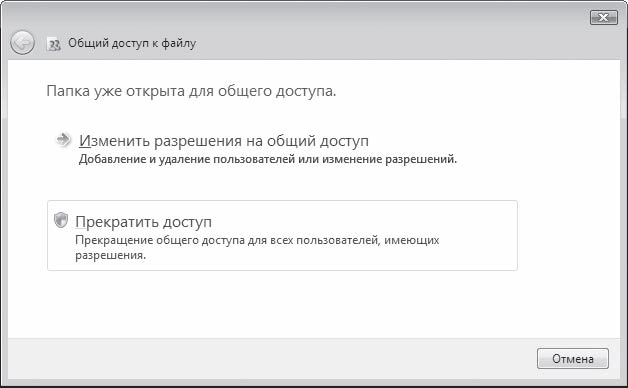
Rice. 17.11. Disable folder access
Configuring access to printers
As with file shares, printer sharing is also a two-step process. First of all, you need to activate the corresponding feature and only then add the rights to use the printer.
Run Start > Control Panel > Network and Internet > Network and Sharing Center. A window will open (Fig. 17.12), in which you need to click the button with the arrow next to the inscription Usage shared printers, set the radio button to Turn on printer sharing, and then click Apply.
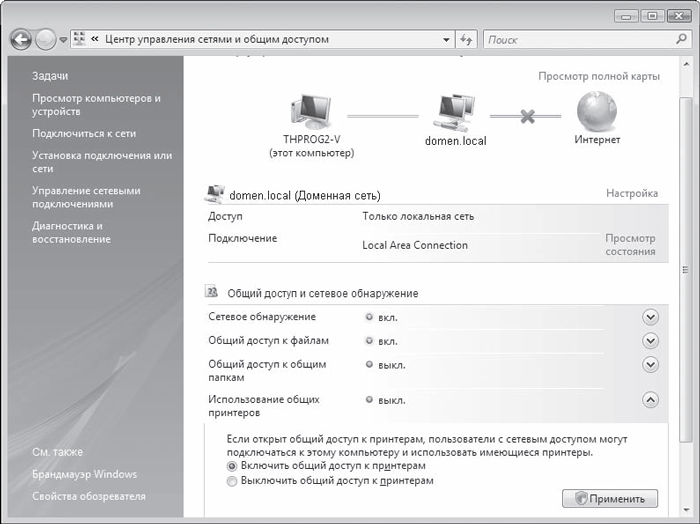
Rice. 17.12. Allow Printer Sharing
The system will execute necessary settings and activates printer sharing, as indicated by the green light next to Printer Sharing.
The next step is to set permissions. To do this, open the Printers group, right-click on the desired printer and select the Sharing item in the menu that appears (Fig. 17.13).
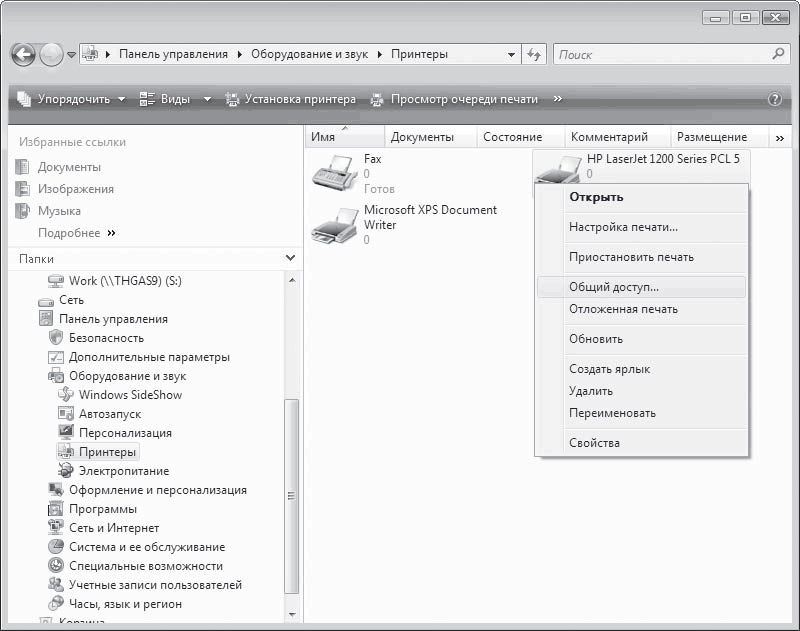
Rice. 17.13. Select the Sharing option
As a result, a window with printer settings will appear (Fig. 17.14), opened on the Access tab. If the computer is not connected to a domain, then the contents of this tab are blocked and become available only after clicking the Sharing settings button. After using this button, you can change network name printer.
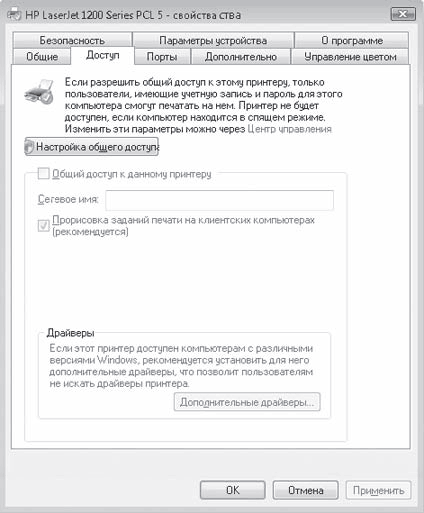
Rice. 17.14. Printer settings window
If the computer is connected to a domain, then the contents of the tab are active and the necessary changes can be made immediately.
On the Security tab, you can add or remove users who can use the printer, as well as configure their rights (Fig. 17.15).
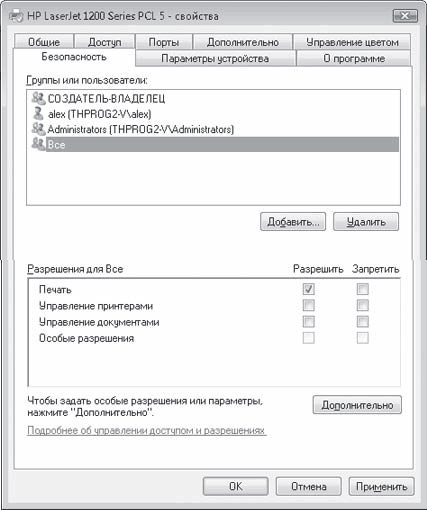
Rice. 17.15. Setting up user and group rights
To configure the rights, it is enough to check or uncheck the corresponding checkboxes located at the bottom of this tab. To add users, use the Add button (for the process of adding users, see Chapter 14, section "Setting up access to file resources").
Connecting to a file share
The process of connecting to a file share is very simple and has several options. Most often, Explorer is used for this.
So, if you need to temporarily connect to network folder to open a file or rewrite a movie, it is enough to open the Network group on the left side of the Explorer and mark the desired computer. In the right part of this window, select the desired object and simply drag it using the mouse button and holding down the Alt key.
If you plan to use this file resource all the time, then it will be easier to connect it as a network drive so that you do not have to look for this computer and data on it every time.
You should right-click on the desired folder and select Map network drive from the menu that appears (Fig. 17.16).
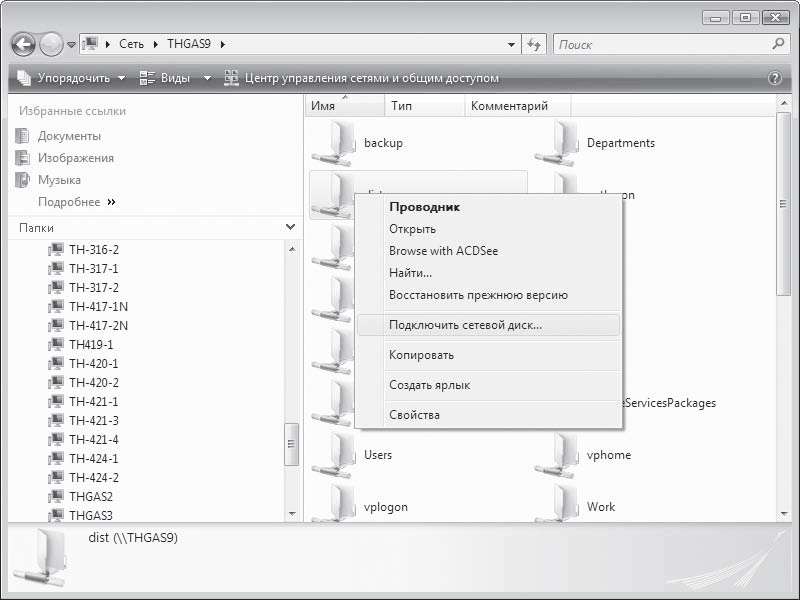
Rice. 17.16. Select Map network drive
As a result, a window will open where you need to specify the drive letter that will be used to connect the network resource (Fig. 17.17). In addition, to permanently automatically mount the drive at logon, select the Restore at logon check box.
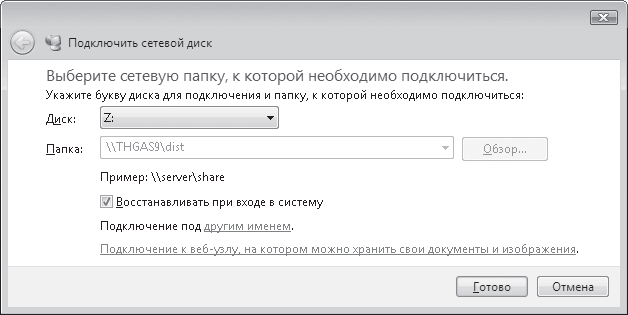
Rice. 17.17. Specify network drive connection options
Connecting to a Printer
network printer in the operating system Windows Vista is connected in the same way as in Windows versions XP.
You need to open Explorer, right-click on the printer and in the menu that appears, click the Connect button or double-click on the printer image.
Since the proportion of computers on the network with Windows Vista installed is still too small, you may need to manually install printer drivers to connect the printer. You will have to look for a printer driver for Windows Vista.
Chapter 18
Connecting your network to the Internet
Connecting a local network to the Internet is a matter of time, and, as a rule, this time comes very quickly. The fact is that the main and main source of new information is the Internet, so connecting it to a local network is absolutely justified. In addition, almost all "home" networks are created precisely in order to charge for the use of the Internet in the first place, and only in the second - for everything else.
The Internet is a network - the Global Network, which began with the connection of several computers, and ended with millions and ended with the pinnacle of network development success, therefore, to consider its organization and capabilities is one of the mandatory tasks of this book.
A little about the Internet
What is the Internet? More than two decades ago, work began on the creation of an experimental ARPAnet network. The idea came from the US Department of Defense. The main task that was set before the developers was to achieve network resilience to any damage.
At that time, there was a "cold war" between the United States and the Soviet Union, which at any moment could develop into a third world war. Considering that aerial bombardment can affect and destroy vast industrial (and not only) areas, the network being developed by the researchers was supposed to ensure uninterrupted operation. It was supposed to achieve this by keeping at least one of the computers working, which could be connected using another computer.
Communicating computers (not just the network itself) were also given the responsibility of ensuring that communications were established and maintained. The basic principle was that any computer could communicate with another as an equal to an equal. The International Organization for Standardization (ISO) has taken up the development of a standard for such a network.
The idea of the network was clear, and everyone, including many of the computer hobbyists, began to develop it, which was possible due to the long delays in the adoption of the standard. Gradually software, which served the network, was improved and distributed. It has been used by many users. Gradually the network was taken under control and everything became highly standardized.
A little later, the World Wide Web (WWW) appeared - “ The World Wide Web”, and everyone rushed to conquer the Internet.
Countless variety of resources has turned the Internet into an information mechanism of unprecedented power. The prospects for its development are unforeseen, which is even more attractive.
The Internet is integrating into life at a rapid pace and sooner or later it will reach 100 percent.
To become a member of the club of Internet lovers, you need very little - desire and money. The global network is such a well-oiled mechanism that even an inexperienced user can work in it. Why not try it and you might like it?
Internet access options
To use the Internet, you need to connect to it, that is, access it. To do this, you will have to conclude an agreement with one of the providers (an organization that has direct access to the Network).
Providers are primary and secondary.
Primary providers - large organizations with high-speed terrestrial or satellite channel on the Internet, which allows you to receive and transmit data at a speed much higher than the speed of a conventional modem, for example, more than 100 Mbps. Only large companies that have one or more servers serving their websites and databases can afford access to such a channel.
Secondary providers - as a rule, small organizations that have concluded a contract for the lease of a channel from the primary provider to them. The speed of such a channel depends on the level and quality of equipment owned by the secondary provider. As a rule, it does not exceed 10 Mbps. Access to a secondary provider's channel is usually several times cheaper than access to a primary provider's channel. This is due to the fact that the channel speed is quickly consumed due to the large number of connections and, as a rule, an ordinary user gets a channel with a speed of up to 1–2 Mbps.
Today, the most popular options for connecting to the Internet are:
Using an analog-to-digital modem;
Using an xDSL modem;
Through a dedicated line;
Via frame relay
Via wireless modem;
Across cable TV.
Since sooner or later a local area network, no matter how large, will have to be connected to the Internet, it is worth at least briefly considering each of these options.
Connecting with an analog-to-digital modemAs follows from of this type connections, to connect to the Internet, that is, to an Internet provider, a conventional analog-digital modem is used, which has already appeared a dozen years ago. For more information on modems, see Chapter 6, Modem section.
Once upon a time, this connection method was the most profitable and simple - it was enough to purchase a modem, configure the connection properties - and you were already on the Internet. Today, this method is also common, but it is already beginning to lose ground.
To connect to an Internet provider, a telephone cable available in every home is used, designed to communicate via telephone. To receive your signal, the provider is forced to keep a similar modem on its side, which, at the same time, is designed, roughly speaking, for a point-to-point connection (which is why the name “session connection method” or dial-up access is often found). This means that in order to serve hundreds of users at the same time, the provider has to have at its disposal a hundred lines and a hundred modems (modem pools). However, this is not the worst. The main disadvantage of connecting via a modem is the low speed, which, with today's methods of designing resources on the Internet, does not provide a good display speed. In addition, you don’t even have to think about watching live video, listening to Internet radio, chatting through a webcam, using an Internet pager, etc.
As mentioned earlier, the theoretical speed of such a connection is no more than 56 Kbps. However, this connection method is often used when the existing analog telephone line does not allow the use of more advanced data transfer technologies.
The organization of Internet access using an analog-digital modem is only suitable for a local network with two or three computers, no more, otherwise you will only get an adrenaline rush from indignation at the low speed.
Connecting with an xDSL modemAs in the case of analog-digital modems, an ordinary telephone line is used to organize Internet access using an xDSL modem. However, thanks to a completely different signal transmission technology, the data transfer rate is much higher than the speed achieved with a conventional analog-to-digital modem. So, most often, for example, at home, speeds from 64 Kbps to 512 Kbps are used. In this case, it is possible to regulate the speed within a fairly wide range, and in both directions, that is, for the transmission and reception of information.
Today, ADSL modems are most widely used, the main advantage of which is high data transfer speed and a telephone line that is free to use. Thus, the maximum data reception rate for ADSL 2+ modems is 24 Mbps, which, you see, is enough for any needs. Even if the speed is only 1 Mbps, you can already easily listen to the radio, watch movies and exchange information with high speed for a short time.
Using an xDSL modem to organize Internet access is often practiced in local area networks at the level of an enterprise or a large office. Nothing prevents them from being used in "home" networks, however, as practice has shown, in this case other options are used, for example, a leased line.
Connection via leased lineA leased line, no matter what type it is - telephone cable or fiber optic, allows you to connect directly to the provider's equipment, so you can be sure that the line is used in full and only by a specific user.
The data transfer rate depends on the equipment used. If optical fiber is used as a carrier, then nothing prevents data from being exchanged at a speed of 10-100 Mbps.
The disadvantage of connecting using a leased line is the high cost, which makes its use possible only for enterprises and large organizations. Nevertheless, a leased line is very often used in "home" networks, as it allows you to get guaranteed access to the Internet, regardless of many conditions.
Connection via frame relayConnection using frame relay (approximate translation - "variable structure") has been used for a long time. The main point of such a connection is a dynamic change in speed depending on the needs of users, that is, the minimum data transfer rate is initially determined, which then automatically changes depending on the conditions. The maximum data rate can be approximately 2 Mbps, depending on the quality of the line.
A similar connection method is often used in enterprises to organize communication with remote sites. This method is not always suitable for accessing the Internet. So, in the case of "home" networks, the line load will almost always be 100%. Therefore, it is more profitable to take a dedicated line with a certain data transfer rate: albeit more expensive, but better.
Connecting via a wireless modemRecently, the use of radio air for data transmission has been practiced more and more often. The advantages are obvious: a fairly high speed and, most importantly, mobility.
To connect to the Internet, it is enough to install a directional antenna and a radio modem by connecting it to the router. The data transmission/reception speed can be quite high, for example 2 Mbps. However, it may fluctuate, as it is directly dependent on the distance to the provider and weather conditions.
Also, do not forget about the satellite Internet, as it also involves the use of radio, only at much higher frequencies. Connecting to the Internet via satellite has a number of features that do not allow it to gain great popularity. The first and most important drawback is the high cost of such a connection, since to use such an Internet you will need to purchase an expensive satellite dish and a special modem. There are symmetrical and asymmetric satellite Internet.
The first of these involves the use of cheaper equipment, but also requires an additional terrestrial Internet connection. This is due to the fact that simple satellite antenna It only allows you to receive data, and another type of communication is needed to transmit information.
The asymmetric Internet is free of such a disadvantage, but the cost satellite equipment in this case exceeds all reasonable limits. Nevertheless, the use of an asymmetric Internet is the only way to connect remote and cut off from civilization villages to the Internet.
Another disadvantage satellite internet- too long response time. This means that even if you have a connection with a speed of, for example, 2 Mbps, you receive information with a delay.
Another wireless connection option is to use existing GSM networks, that is, networks that serve mobile phones. In this case, simply connect mobile phone by any available means to the computer (cable, infrared port, Bluetooth), set up the connection in a certain way and use its modem to access the Internet. At the same time, the data transfer speed does not stand up to criticism, therefore, such a stationary method of connecting to the Internet is used quite rarely.
Consider using wireless technology to connect your local area network to the Internet wisely, and only if you are not satisfied with other connection options.
Connection via cable TVAnother booming way to connect to the Internet is using existing television cable systems. A TV is a device that is in almost every home, and very often cable TV is used to watch programs. Its advantages are obvious: a large number of programs for every taste and for every viewer.
Using an existing television cable to transfer data from the Internet is quite tempting and effective, since it does not require the organization of separate wire lines. The data transfer rate is quite high and can reach 30 Mbps. However, the use cable connection justified only at home, and for organizing Internet access for a local network, even a small size, this method is absolutely not suitable.
Sharing the Internet
There are several well-established mechanisms by which you can connect a local network to the Internet.
The general idea of connecting a network to the Internet is simple. It is enough to organize the connection of one of the computers and teach it to "share" this connection with other users. Using a computer for these purposes is quite convenient, as it allows you to adjust the permissions visually.
Also, for these purposes, you can use a router with a modem connected to it, which is more profitable, since it eliminates an extra “weak link”.
The implementation of this idea is complicated only by the fact that you need to organize control over the use of the Internet by other computers and monitor the security of their connection.
For an office network consisting of more than 20 computers, a separate computer is usually set up - an Internet gateway to which a high-speed modem is connected, the necessary software is installed, and which is intended only to serve users connected to it.
If it is impossible to allocate a separate computer, then any other used one can be used. Of course, in this case, some additional requirements must be imposed on it - at least it must be constantly turned on, not to mention the fact that it is necessary to exclude the situation of "hanging".
Using standard Windows components XPLet's consider how to organize general Internet access using the capabilities of the Microsoft Windows XP Professional operating system. This situation is common in small offices and small home networks. To share the Internet, a special Internet connection sharing service is used, called ICS (Internet Connection Sharing).
To carry out the plan, the computer that will act as the main one must already have a configured Internet connection of any type, through which general access to the Global Network will be organized.
Attention!
Use standard means to organize general access to the Internet when the computer is on a local network with a domain, it is impossible. This means that additional software will have to be used to implement the plan.
Let's choose the easiest way - we use the network setup wizard, to launch which you need to open the Network connections window (to do this, select the Start > Network Places command and click on the Show network connections link) and click on the Install link home network or small office network.
As a result, a window will open that tells you what you can use the Network Setup Wizard for (Fig. 18.1), including, for example, organizing a general connection to the Internet.
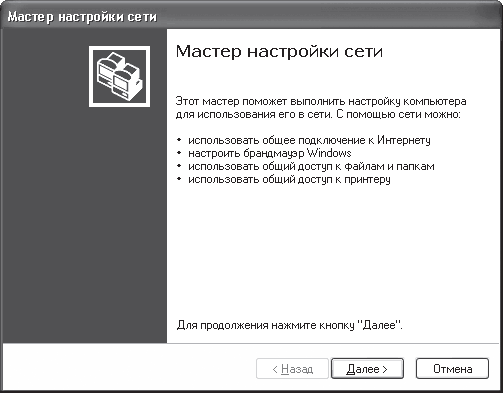
Rice. 18.1. Network Setup Wizard
After clicking the Next button, the following window will open, which provides tips for preparing in advance for the selected actions. In particular, it is suggested to check if the network card and modem are installed and working. It is also recommended that you connect to the Internet, which is not necessary, as you can do this later to check the sharing result.
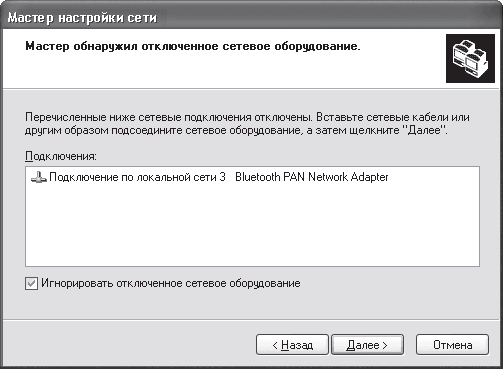
Rice. 18.2. Network connection detected
In this example, there is one wired network connection that is temporarily down because the network card is not connected to the network. This is done to test the master. As you can see, he found the connection and asked to check it or connect the cord, which can be done later by creating a share, so check the box Ignore disconnected network equipment.
If there were more than one connection in the list, the wizard would offer to select one of them, which will be responsible for connecting the computer to the local network. In the next window, the wizard will prompt you to select a connection method (Fig. 18.3).
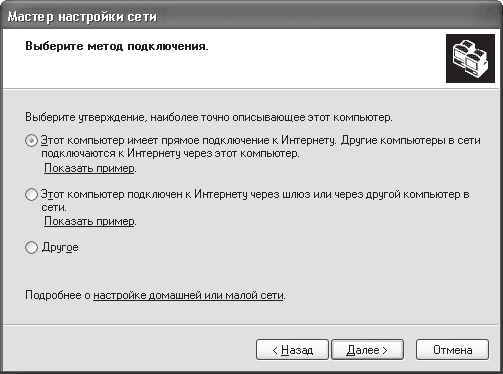
Rice. 18.3. Choose a connection method
There are several possible options depending on what needs to be configured. If you want to make this computer responsible for connecting to the Internet and provide other access to the global network through it, then you should select the first option: This computer has a direct connection to the Internet. Other computers on the network connect to the Internet through this computer.
If there is already a computer on the network with Internet access and it has already been configured for public access, then you need to select the second option: This computer is connected to the Internet through a gateway or through another computer on the network.
The third option is a more difficult path, so it will not be considered in this book.
Let's say you chose the first option. In this case, the next window will prompt you to specify the connection responsible for communicating with the Internet (Fig. 18.4).
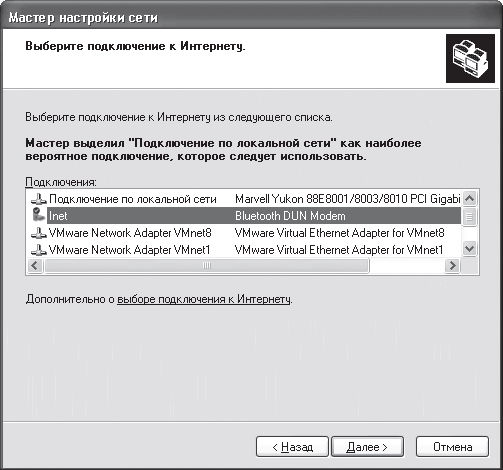
Rice. 18.4. Choose a connection
After selecting the connection and clicking Next, the following window will open, in which you need to specify the computer name and description. If you need to make changes to the previous selection, use the Back button.
In the next window you will be asked to name the group and add a description this computer. For computers to be able to access the Internet, they must belong to the same group as the computer with Internet Sharing configured.
As a group name, you can use the current name of the group in which the computer is located, or give a new one.
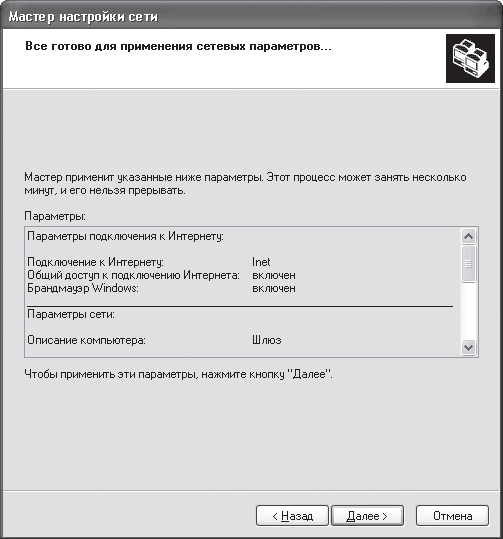
Rice. 18.5. Result Information
After the settings are completed, a window will open (Fig. 18.6), in which you need to select the last item. To configure other computers, that is, to include them in the created group, they also use the Network Configuration Wizard.
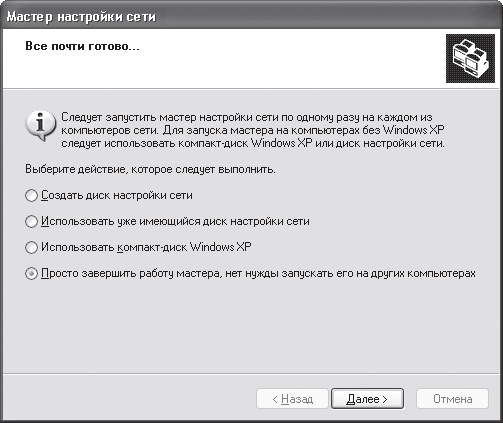
Rice. 18.6. Completing the wizard
In order for other computers to connect to the Internet, they will need to configure the IP protocol a little. So, you need to register the IP address of the gateway, which in our case looks like 192.168.0.1. For more details on protocol setup, see Chapter 16, section “Protocol Setup and Ping”.
Using Kerio WinRouteUsing ancillary programs to share the Internet is a smart move. Its main advantage is manageability and control. In addition, such programs contain all the necessary mechanisms to ensure the functioning of public access to the Internet. Kerio WinRoute is one such program.
Before installing this program, you should understand that in order to separate the traffic of the local network and the Internet, you must have a configured connection to the Internet. As a rule, this applies to both office and "home" networks; an additional network card is used to create such a connection. Although it is quite possible that any type of modem will be used. When installing the program, you will need to specify the device that is used to access the Internet, otherwise the traffic will be calculated incorrectly.
The program is not large, but nevertheless combines powerful mechanisms for Internet sharing and maximum control. Using only one IP address (NAT mechanism) to access the Internet makes the rest of the clients as secure as possible. In addition, there is a mechanism with which you can configure rules of a different nature.
After starting the program, you need to make minimal settings so that the whole mechanism starts working. The fact is that WinRoute is initially configured, and the required changes relate only to specifying the desired network connection, a list of allowed protocols, and a list of users with passwords.
Over time, with the advent of new connections and new nuances, it may be necessary to configure the built-in DHCP and DNS mechanisms, although this is not necessary.
The number of parameters of the program is simply amazing. You can set up a variety of filters, block or allow execution software modules, limit speed, configure routing tables, traffic usage rules and much more. All parameters are divided into groups, interconnected in the form of a tree structure in the left part of the program window (Fig. 18.7).
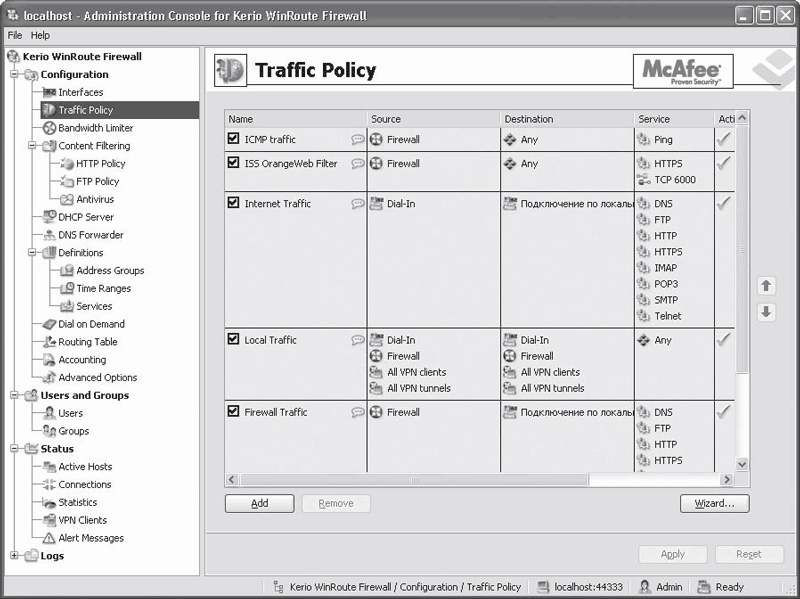
Rice. 18.7. Kerio WinRoute interface
The advantage of WinRoute over other similar programs is the presence of a built-in firewall and McAfee anti-virus protection. There is also the most detailed traffic usage statistics, available both in the program interface itself (Status branch), and called using the browser.
Setting client computers consists in prescribing the proxy server address in the IP protocol settings (in the Default gateway field).
If you want to make easy billing of users, then be sure to add them all and assign them a static IP address. In this case, no user authorization is required. If a DHCP server is configured on the network and addresses are issued dynamically, then users will be authorized every time they try to load any web page.
