Material from Encyclopedia Hub.ru
So how can you check your computer's network activity? There is a simple utility from Mark Russinovich, whose company was acquired by Microsoft in 2006, and now all these numerous utilities from Sysinternals are posted on microsoft.com and are officially recommended for use. In terms of control network connections there is tcpview, which perfectly copes with the task and does not have any unnecessary bells and whistles.
In order not to search for a long time on the Microsoft website, I will save a small archive with the utility here.
It’s very simple to use: unpack the archive and run Tcpview.exe (the first time you run it, it will show the license agreement - you must agree), you’ll see something like this on the screen:
And then we see everything! The first column is the application (name of the file to be launched) that initiated the network activity. Second column - network protocol, followed by the name and port of the initiator (usually your computer) and the address/port of the recipient. The last column is the connection status: LISTENING - the application has opened a port and is waiting for an incoming connection; ESTABLISHED - connection established.
We look at the list carefully and think, does any specific application need to go online? If it's a browser, that's understandable, but if it's AutoCAD, then don't expect anything good from it. You can close the connection one-time by clicking the mouse button on the desired line, and if this happens repeatedly and removing the “informer and spy” is not an option, you should already think about installing a firewall.
This utility does not replace a firewall in any way, it has an informative function, but this data is often irreplaceable and I advise you to always keep it ready with the ability to quickly launch and “look under the hood” if necessary. The decision about the need for some application is also up to you, if there is something incomprehensible hanging there and interfering with the network, it is better to first close the connection, then delete the process, and if nothing bad happens, then delete the file from the disk altogether (to be on the safe side, you can first change its extension to ex_ for example).
If you are a home user, you will someday be faced with the task of setting up an Internet connection, synchronizing with the game XBOX console, and if you have several units at home computer equipment, then in any case you will have to configure the wired or wireless network, and one computer will have to distribute the Internet to all the others. In case you are working system administrators small office, you will need to set up a network with static or dynamic addresses. Unfortunately, many users usually try to set up a local network without having any networking skills, and therefore carry out the setup at random, which causes them to have many problems during subsequent work. This series of articles is dedicated to various configuration methods local network, terminology, as well as connections to the World Wide Web.
Often, setting up a local network in operating systems Windows Vista, Windows 7, Windows Server 2008/2008 R2 begins with such an area for configuring network properties as the . With this network configuration tool, you can select a network location, view a network map, set up network discovery, file and printer sharing, and configure and view the status of your current network connections. In this article you will learn about managing this component.
Open Network and Sharing Center
In order to use the functionality of the network configuration tool, you first need to open it. To open a window "Network Control Center and shared access" , Perform one of the following actions:
The following illustration shows the window "Network and Sharing Center".
I wanted to do without an introduction this time, but I couldn’t resist. Never wondered how much is on your operating system network connections have been established, and by which services, programs to which addresses. This information can be obtained using some firewalls if, if you have it installed. But there is one free utility written by Mark Russinovich, a guru who has written many useful utilities for Windows.

The program does not need to be installed, just download the archive, unpack the files and run the utility. The size is simply miniature for today's times, only about 200 kilobytes, find something similar with such capabilities. In the open window we get a list of all processes that open network connections, the protocol used, the status and local and remote addresses that are used. Information is updated at a set frequency (default 1 second), which can be configured.
You can choose to show IP addresses or define them domain names if it is possible. In order not to drown in a heap of unnecessary information, you can disconnect connections that do not have a final responding point.
From the context menu you can find out information about the selected process (path to the executable file), terminate the process (helps kill dangerous or suspicious programs), close the connection (high-speed disconnection from unnecessary sites, leaving the process in working order) and get information about the current site to to whom the connection is made (sometimes you learn interesting things).
Only TCP, UDP and TCPV6 (it turns out that it is now actively used) protocols, which are currently used for all network traffic on computers, are monitored.
Among the settings, there is only changing the font parameters, and that’s all.

TCPView is a utility that does its job, does not have a fabulous interface, but works like a clock, a classic workhorse. When the utility is working, you simply don’t notice it, and when it’s not at hand, you feel like something important is missing. For those who do not understand its purpose, you will not need it for those who are required to use it in the topic.
Works great on 32 and 64 bit operating systems. There is only one language available, English, no other options are offered.
TCPView free download page http://technet.microsoft.com/en-us/sysinternals/bb897437.aspx
Latest version at the time of writing TCPView 2.54
Introduction
TCPView is a program designed for the Windows operating system that displays lists of endpoints of all TCP and UDP connections established on the system with detailed data, including local and remote addresses and the status of TCP connections. On Windows NT, 2000, and XP operating systems, TCPView also reports the name of the process that owns the endpoint. TCPView is an extension of Netstat, which comes with Windows, and provides more information in a more convenient way. The TCPView download includes the Tcpvcon program with the same functionality, designed to work in command line mode.
TCPView runs on Windows NT/2000/XP and Windows 98/Me operating systems. TCPView can also be used in the operating room Windows system 95 subject to installation Winsock 2 update package for Windows 95 operating system provided by Microsoft Corporation.
Using TCPView
When launched, TCPView generates a list of all active TCP and UDP connection endpoints, displaying all IP addresses as domain names. To switch the display mode to view addresses in digital form, you can use a toolbar button or a menu item. On Windows XP operating systems, TCPView displays for each endpoint the name of the process to which that endpoint belongs.
By default, TCPView updates information once per second, but the update period can be changed using the Refresh Rate(Update period) in the menu Options(Options). If the state of an endpoint has changed between updates, it is highlighted in yellow; if an endpoint has been deleted, it is highlighted in red; new endpoints are displayed in green.
To close established connections via TCP/IP protocols (with the status marked ESTABLISHED (installed)), you can select the Close Connections(Close connections) in the menu File(File) or click right click mouse any connection and select in context menu paragraph Close Connections.
The data displayed in the TCPView program window can be saved as a file using the menu item Save(save).
Using the Tcpvcon program
Using the Tcpvcon utility is similar to using the netstat utility, which is built into the Windows operating system.
Usage: tcpvcon [-a] [-c] [-n] [process name or PID]
Netstatp source code
Want to know how TCPView works? Using the source code of the Netstatp program as an example, we show how to program some of the functions of the TCPView program. This example program shows how to use the IP Helper interfaces (see documentation on MSDN) to obtain a list of TCP/IP connection endpoints. However, note that netstatp does not display process names on NT 4 and Windows 2000 systems like TCPView and TCPVCon do.
Microsoft Knowledge Base article about TCPView
This Microsoft Knowledge Base article is about TCPView:
Interconnected utility
TDImon- Shows activity using TCP and UDP protocols in real time.
If you liked TCPView, you'll like TCPView Pro even more. TCPView Pro, developed by Winternals Software, has a number of features that make it much more powerful and useful than TCPView. These are the following functions: viewing data about the processes that own the endpoints of open connections (also works on Windows 9x)
- View process activity using TCP and UDP protocols in real time
- Using advanced filtering techniques to show only the data you need.
- and much more...
TCPView Pro is supplied as part of Winternals Administrator's Pak.
Admin, let's remove it by making the window empty. To begin with, in the window Accounts users click on the button Changing user logins and remove the checkbox Use Welcome Page(Fig. 19.6 and Fig. 19.7).
Rice. 19.6.
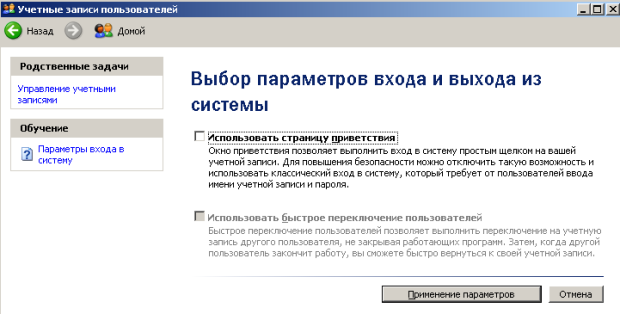
Rice. 19.7.
But that's only half the story. Now let’s increase network security one more notional step by making both fields of the welcome window empty (Fig. 19.8).
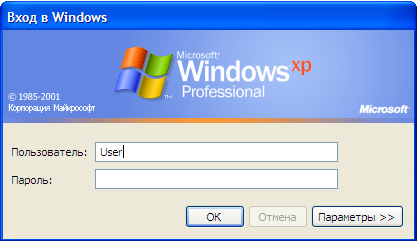
Rice. 19.8.
Let's run the command Control Panel - Administrative Tools - Local Security Policies - Local Policies - Security Settings - Interactive login: do not display last username. This entry must be enabled (Fig. 19.9).

Rice. 19.9.
Now, after completing the session, the user must guess not only the password, but also Username(Fig. 19.10).

Rice. 19.10.
Detecting network vulnerabilities by scanning PC ports
Attackers use PC port scanning to take advantage of the resources of someone else's PC on the Internet. In this case it is necessary to indicate IP PC open address port, For example, 195.34.34.30:23 . After this, a connection occurs with a remote PC with a certain probability of entering this PC.
- TCP/IP port is the address of a specific service (program) running on this computer on the Internet. Every open port- a potential loophole for network and PC hackers. For example, SMTP (sending mail) - port 25, WWW - port 80, FTP - port 21.
- Hackers scan ports to find a hole (bug) in the operating system. An example of an error if an administrator or PC user has granted full access to network resources for everyone or left a blank password for logging into the computer.
One of the functions of a network administrator (sysadmin) is to identify shortcomings in the functioning of the network and eliminate them. To do this, you need to scan the network and close (block) all unnecessary ones (opened unnecessarily) network ports. Below, as an example, are the TCP/IP services that can be disabled:
- finger - getting information about users
- talk - the ability to exchange data over the network between users
- bootp - provides clients with network information
- systat - getting system information
- netstat - Get network information such as current connections
- rusersd - getting information about currently registered users
Viewing active connections using Netstat utility
Team netstat has a set of keys to display ports that are in active and/or passive states. With its help, you can get a list of server applications running on a given computer. Most servers are in mode LISTEN- waiting for a connection request. State CLOSE_WAIT means the connection is broken. TIME_WAIT- the connection is waiting to be disconnected. If the connection is in SYN_SENT, then this means there is a process that is trying to establish a connection with the server. ESTABLISHED- connections are established, i.e. network services are running (in use).
So, the netstat command displays the contents of various network-related data structures in different formats depending on the options specified. The following status values are allowed for TCP sockets (software interfaces):
- CLOSED - Closed. The socket is not in use.
- LISTEN - Waits for incoming connections.
- SYN_SENT - Actively trying to establish a connection.
- SYN_RECEIVED - Initial connection synchronization in progress.
- ESTABLISHED - Connection established.
- CLOSE_WAIT - The remote side has disconnected; waiting for the socket to close.
- FIN_WAIT_1 - The socket is closed; disconnecting the connection.
- CLOSING - The socket is closed, then the remote side disconnected; Waiting for confirmation.
- LAST_ACK - The remote side disconnected, then the socket is closed; Waiting for confirmation.
- FIN_WAIT_2 - The socket is closed; waiting for the remote side to disconnect.
- TIME_WAIT - The socket is closed, but is waiting for packets still on the network for processing
