Our company offers a service router connection, as well as diagnostics, repair, configuration and connection of the router (router) wired and wireless home computer network. Works are carried out with departure to the customer.
First of all, the router (router) in translation means a router. This is the same device, sometimes called that, and sometimes that way. transfer data between different devices connected to the same network, draw up routes and sequence of this transfer and carry out their simultaneous operation in the global network.
The home network must connect router to connect computers, laptops, smartphones, TVs and other devices to the communication channel of the Internet provider.
Modern routers have a number of additional features that greatly expand the convenience of its use:
Access point Wi-Fi, which allows you to connect a router to organize a simple connection of wireless devices. Almost all modern devices such as TVs, Blu-ray players, gaming consoles, camcorders, tablets, smartphones and others have a built-in wireless connection module. Using a wireless access point allows you to organize their joint work and independent access to the global Internet.
USB port allowing to organize router connection and its connection to a printer or disk storage. Using this port, there is no need to constantly keep the desktop turned on to print any documents or save data. The whole procedure is controlled by the connected router. From any device connected to the home network, you can save data to paper or electronic media.
Reception and transmission of data from the global network can be carried out in several ways: mobile communications, via telephone wire, via twisted-pair cable, via antenna cable, via electrical network, via satellite communication. Accordingly, various devices are produced and it is necessary to understand how to connect a router for a specific type of use of the global network.
Mobile networks 3G and 4G - LTE, the standard for data transmission technology through operators cellular communication. 3G Internet is present in almost the entire territory of the Moscow region. 4G high-speed Internet covers the whole of Moscow and the nearest suburbs. The mobile network router has a built-in antenna for receiving signals from the mobile operator; in the area of \u200b\u200buncertain reception, it is possible to use a special 3G antenna directed at the cell tower to the router. This greatly improves the quality of the Internet connection. A special socket on the case allows you to connect the router via an RF cable to the antenna.
Through wired telephone lines using the ADSL technology standard This technology allows you to connect the router to the Internet through a regular telephone socket. There are varieties of ADSL2 and ADSL2+ technology that significantly increase the data transfer rate. The router is connected through a special splitter that separates the audio transmission channels from the information transmission channels. Each telephone connected in parallel is connected to the telephone socket through a special ADSL microfilter, which ensures the preservation of the quality of telephone communication during the transmission of information data packets.
 Through a twisted-pair cable specially brought into the apartment, ETHERNET technology, which is brought into the apartment and allows you to connect the router to the provider's equipment. This cable consists of 4 pairs of copper wires in common insulation, equally twisted together. This design has good noise immunity and allows you to create data transmission at speeds up to 100 Mbps. As a rule, it is these cables that connect various devices. home network when wired to the LAN jack of the router.
Through a twisted-pair cable specially brought into the apartment, ETHERNET technology, which is brought into the apartment and allows you to connect the router to the provider's equipment. This cable consists of 4 pairs of copper wires in common insulation, equally twisted together. This design has good noise immunity and allows you to create data transmission at speeds up to 100 Mbps. As a rule, it is these cables that connect various devices. home network when wired to the LAN jack of the router.
By TV antenna cable - EoC technology. In this case, an antenna cable already laid around the apartment is used for viewing television programs. Through the splitter, the television signal and digital data are separated, the image and sound signal is fed to the antenna input of the TV, and the information signal via a coaxial cable must be connected to the router, to a specially designed input for this. The convenience of this technology is that there is no need to stretch a special wire, because a television antenna is present in almost every home.
By fiber optic cable - GPON technology. A special fiber optic cable is brought into the apartment, and by connecting a router connects various devices to the home network at speeds up to 1Gbps. Actually, the abbreviation GPON is translated as Gigabit Passive Optical Network. Through such a router connection, you can easily connect all home devices to the Internet and ensure high-quality reception of digital television channels.
Via electrical outlet - PLC technology. In this case, the role of the home computer network is performed by the electrical wiring in the house. Refer to the instructions that came with the adapter to find out how to connect the router. Data is transmitted through electrical sockets and wires located in the apartment under 220V voltage using special adapters.
Using a satellite dish - two-way, when both receiving and transmitting information occurs through a communication satellite, or one-way (asymmetric) - when it is used to receive data satellite channel, and for transmission - available terrestrial channels, usually mobile networks.
According to the method of data transfer within the home network, that is, according to the method of connecting various devices and connecting them to the router, routers are divided into: wired - all devices on the network are connected only with special cables connected to the LAN connector of the router, wireless - when all devices are connected to each other to a friend and to a router via Wi-Fi wireless technology, and mixed, when the router has at least one LAN output and the ability to wireless wifi connections.
In this article, we will look at the main types of equipment needed to create a home local network. However, this knowledge will be fully useful for creating an office local network, so after reading the article, you can safely look for a job as a system administrator :) Well, if you read other articles from the heading ““ in addition, you can completely put any it - shnega! However, we digress :) So, let's move on to the equipment.
Network adapters
A few years ago, most computers connected to local networks using network adapters, which were installed in the PCI slot of the motherboard. However, this was before, because now each motherboard has its own built-in network adapter, which is equipped with a corresponding RJ-45 connector. This connector is used in Ethernet networks and can easily be found on the back of the motherboard or just look at the back of your computer case.
Dusty Like in an ass at a black man, sorry connector RJ-45 is on every motherboard.
If you dug up a motherboard somewhere without the right connector (or you need more than one connector), then you will need an external network adapter.
It can be either a PCI/PCI-E board or an external network adapter with a USB connector. Of course, ancient 10BASE-T adapters with a data rate of 10 Mbps are hard to find even in the radio market from a junk dealer, so forget about them. You only need a Fast or, better yet, Gigabit Ethernet adapter.
A typical NIC for a PCI port. It is so cheap that, one might say, they give for a can of beer.

The USB-to-Ethernet adapter is also great, and you don't have to open the case. It is enough to have free USB port.

Almost all modern Fast Ethernet network adapters are designed to use unshielded UTP twisted-pair cables exclusively. The same is true for Gigabit Ethernet adapters designed to use conventional rather than fiber optic cables. As already mentioned, separate network cards are practically extinct in home computers, since all modern motherboards have such a connector. But if you need two connectors, then a separate network card will come in handy.
To set up like motherboards with support for local network connections and network adapters require driver installation. In most cases, you can use standard windows drivers. In case of problems or to support special functions, you can install the driver, which is usually supplied on a CD or floppy disk with the system board or network adapter. In addition, the required driver can always be downloaded from the Internet.
As already mentioned, most modern Ethernet LANs are based on a star topology using network adapters, UTP cables and switches (hubs are already hopelessly outdated, so we won’t mention them)).
(switch) provides data transfer between computers of the same network segment. Appearance The switch may not differ from the hub, but the principle of the switch is completely different. Instead of sending data to all computers on the network, the switch only sends data packets to the computer for which the packets are intended. In other words, thanks to the switch, a direct connection is organized between the computer that requested the data and the computer that transmits the requested information. Thanks to a direct connection between systems, all free network bandwidth is available for each port of the switch, which, as everyone knows, for a 100BASE-TX/1000BASE-TX network is 100/1000 Mbps.

The rear panel of the home networking hubs and switches has multiple RJ-45 ports, a power cord connector, and an Uplink port. RJ-45 ports are used to connect computers to them using a UTP cable. The Uplink port is essentially the same as an RJ-45 port, but with a different pinout. The port is required to connect an additional hub or switch to a hub or switch. This feature is used to expand an existing network.
Many modern switches have a built-in device for broadband Internet access, such as a cable or ADSL modem. These modems are also sold separately and connect to your computer using a standard network cable UTP Ethernet (category 5) or USB port.
Thanks to the RJ-45 port, the ADSL modem can be connected directly to a regular switch, then all computers on the local network should be connected to the switch's LAN ports, after which Internet access will be provided to the entire local network. In fact, a switch with a built-in broadband modem is a router. It is routers that are now the most popular device in the home network, and individual switches are gradually dying out.
Routers
On a normal local network router(aka router and illiterate bastard "router") provides a connection between a local area network (LAN) and a wide area network (WAN). The router analyzes network data packets and determines not only the computer for which these packets are intended, but also the most optimal way to deliver them. Routers are used to connect various networks, as well as to provide access to the Internet from the local network.
Modern routers are often equipped with ADSL or cable modems, and may be wireless or designed to act as a switch between a wired and wireless network. For security purposes, many routers support data encryption and contain a firewall that is used to protect against external attacks. Just like switches, other routers can be connected to routers.
Routers range from a simple home appliance to powerful backbone routers that power the entire Internet. Since we are interested in the home use of such devices, a typical home router plays the role of both a switch, thanks to which computers on the local network exchange data, and, in fact, a router, i.e. a device that provides data exchange between a local network and the Internet via a cable or DSL modem, or via an Ethernet port on an Ethernet local network.
This little Netgear has a built-in switch, wired/wireless router, and ADSL modem..

Technically, in order to organize access to the Internet from the local network, it is not necessary to purchase a router separately. Sometimes the functions of the router are assigned directly to the computer with the usual operating system, since operating systems like Windows XP or Vista can programmatically route data from a local network to a global (or other network) and vice versa.
At the same time, it is enough to connect the modem to the central computer in any way, for example, using the USB port, and then configure general access to the Internet. If Internet access is provided via an Ethernet connection, then the central computer will need to be equipped with an additional network card to route data (or even more than one card if several other PCs are to be connected to the central computer). In addition to all the described functions, some routers also act as a DHCP server, which is used to assign IP addresses to all computers on the network.
Here is a diagram of such a connection.

However, the scheme presented above is quite complicated to set up and inconvenient to maintain, therefore, it can be said that it is irrelevant. An inexpensive router with, for example, an ADSL modem can be bought for as little as $30, so don't be greedy. After spending a few minutes, you get full access to the Internet for all computers on the local network, not to mention the fact that the local network itself will be quite productive and efficient.
Do not flatter yourself with a minimum price of $ 30 - yes, it is inexpensive, but you will get through the roof with “glitches” and problems with such a device. There are practically no exceptions to this rule.
Of course, the question immediately arises, which router to choose? This is the topic of a separate article, but for now we will give three simple tips.
- Do not take a very cheap model, even with the most attractive features. There is a very high chance that it will be shamelessly "buggy" and "slow down".
- Run like hell from cheap D-Link and TP-Link models.
- Choose from ASUS, Linksys, Netgear, mid-priced or expensive D-Link models.
Today, everyone already knows how to create a network through a router and set up a point WiFi access. In fact, everything turned out to be simpler than one might expect: a wired switch is not needed, since it is built into the router, and performing configuration through the GUI has become the standard. Setting up a local network is reduced to specifying a single IP address, and the DHCP server adjusts to this value automatically.
We'll talk about what typical mistakes users allow when not the router is configured, but the subscriber device. In some cases, it is required to use static IPs (let's name which ones), but their values are sometimes not chosen correctly.
Device Local IP Addresses
By default, the local network in any router is already configured, and the address of the following form is assigned to it: 192.168.X.1 (instead of X, it is usually 1, 0 or 10). On all local devices, no one forbids enabling automatic address acquisition (auto DNS, auto IP), and in most cases everything really works as it should. Note that when using "automatic" each device receives an address issued by a DHCP server:
- 192.168.0.100 - 199 (D-Link router)
- 192.168.1.100 - 199 (TP-Link)
- 192.168.1.100 - 254 (ASUS)
- Etc.
You can see that by default there is always a range (pool) of free addresses that are not occupied by the DHCP service: 192.168.1.2 - 99, and other pools. Free values just need to be used if you are going to set the address on the subscriber device explicitly. Sometimes you want to do just that, that is, make the transition to using statics, not paying attention to anything else. We will talk more about this now.
Why "static" in LAN?
Computer connected to the port LAN router, usually set to automatic:

TCP/IP settings, wired adapter
Specifying the IP address explicitly, that is, switching to "static", is required in such cases:
- The device goes into sleep mode instead of shutting down. When it "wakes up", it will continue to use the IP value, which will no longer be relevant for it - the DHCP server will update all values \u200b\u200bby that time (an IP address conflict is not excluded)
- Some consoles, like PS3, can only use IP values in which the last digit is small (2.3 ... 9). It is possible to correct the DHCP server setting accordingly, although this is not required. It will be easier to register the IP address in the subscriber device itself (in the set-top box)
- Sometimes the router settings get lost, and then you won’t be able to enter the web interface without assigning a static value to the PC.
Setting Static Local IP Addresses
We have already said that by default the range of values occupied by the DHCP server and used by it in the process of operation usually starts with the following numbers: 192.168.X.100. Less often, the last digit can be "50", but the essence remains the same - there is always a pool of free values, which we should use for our own purposes. You can safely assign an IP address to the computer equal to "192.168.0.49" (if the router is accessible via local address"192.168.0.1"). Well, you will then assign the value “192.168.0.2” to the SPS prefix (and why, it was described above).

Setting the address of the set-top box, cable
When setting up, as discussed here, you will notice that the device (computer, tablet, set-top box) requires you to specify not only the locale settings, but also the DNS address. To get started, use the numbers equal to the IP address of the router (as in the figure). Well, what needs to be done so that there are no problems with DNS in 100% of cases, we will consider in the next chapter. You will need a device capable of obtaining an IP value automatically. Usually, it is a Windows computer.
How to fill in the "DNS" field?
Let's say we have a computer that is connected to a router, and let's say automatic DNS and IP acquisition is enabled on this PC. Then, if you are using Windows 7, follow these steps:
- After right-clicking on the connection icon, enable the “Status” item
- In the window that appears, click the "Details" button
- In the new window, find the line "IPv4 DNS server" and write the numbers on a piece of paper
- Use the value you recorded in the future, registering it as a DNS address.

About connection options
Usually you will be shown the local IP of the router itself. The values issued by the provider are less commonly used, but all this is not so important - you will set as DNS what you see in the "Details" (if we are talking about setting "statics").
Note that in Windows XP, the "Details" button in the "Status" window is missing.
There you need to switch the tab and click the "Details" button. In general, it is recommended to specify universal values as DNS (8.8.8.8, 8.8.4.4). We warn you: by doing this, you will get a working Internet, but access to some provider resources may be lost. As a rule, in reality it happens.
We will talk here about the IPv6 protocol, or rather about how to turn it off. Some devices support this protocol, it is implemented in Windows 7 / Vista, but in XP it is not. The point is that inside the locale you need to disable IPv6 and use only IPv4 (both protocols can be enabled by default). After opening the "Status" of the connection, click the "Properties" button, and you will see the following window:
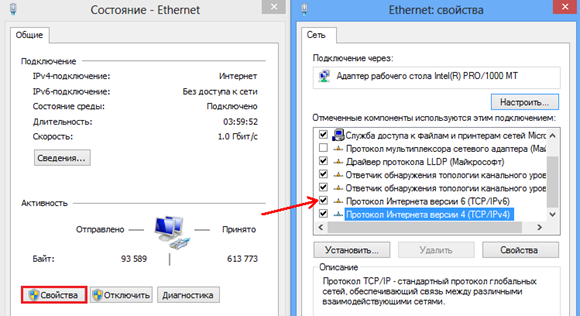
Where TCP/IPv6 is turned off
You will need to uncheck the box located in the line "Internet Protocol version 6", and click "OK".
Actually, having stopped the operation of IPv6 on all local devices, it remains to do the same in the main device (router). This option is not implemented in some models, that is, IPv6 is simply not there. And in theory, you can not disable anything if everything works as it should. We hope these tips will help you create a local network that will last its owner for a long time.
Here we have not considered recommendations that should be extended to special cases. For example, when talking about MAC cloning on a network combine equipped with gigabit ports, you need to take into account the features of the Ethernet 1000 protocol. In such cases, you need to exclude the presence of two devices with the same MAC address. You can also notice that home / small office combines are not designed for a significant number of users to simultaneously connect via Wi-Fi. Therefore, when designing a future network, if possible, preference is given to connecting via a LAN. Happy routing!
A lot of tools have been developed to protect against various kinds of attacks from the outside (that is, from the Internet) on a local network, but they all have one serious drawback: in order to implement this kind of protection, it is necessary to allocate a PC on which specialized software will be installed and configured. If we are talking about a fairly large network with at least a hundred PCs, then such a decision is quite justified, but in the case of small SOHO class networks, it is very expensive to allocate a computer to organize network protection. In addition, it must be remembered that professional packages that implement network protection are quite expensive, so for the SOHO segment, it may make sense to turn to alternative solutions. These are SOHO class routers, which are also called Internet servers and Internet routers. Currently, there are a huge number of similar routers on the market, differing from each other in functionality and price. In order to make the right choice, you need to clearly understand the capabilities and functions of modern routers.
Router design
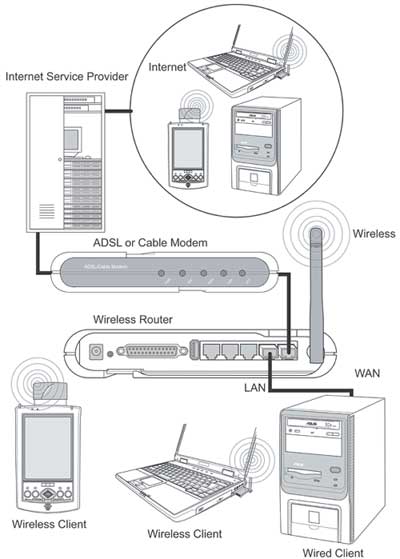
Since routers are network edge devices, that is, they are installed on the border between two networks or between a local network and the Internet, acting as a network gateway, they must have at least two ports (see figure). The LAN is connected to one of these ports, and this port is called the internal LAN port. The second port connects to the external network (Internet), and this port is called the external WAN port. As a rule, SOHO class routers have one WAN port and several (from one to four) internal LAN ports, which are combined into a switch. In most cases, the WAN port of the switch has a 10/100Base-TX interface, and an xDSL modem with the appropriate interface or an Ethernet network cable can be connected to it.
In some router models, in addition to the WAN port, there is a serial port for connecting an analog modem. As a rule, this port is intended for creating a redundant low-speed dial-up connection with an ISP.
Given the widespread wireless networks, a whole class of so-called wireless routers has been created. These devices, in addition to the classic router with WAN and LAN ports, contain an integrated wireless access point that supports the IEEE 802.11a/b/g protocol. The wireless segment of the network that the access point allows you to organize refers to the internal network from the point of view of the router, and in this sense, computers connected to the router wirelessly are no different from network computers connected to the LAN port.
Any router, as a network layer device, has its own IP address. In addition, its WAN port also has an IP address. For example, a router might have the following IP address:
IP address: 192.168.1.254;
At the same time, its WAN port may have the following address:
IP address: 10.0.0.254;
Subnet mask: 255.255.255.0.
Computers connected to the router's LAN ports must have an IP address on the same subnet as the router itself. In addition, in the network settings of these PCs, you must set the default gateway address to match the IP address of the router. For example, in the case above network settings The PC connected to the LAN port can be as follows:
IP address: 192.168.1.10;
Subnet mask: 255.255.255.0;
Default gateway: 192.168.1.254.
The device connected to the WAN port from the external network must have an IP address from the same subnet as the WAN port of the router. In our case, this can be the following network settings:
IP address: 10.0.0.10;
Subnet mask: 255.255.255.0.
In the example above, we used the so-called static method of setting an IP address (Static IP), which is supported by all routers. It should be used to familiarize yourself with the capabilities of the router or to test it. However, in real conditions, the dynamic (Dynamic IP) method of setting the IP address is more often used, when the router acts as a DHCP client, automatically obtaining an IP address, the address of the default gateway and the DNS server from the provider (DHCP server). This method provides the provider with sufficient flexibility in configuring their network and is supported by all providers.
Firewall
Since the router acts as a gateway between the local network and the Internet, it would be logical to give it such a function as protecting the internal network from unauthorized access. Therefore, almost all modern SOHO class routers have built-in hardware firewalls, also called firewalls, or firewalls. Of course, firewalls exist as standalone hardware solutions, but integrating a firewall with a router reduces the total cost of the hardware.
Firewalls analyze all traffic between two networks connected by a router to see if it meets certain criteria. If the traffic meets the specified conditions, then the firewall passes it through itself (produces routing). Otherwise, that is, if the established criteria are not met, the traffic is blocked by the firewall. Firewalls filter both incoming and outgoing traffic and allow you to control access to certain network resources or applications. They can record all attempts of unauthorized access to local network resources and issue warnings about penetration attempts.
Firewalls are capable of filtering network packets based on source and destination addresses and port numbers, a feature called address filtering. In addition, firewalls can filter specific types of network traffic, such as HTTP, ftp, or telnet, and can also filter traffic based on the analysis of network packet attributes.
There are two methodologies for how firewalls operate: one is that the firewall allows all traffic through it, except for those that meet certain criteria; the second is that the firewall, on the contrary, blocks all traffic except those that meet certain criteria.
The capabilities of firewalls and how intelligent they are depends on which layer of the OSI reference model they operate on. The higher the OSI level on which the firewall is built, the higher the level of protection it provides.
Recall that the OSI (Open System Interconnection) model includes seven levels of network architecture. The first, lowest level is the physical one. It is followed by the link, network, transport, session, presentation, and application or application layers.
In order to provide traffic filtering, the firewall must operate at least at the third level of the OSI model, that is, at network layer. At this level, packets are routed based on the translation of MAC addresses into network addresses. From the point of view of the TCP/IP protocol, this layer corresponds to the IP (Internet Protocol) layer. By receiving network layer information, firewalls are able to determine the source and destination address of a packet and check whether traffic is allowed to pass between these destinations. However, the network layer information is not sufficient to analyze the contents of the packet. Firewalls that operate at the transport layer of the OSI model get more information about packets and are smarter network protection schemes. When firewalls operate at the application layer, they have complete information about network packets, so these firewalls provide the most reliable network protection.
Professional firewalls capture every incoming packet before it is transmitted to the destination and accepted by its operating system. This makes it very difficult to take control of a computer protected by such a firewall.
All firewalls can be roughly divided into four categories according to the layers of the OSI model at which they operate:
Packet filter;
Session level gateway (circuit-level gateway);
Application-level gateway (application-level gateway);
Stateful Packet Inspection.
Packet filters
Packet filter type firewalls are the simplest and least intelligent. They operate at the network layer of the OSI model or at the IP layer of the TCP/IP protocol stack. Such firewalls are mandatory in any router, since all routers can operate at least at the third layer of the OSI model.
In packet filters, each packet is analyzed to see if it meets the transmission criteria or blocks the transmission before it is transmitted. Depending on the packet and the generated transmission criteria, the firewall may either forward the packet, reject it, or send a notification to the initiator of the transmission. The criteria, or rules, for packet transmission can be formed based on source and destination IP addresses, source and destination port numbers, and protocols used.
The advantage of packet filters is their low price. In addition, they practically do not affect the routing speed, that is, they do not adversely affect the performance of the router.
Session level gateways
Session level gateways are firewalls that operate at the session level of the OSI model or at the TCP (Transport Control Protocol) level of the TCP/IP protocol stack. They track the process of establishing a TCP connection (the organization of data exchange sessions between network nodes) and allow you to determine whether a given communication session is legitimate. Data transmitted remote computer in the external network through a gateway at the session level, do not contain information about the source of transmission, that is, everything looks as if the data is sent by the firewall itself, and not by a computer in the internal (protected) network. All firewalls based on the NAT protocol are session layer gateways (the NAT protocol will be described later).
The advantages of session-level gateways include their low price, and they do not significantly affect the routing speed. However, session layer gateways are not capable of filtering individual packets.
Application Layer Gateways
Application layer gateways, also called proxy servers, operate at the application layer of the OSI model, which is responsible for accessing applications to the network. At this level, tasks such as file transfer, mail exchange, and network management are solved. By receiving information about packets at the application level, such gateways can implement blocking access to certain services. For example, if the application layer gateway is configured as a Web proxy, then any traffic related to the telnet, ftp, gopher protocols will be blocked. Because these firewalls parse packets at the application layer, they are able to filter specific commands such as http:post, get, and so on. This feature is not available to packet filters or session level gateways. Application layer gateways can also be used to log the activity of individual users and set up communication sessions. These firewalls offer a more robust way to secure networks than session-level gateways and packet filters, but have a much greater impact on reducing routing speed.
SPI firewalls
Stateful Packet Inspection (SPI) firewalls combine the benefits of packet filters, session layer gateways, and application layer gateways. In fact, these are multi-level firewalls that work simultaneously at the network, session and application levels.
SPI firewalls filter packets at the network layer, determine the legitimacy of establishing a session based on session layer data, and parse the contents of packets using application layer data.
SPI firewalls provide the most secure network protection and are found in many modern routers.
NAT protocol
Most modern routers support the NAT (Network Address Translation) protocol, which is based on the session level and is essentially a network address translation protocol. NAT allows you to implement multiple access of computers on a local (private) network (each of which has its own internal IP address) to the Internet using just one external IP address WAN port of the router. In this case, all computers in the internal local network become invisible from the outside, but for each of them the external network is available. The NAT protocol allows only data from the Internet to enter the network that was received as a result of a request from a computer on the local network.
The NAT protocol solves two main tasks:
Helps to cope with the shortage of IP addresses, which is becoming more acute as the number of computers grows;
Provides security for the internal network LAN computers protected by a NAT-enabled router (NAT device) become inaccessible from the external network.
Although NAT does not replace the firewall, it is still a important element security.
The principle of operation of the NAT protocol is quite simple. When an internal network client communicates with an external network server, a socket is opened, identified by the source IP address, source port, destination IP address, destination port, and network protocol. When an application sends data over this socket, the source IP address and source port are inserted into the packet in the source parameter fields. The destination parameter fields will contain the server IP address and server port.
The NAT device (router) intercepts the outgoing packet from the internal network and enters in its internal table mappings of the source and destination ports of the packet using the destination IP address, destination port, external IP address of the NAT device, external port, network protocol, and internal IP -address and port of the client. The NAT device then translates the packet, transforming the source fields in the packet: the client's internal IP address and port are replaced with the NAT device's external IP address and port.
The converted packet is sent over the external network and eventually reaches the specified server. Upon receiving the packet, the server will send response packets to the external IP address and port of the NAT device (router), specifying its own IP address and port in the source fields.
The NAT device receives these packets from the server and parses their content based on its port mapping table. If a port mapping is found in the table for which the source IP address, source port, destination port, and network protocol from the incoming packet match the remote host IP address, remote port, and network protocol specified in the port mapping, then NAT will perform the reverse translation : will replace the external IP address and external port in the destination fields of the packet with the IP address and internal port of the internal network client. However, if there is no match in the port mapping table, then the incoming packet is rejected and the connection is closed.
Some routers may disable the NAT protocol. However, there are models where the NAT protocol is activated and it is impossible to disable it. At the same time, it is important that the router can partially bypass the restrictions of the NAT protocol. The fact is that not all network applications use protocols that can interact with NAT. Therefore, all routers have features that allow you to impose restrictions on the use of the NAT protocol. A server that is installed on the internal network and is transparent to the NAT protocol is called a virtual server (Virtual Server). Not the entire server can be transparent to the NAT protocol, but only certain applications running on it. In order to implement a virtual server on the internal network, the router uses port forwarding technology.
Port mapping
In order to make certain applications running on a server on the internal network (for example, a Web server or an ftp server) accessible from the external network, the router must be mapped between the ports used by certain applications and the IP addresses of those virtual servers on the internal network on which these applications run. In this case, they talk about port forwarding (Port mapping). As a result, any request from the external network to the IP address of the WAN port of the router (but not the virtual server) on the specified port will be automatically redirected to the specified virtual server.
There are several ways to configure virtual server. In the simplest case, static port forwarding is set, that is, the IP address of the virtual server, the allowed application port on this virtual server (Private Port) and the request port (Public Port). If, for example, access to the Web server (port 80) located on the internal network with IP address 192.168.1.10 is open, then when accessing from the external network at 10.0. this packet will be forwarded by the router to the Web server. If there is a call to the same address, but on the 21st port, then such a packet will be rejected by the router.
Routers allow you to create multiple static port forwarding. So, on one virtual server, you can open several ports at once or create several virtual servers with different IP addresses. However, with static port forwarding, you cannot forward a single port to multiple IP addresses, which means that a port can only correspond to one IP address. Thus, it is impossible, for example, to configure several Web servers with different IP addresses to do this, you will have to change the default Web server port and, when accessing port 80, specify the changed Web server port as Private Port in the router settings.
Most router models also allow you to set static redirection of a group of ports, that is, assign a group of ports to the IP address of the virtual server at once. This feature is useful if you need to ensure the operation of applications that use a large number of ports such as gaming or audio/video conferencing. The number of forwarded port groups in different router models is different, but, as a rule, there are at least ten of them.
Static port forwarding only partially solves the problem of access from an external network to local network services protected by a NAT device. However, there is also an inverse problem to provide local network users with access to an external network through a NAT device. The fact is that some applications (for example, Internet games, video conferencing, Internet telephony, and others that require the simultaneous establishment of multiple sessions) are not compatible with NAT technology. In order to solve this problem, so-called dynamic port forwarding is used, which is set at the level of individual network applications.
If the router supports this function, you must set the internal port number (or port interval) associated with a particular application (usually denoted by Trigger Port), and the number external port(Public Port), which will be mapped to the public port.
When dynamic port forwarding is enabled, the router monitors outgoing traffic from the internal network and remembers the IP address of the computer from which this traffic originated. When data flows back into the local segment, port forwarding is enabled and the data is allowed in. When the transfer is completed, the redirect is disabled, as a result of which any other computer can create a new redirect to its own IP address.
Dynamic port forwarding is mainly used for services that require short-lived requests and data transfers, because if one computer applies port forwarding this port, then another at the same time cannot use the same port forwarding. If you need to configure the work of applications that need a constant stream of data and which occupy the port for a long time, then dynamic redirection does not help much. However, in this case, it is also possible to solve the problem by using a demilitarized zone.
DMZ zone
demilitarized zone (DMZ) is another way to forward ports. This opportunity provides most modern routers. When you place an internal LAN computer in the DMZ, it becomes transparent to NAT. In fact, this means that the computer on the internal network is virtually located before the firewall. For a PC located in a DMZ zone, all ports are redirected to one internal IP address, which allows organizing data transfer from an external network to an internal one.
If, for example, a server with an IP address of 192.168.1.10, located in the internal local network, is located in a DMZ zone, and the local network itself is protected by a NAT device, then a request received from the external network at the address of the WAN port of the router will be forwarded to any port to the IP address 192.168.1.10, that is, to the virtual server address in the DMZ zone.
Authentication Methods
Currently, there are many user authentication technologies supported by routers. However, if we talk about SOHO class switches, then the most common authentication methods are the following:
Use of password and username;
MAC address application;
Using the PPPoE protocol.
The use of a password and username is typical for dial-up connections where the router has an additional serial port for connecting an analog modem. In this case, as with the traditional dial-up connection using an analog modem, the router's serial port configuration specifies the provider's phone number, username, and password.
Using MAC address authentication is quite rare and involves linking the connection to the MAC address of the router. The meaning of this technology is quite simple: each network device has its own unique MAC address 6 bytes long, or 12 hexadecimal digits. The identity of the user is verified by the ISP using a request for the MAC address of the router.
Authentication by MAC address has one pitfall: when you connect the modem to a new router or to a computer, the connection stops working. To prevent this from happening, many router models allow you to set an external MAC address.
The use of PPPoE (Point-to-Point Protocol over Ethernet) for user authentication is supported by almost all models of modern routers. This protocol is an extension of the PPP protocol, which was specifically designed to use TCP/IP over serial connections, such as dial-up connections. In fact, this protocol offers a mechanism for encapsulating TCP packets for their transmission over serial connections. For example, the PPP protocol is used to organize dial-up access to the Internet.
PPPoE (like PPP) is not a pure authentication protocol, but the authentication mechanism can be considered as an integral part of this protocol. PPPoE authentication requires a username and password.
DHCP server
any modern router can not only be a DHCP client, but can also have a built-in DHCP server, which allows you to automatically assign IP addresses to all clients on the internal network. The DHCP server settings usually specify the beginning and end of the range of allocated IP addresses. In addition, sometimes you can specify IP addresses in the specified range that will not be dynamically assigned to clients.
PPTP defines a call control protocol that allows a server to control remote dial-up access through telephone networks public domain (PSTN) or digital channels(ISDN) or initialize outgoing dial-up connections. PPTP uses the Generic Route Encapsulation (GRE) mechanism to transport PPP packets while providing flow control and network congestion. Data security in PPTP can be provided using the IPsec protocol.
L2TP
Layer 2 Tunneling Protocol is a combination of PPTP and Layer 2 Forwarding (L2F) handover protocol developed by Cisco. L2F protocol provides protocol tunneling link layer using higher layer protocols such as IP.
The L2F and PPTP protocols have similar functionality, so Cisco and Microsoft decided to jointly develop a single standard protocol, which was called the second layer tunnel protocol.
IPsec
IPsec is a protocol for securing network traffic by using encryption algorithms at the IP layer. This protocol provides two modes of operation: transport and tunnel. In transport mode, IPsec is applied to the contents of IP packets while leaving their original headers visible. Tunnel mode encapsulates original IP packets into IPsec packets with new IP headers and allows you to effectively hide the original IP packets.
VPN modes of operation
There are two modes of VPN operation: Pass Through and Active. In the first case, the router transmits incoming and outgoing VPN traffic without interference, passing encapsulated data packets through itself without viewing their contents. If the router supports VPN Pass Through mode, then you only need to configure the connection on VPN clients (computers on the internal network) so that clients from the internal network can freely connect to VPN server outside. However, there can be problems when using NAT and VPN tunnels together.
In active mode, the router acts as a server and can establish a VPN connection to a host on the local network, to other gateways and routers, or in both directions.
Conclusion
In this article, we have considered only the most common features of modern SOHO class routers. Many router models also support other features that, despite the different names, have the same purpose. For example, it can be the ability to block certain URLs, disable the response to scanning with the Ping command, put the router in Stealth mode, in which it becomes invisible from the external network, and much more.
At correct setting the router is quite capable of providing reliable protection for the internal network. In addition, its use is more economical than using a PC as a router (if, of course, the prices of the necessary software are taken into account).
