Federal Agency for Education of the Russian Federation
Branch of the Saratov State Technical University in Petrovsk
Course work
By discipline: "Technology of software product development"
Theme: Development information system"cargo transportation"
Completed by: 3rd year student
Specialties 230105.51
The heart of a company's information and communication processes is usually an outdated mainframe computer system, which is usually accessible via the Internet. Access is secured by passwords or a virtual private network with various levels of security.
Overview of the best software systems in the field of cargo transportation and logistics
Suggested reference: "2 Freight Information System Technologies". Transport Research Council and National Research Council. Cybersecurity of Cargo Information Systems: Scoping Study - Special Report 274. The use of digital certificates and signatures has done long haul to solve the wide-ranging problem of software authentication. Digital certificates and signatures are often used in conjunction with hardware devices such as smart cards and smart tokens to further strengthen the authentication scheme used by the system.
« Software computing and automated systems»
Shikhin Gleb
Checked by: teacher
Trubkina Yu.A.
Petrovsk 2010
| Introduction I. Terms of Reference 2.Implementation of research work 2.1. Define input and output data structures 2.2. Requirements for the composition and parameters technical means PC Historically, the main interface between the real world and cyberdrive has been human: someone interprets real actions and enters data into a computer system, or someone receives a task from a computer and does day-to-day work. Embedded processors transfer information directly between the real world and the cyber world. Examples of embedded processors are RFID tags, electronic sensors, and electronic seals along with their electronic readers at all relevant points. These tags can be active or passive. Electronic sensors use embedded processors to detect and document environmental performance or changes in shipping along a route. For example, temperature sensors can be used on refrigerated containers to determine if the internal temperature has been maintained within the proper limits along the entire route. 2.3. Requirements for information and software compatibility II.Economic project. Explanatory note 1. Rationale for the need to develop an application 2. Setting a task for development, description of solution methods 2.1.Database structure 2.2.Diagrams 2.2.1. Diagram of sequence options 2.2.2 Sequence diagram Some types of sensors have been used for some time in various applications in the transportation sector, but are now somewhat integrated with embedded processors. For example, an electronic temperature sensor can record the actual temperature of the cargo along the entire route, and the temperature data can be stored in order of opening, using various hardware and software methods. Seals, whether electronic or mechanical, are placed on shipments or facilities to detect tampering or deter intrusions for fear of detection. They can be designed for different applications. For example, electronic seals on a container door may store information about the container, a declaration of its contents, and an intended route through the system. In combination with digital certificates and signatures, the electronic seal can also document whether the container was allowed to be closed and opened by persons. 2.2.3 Action diagram 2.2.4.Diagram 2.3 Instructions for the user 3. Description and justification for the choice of the composition of technical and software tools Brief characteristics of the operating room Windows systems XP Conclusion Bibliography |
Introduction
Theme of my term paper Development of the information system "Cargo transportation". Technological delivery operations, both necessary, due to economic relations, and unnecessary, can be carried out in time exceeding the normative ones and, in addition, using adjacent elements (warehouses, transport, mechanization of cargo operations, etc.) according to their technical and economic characteristics (productivity, cost, etc.) different from the planned ones.
Junction points can increase cyber resilience. A full assessment of the potential cybersecurity vulnerability that will be created by the widespread adoption of these technologies in the freight transport industry is needed, perhaps as part of a larger study that is the focus of this report.
Cryptography has been used in various applications for over 25 years to enable the exchange of information between two entities over a network. Cryptography is the basis for most "secure" web activities and "secure" applications. Email, and is supported by all major software applications. The need for strong cryptographic techniques in e-commerce has led to its widespread adoption outside of traditional military applications.
An assessment of the economic efficiency of container service for production, transport and storage systems should be carried out on the basis of comparisons the cost of delivering products prior to the implementation of the container system and the results obtained by the serviced system after the implementation of the container system.
Biometric devices are used to authenticate people based on one or more physical attributes such as retina or iris pattern, fingerprint, digital face recognition, or voice pattern. So it restricts access to a specific person, not just someone who knows certain information or holds certain credentials.
Tracking systems wireless communication are used in the inland transport sector to track the location of shipments along their route. In some cases, the shipment sends its location wirelessly to the control system, while in other cases the shipment simply records its location along its route and this data is collected at the checkpoint.
In accordance with the economic essence of the processes of functioning of container systems, the main arguments that form their economic efficiency are the growth of labor productivity, the reduction of material and labor costs, as well as the increase in the reliability of contractual (contractual) production, transport and warehouse communications that underlie the serviced systems and their processes. implementation.
It will be important to closely monitor ongoing and planned pilot programs designed to test these technologies to determine what role they can play in enhancing supply chain security. Proper documentation, including bills of lading, operating procedures and letters of credit, is essential for the movement of goods. The electronic exchange of documents required throughout the delivery process is becoming more and more common.
The first electronic documents to be exchanged were those directly related to money, such as purchase orders, work orders, invoices, and payments. In some cases, the electronic exchange of other documents during the shipping process is increasing because in some cases no paper document is generated. Historically, the validity of a shipping document was verified by people along the route who physically examined the document itself and any seal attached. Some fraudulent or forged documents will usually be detected, but some will not.
Evaluation of the economic efficiency of container services according to the criterion of reduced costs for the implementation of the product delivery process provides the most complete account of the factors that determine the magnitude of efficiency.
The container is loaded onto the vessel in New York and follows a direct flight to Rotterdam, where the unloading / loading of passing containers and empty units takes place, the information about the slave container is updated. The vessel goes on a voyage to St. Petersburg, where the container is unloaded and, after passing through customs and other formalities, it follows to its destination by main (railway) or motor transport. If the container is loaded onto the main platform, then “to the door” is delivered again by road.
In general, the system has been designed to limit the number of incorrect documents to an acceptable level throughout the transport sector. However, a steady move towards electronic documents could change this delicate balance significantly, as electronic documents are easily reproduced, altered, or counterfeited if not executed properly. More importantly, it is impossible for a human to detect such forgery, let alone control the rapidly growing number of exchange documents.
As discussed above, such technology is widely used in many applications and is widely available. An effective digital signature will remove the document's vulnerability to forgery and fraudulent use. The transport sector in general, and system developers in particular, have largely not included digital signatures in new systems.
I. Terms of Reference
Name of applications - IS "Airport"
2.Performance of research work:
2.1.Determination of the structure of input and output data.
Develop an information system that provides work with the database, including records of the form:
| Cargo transportation |
|||
| Podshita rashodov To date, counterfeiting in the trucking industry has had little impact on funding. However, if the weapons of mass destruction are to be smuggled, forgery can be an integral part of the deception. The study presented here should analyze the use of digital signatures in electronic documents and determine if steps can be taken to encourage wider use. In many cases, the worst cybersecurity problems come from the first wave of performance gains that come with computer systems. That is, when computerized systems are first deployed to improve productivity, they naturally bring about changes in business processes and procedures that people follow to get their jobs done. If the consequences of those human-centric changes are not considered by the system designers, the offender can take advantage of these changes and cause more complex problems than previously possible. |
vibor mashini dlay perevozki |
||
2.2. Requirements for the composition and parameters of PC hardware.
External devices, their characteristics.
For the operation of this application, the programs require a PC with a microprocessor 1.6GHz or higher, random access memory 512 Mb, HDD 80 Gb, NVIDIA GeForce 8600 GTS video adapter, monitor, mouse, keyboard, printer.
Similarly, digitally signing electronic documents based on strong cryptography can create an environment where electronic documents replace paper documents, which can change normal business processes and procedures. The performance improvements provided by electronic documents come with a price. Widespread use of electronic documents will require the development of an electronic infrastructure to support the authentication of individuals and organizations, document standards in various transport sectors, and a set of audit processes to ensure the normal operation of the system.
2.3. Requirements for information and software compatibility.
The application requires Windows 7 operating system, MS Access database management system, text editor MS Word, Rational Rose software design program.
II. Sketch project. Explanatory note (GOST 19.404-78)
Name of applications - IS "cargo transportation"
Such infrastructure elements are being developed across a wide range of business sectors and are starting to develop in the transport sector. The study presented here should consider the value of pilot programs in identifying the various challenges and challenges associated with establishing such an e-infrastructure in the transport sector.
This may be due to changes in existing business practices and the development of infrastructure elements in various business sectors, among other reasons. Economic forces are pushing most systems towards Internet communications as a result of widespread, near-universal access. Consumer carriers handle a significant portion of their business over the Internet, keeping up.
1. Justification for the need to develop an application:
Rationale for development - writing a term paper
Purpose for development - this application is a database that is designed for the successful and convenient operation of the airport.
2. Setting a task for development, description of solution methods:
A general push towards online trading in all sectors. Likewise, business carriers are also beginning to use the Internet for a significant portion of their transactions. With the increase in the use of the Internet, the need for secure communications and stronger authentication methods in most information systems, especially those using the Internet, has come to be recognized. Hardware Authentication IDs, which are issued to users who need to access the system via the Internet or some other remote access technology, replace or supplement the conventional password system to enhance the remote authentication process.
2.1.Database structure.
Table «Buhgalteriya»
Table "Podshita rashodov"

Table "vibor mashini dlay perevozki"
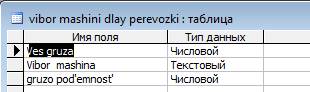
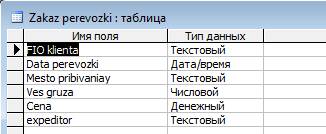
Table «Zakaz perevozki»
2.2.Diagrams.
Virtual Private Network technologies have been developed to provide additional layers of security for remote communication between users and the system and the system over the Internet. One of the problems faced by the developers of the Internet is the problem of accessibility. As the Internet is increasingly used as the primary method of communication between transport systems, the ability to transmit data securely over the Internet becomes more critical. Internet accessibility is a double-edged sword.
On the one hand, the Internet is vast, and many redundant paths between all points - local and even regional breakdowns in one part of the Internet heal relatively quickly, redirecting traffic around problem areas. On the other hand, key resources on the Internet depend on standard software components that are constantly under attack from various sources, constantly looking for ways to eliminate them.
2.2.1 Diagram of use cases.
External users - physical objects of a different nature (from people and mechanisms to software) that transmit or receive information for the system;
Usage blocks - groups of system functions that are combined into a single whole for an external user;
![]()
Designed to display time dependencies that arise in the process of communication between objects. The sequence diagram depicts only those objects that are directly involved in the interaction and does not show possible static associations with other objects. For chart key point is precisely the dynamics of the interaction of objects in time. In this case, the sequence diagram has, as it were, two dimensions. One - from left to right in the form of vertical lines, each of which depicts the lifeline of a separate object participating in the interaction. Graphically, each object is represented by a rectangle and is located at the top of its lifeline. Inside the rectangle, the name of the object and the name of the class are written, separated by a colon.

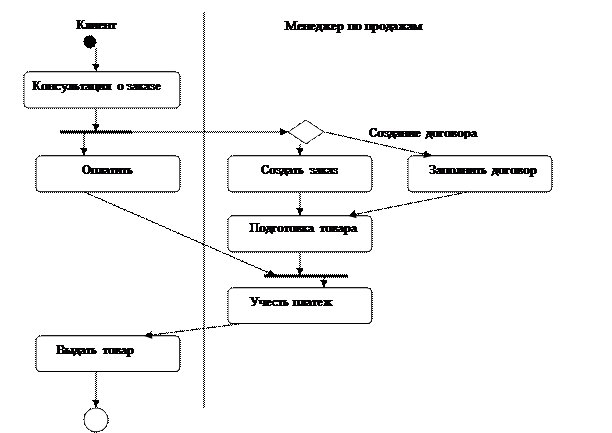
2.2.3.Diagram of actions.
Shows the operation. The purpose of this diagram is to show the flow of control internal to an operation. The action diagram is divided into 2 bands, which include a specific set of actions and transitions. Each lane has its own name: client and sales manager, and thus allows you to group actions into a single whole. Graphically, each bar represents a vertical division of the chart with a solid bar. Each action can only be in one lane, and transitions can cross lanes.
2.2.4.Diagram of cooperation.
main feature cooperation diagrams lies in the ability to graphically represent not only the sequence of interaction, but also all the structural relationships between the objects participating in this interaction. On the diagram, the objects participating in the interaction are shown in the form of rectangles, containing the name of the object, its class: order option selection, order details form, order manager, order, general manager. Further on the diagram, associations between objects are indicated in the form of various connecting lines. Between objects, dynamic links are displayed - message flows - in the form of connecting lines, above which there is an arrow indicating the direction, message name, ordinal number in the general sequence of message initialization.

2.2.Diagrams.
2.2 Diagrams of use cases.
Use case diagrams describe the functionality of the system or what the system is supposed to do. The diagram includes the following elements:
External users - physical objects of different nature (from people and mechanisms to software) that transmit or receive information for the system;
Use block - groups of system functions that are combined into a single whole for an external user;
Links between use blocks and links between use blocks and external users.

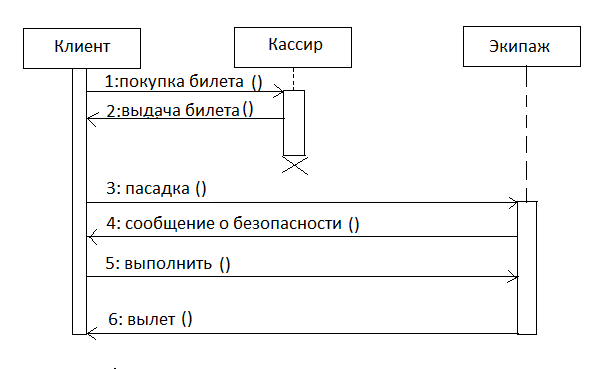
2.2.2 Sequence diagram.
Designed to display time dependencies that arise in the process of communication between objects. The sequence diagram depicts only those objects that are directly involved in the interaction and does not show possible static associations with other objects. On the constructed diagram, the objects are: client, cashier, crew. For the diagram, the key point is precisely the dynamics of the interaction of objects over time. In this case, the sequence diagram has, as it were, two dimensions. One - from left to right in the form of vertical lines, each of which depicts the lifeline of a separate object participating in the interaction. Graphically, each object is represented by a rectangle and is located at the top of its lifeline.
2.3 Instructions for the user.
This application is represented by a button interface - this is a user interface with a database, it is developed individually for each application, it is a user form that contains all the objects of the database. This form contains buttons for working with application data: accounting, ordering, calculating expenses, choosing a car. By clicking these buttons, you can see all the information about the store computer technology. The form is also intended for making changes to the application. In the lower right corner there is a button to exit this application.
3. Description of hardware and software.
The MS Access database management system was chosen to write the database. Due to the fact that at present enterprises mainly use Pentium 3 and higher computers, operating systems Windows 2000, ME, XP, Vista and office suite MS office. Therefore, operating systems of this type were chosen to develop their application, versions Word programs and Access and Rational Rose.
Brief characteristics of the operating system Windows 7
Microsoft Windows 7 Professional is the latest operating system, the optimal solution for both home and office work. Provides advanced features for business, entertainment, storage, archiving, protection and recovery of information. Supports the ability to securely connect to corporate networks through the domain.
Get the most out of the latest hardware with the new Windows 7! Microsoft Windows 7 Professional is a flexible operating system tailored for business tasks.
Key features of Windows 7 Professional:
Significant increase in productivity: quick launch and shutdown, fast switching between sessions and modes.
· System resource management modules, optimization of load distribution, protection against unexpected failures and freezes, automatic system diagnostics imperceptible to the user.
Intelligent Search Acceleration Technology necessary files and programs and a convenient system for viewing search results. Any item from your archives saved under Windows 7 can now be found in minutes!
Built-in web search option via Windows Internet Explorer 7.
· Watch, pause, rewind and record TV programs with Windows media center.
· System parental control to prevent unauthorized use and block unwanted data.
· Flexible system Microsoft settings Windows 7 Pro.
· Ensuring device compatibility, providing all necessary drivers through Windows Update.
· Ensuring full compatibility of applications within the system, built-in compatibility tools.
· Ability to easily transfer data and settings from an old PC to a new one.
Additional features of Windows 7 Professional:
· Fundamental security features: protecting the kernel from changes, strengthening the protection of services, preventing unauthorized data execution, protecting against accidental changes in the structure of the address space, maintaining mandatory integrity levels.
· Increased battery life by reducing the total number of background tasks, diagnosing the causes of energy overruns, auto-saving power during idle time, dimming the display, sleep mode, etc.
· Design support for 64-bit processors.
· For IT-specialists in Microsoft Windows 7 Professional work through command line, support for WMI scripts to view system stability analysis tool (RAC) data, system stability monitoring.
Video report: New features of Windows 7. Booting the system from a VHD disk
· One of the most interesting and long-awaited features in Windows 7 is support for virtual files. hard drives VHD as normal physical drives. The report discusses the process of installing and loading an operating system from a VHD file, allowing you to familiarize yourself with the new operating system without affecting the OS currently installed on the computer.
Conclusion
The purpose of this work was to create an information system "cargo transportation". This system is designed to function as a freight management campaign. This application was written in Rational Rose and the database was created in MS Access.
While working on this product, I learned how to create and design databases, and how to develop various types of diagrams. At present, the storage, retrieval and access to information has become an important phenomenon. The use of this product in a computer equipment store allows you to reduce all human costs and efforts, and most importantly, quickly give the result the employee needs, as well as replace large archives with structured storage in electronic form.
I also learned about freight forwarding companies, learned how they function.
Brief characteristics of the Rational Rose program
Rational Rose, unlike similar design tools, is capable of designing systems of any complexity, that is, the program toolkit allows both high-level (abstract) representation (for example, an enterprise automation scheme) and low-level design (program interface, database scheme, partial description of classes). The whole power of the program is based on just 7 diagrams, which, depending on the situation, are able to describe various actions.
1. Analysis of requirements for automated information systems / Internet University Information technologies. http://www.INTUIT.ru.
2. Butch G. Object-oriented design with examples of application / Per. from English. / G. Butch. – M.: Concord, 1992.
3. Vendrov A.M. CASE technologies. Modern methods and means of designing information systems. - M.: Finance and statistics, 1998.
4. Gvozdeva T.V. Designing information systems: a tutorial. - Rostov n / a: Phoenix, 2009.
5. Gvozdeva T.V. Design of information systems. Part 1. Methods of structural analysis. Planning and project management: lab.workshop / GOU VPO "Ivanovo State Power Engineering University named after V.I. Lenin". - Ivanovo, 2005.
6. Parondzhanov S.D. Methodology for creating corporate IS. Argussoft Company. 96, http:///www.citforum.ru/database/kbd96/43.shtml.
7. Designing information systems: textbook for universities / under the general editorship of. K.I. Kurbakov. Moscow: Russian Economic Academy, 2000.
8. Fomenkov S.A. Lectures on the course of modeling. http://vstuhelp.narod.ru.
9. Cheremnykh S.V. Modeling and analysis of systems: IDEF-technologies: workshop / SV Cheremnykh. - M.: Finance and statistics, 2002.
10. Cheremnykh S.V. Structural analysis of systems: IDEF-technologies: workshop / SV Cheremnykh. - M.: Finance and statistics, 2003.
Online service for operational work of forwarding companies. Create requests for transportation, organize documents, control the work of logistics managers, monitor the profitability of the company.
Online business management system in the field of cargo transportation. The purpose of the system is to ensure timely exchange of information, SaaS document flow between customers, carriers and forwarding companies in a single information space using the internet portal.
A cloud service for automating transport logistics and can be supplied both in SaaS format and with installation on the customer's servers. Allows you to optimize routes. GLONASS/GPS integration with transport monitoring.
A program for accounting for motor vehicles of your own fleet, documents related to accounting, generating and printing waybills, accounting for repairs and maintenance, accounting for fuel and lubricants, drivers, accounting for counterparties and working with them, warehouse accounting.
Online program for maintaining a secure document flow for the transportation of goods. Organization of a systematic approach to the processing of applications and full transparency of the process from the receipt of an application for transportation to the arrival of the cargo at its destination
Online service to automate all processes transport company. Allows you to create and control applications, maintain acts and TTN, salaries, generate reports
Cloud SaaS solution designed for automatic planning of delivery routes. The program for logistics is based on a unique algorithm that optimally plans routes, taking into account all restrictions, and also selects the optimal sequence of routes and the most suitable one in terms of technical capabilities and cost of transport.
Robotic software package for automating accounting and management at a motor transport enterprise. It combines all the resources and processes of a motor transport enterprise into one convenient control system.
1C configuration for vehicle accounting. The program allows you to keep track of fuel and lubricants, waybills, monitor routine maintenance, carry out dispatching functions, control the availability and relevance of drivers' documents. Cars are stored in car parks and boxes, the presence of cars in the boxes is controlled. A mechanism for warehouse accounting of fuels and lubricants, spare parts and other material assets has been implemented.
Automation system for management and operational accounting in motor transport enterprises, as well as in transport divisions of trade, manufacturing and other companies with various industry specifics.
A program for transport companies and forwarders, as well as any logistics departments of enterprises whose activities are somehow related to transportation: cargo transportation, trucking, delivery, etc.
The system based on 1C:Enterprise 8 comprehensively automates all business processes of vehicle management at enterprises of any size and industry.
A trucking management software package that has the full range of functionality required by most freight forwarding companies.
Configuration for accounting waybills in 1C with a wide range of features and a familiar interface.
A program for cargo transportation that can manage the process of cargo delivery. dispatcher workstation, mobile app for the driver, SMS informing, reporting
Freight transportation and logistics automation program. CRM-system (TMS-system), which will simplify the accounting of transportation and automate all processes of the transport company. Solutions for a manager, logistician, dispatcher, accountant, as well as control tools for the head of the transport department.
