Protocols implemented at the Network layer that carry user data include:
- Internet Protocol version 4 (IPv4)
- Internet Protocol version 6 ( IPv6)
- Novell packet interworking ( IPX)
- AppleTalk
- Network Service without Connection Establishment ( CLNS/DECnet)
The Internet Protocol (IPv4 and IPv6) is the most widely used Layer 3 data transfer protocol, which will be the focus of the following. Discussion of other protocols will only be superficial.
IP Protocol - An Example of a Network Layer Protocol
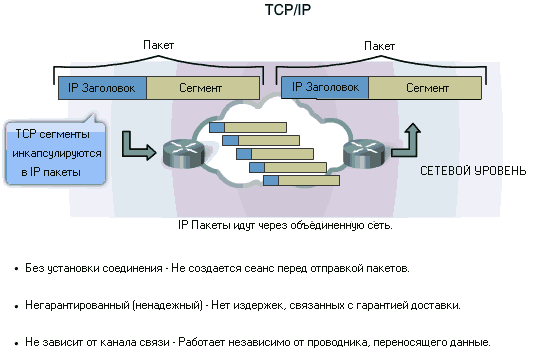
Role of IPv4
As shown in the figure, the Network Layer services implemented in the TCP/IP protocol stack include Internet Protocol (IP). Version 4 of IP (IPv4) is currently the most widely used version of IP. This is the only Layer 3 protocol that is used to transmit user data over the Internet and will be taken as an example. network layer protocols in this and subsequent articles.
Version 6 of IP (IPv6) is being developed and implemented in some areas. IPv6 will work alongside IPv4 and may replace it in the future. The services provided by IP, as well as the packet header structure and content, are defined by either IPv4 or IPv6. These services and packet structure are used to encapsulate UDP datagrams or TCP segments for their passage through the internetwork.
The characteristics of each protocol are different. Understanding these characteristics will allow you to understand the operation of the services described by the respective protocol.
The Internet Protocol was designed as a low overhead protocol. This provides only the functionality needed to deliver a packet from source to destination over a system of interconnected networks. The protocol was not designed to monitor and control the flow of packets. These functions are performed by other protocols at other layers.
Main characteristics of IPv4:
- Connectionless - No sessions are established before packets are sent.
- Non-guaranteed delivery (unreliable) - No additional overhead is used to guarantee the delivery of packets.
- Environment independent - Operates independently of the medium carrying the data.
The network layer serves to form a unified transport system, which unites several networks with different principles of information transfer between end nodes.
Functions network layer:
Delivery of data between networks
Routing Features
Selecting the best path according to the data transfer criteria.
Data flow control to prevent congestion
Coordination of different technologies at the internetwork level
Traffic filtering
Flexible addressing
Network layer protocols:
- IP/IPv4/IPv6 (Internet Protocol).
IPX (Internetwork Packet Exchange, internetworking protocol).
CLNP (network protocol without organization of connections).
IPsec (Internet Protocol Security).
ICMP ( Internet Control Message Protocol ).
RIP (Routing Information Protocol).
OSPF (Open Shortest Path First).
ARP (Address Resolution Protocol).
router(router) is a collection of a certain number of ports, each of which is connected to a certain subnet, while each port is considered as a separate full-fledged node of the corresponding subnet.
The router performs some of the functions of a bridge, such as topology analysis, filtering, and packet forwarding. However, unlike bridges, routers can direct packets to specific networks, analyze network traffic, and quickly adapt to network changes.
Routers implement the routing function based on the information that is in the routing table.
Routing tables and protocols
Databases are used by routers to store information about host addresses and network status. Routing table databases contain the addresses of other routers. Routers configured for dynamic routing automatically update these tables by regularly exchanging addresses with other routers. Routers also exchange information about network traffic, network topology, and the state of network links. Each router store this information in the network state database.
When a packet is received, the router parses the protocol address for values, such as the IP address in the TCP/IP protocol packet. The forwarding direction is determined based on the metric used, i.e., taking into account information about the state of the network and the number of hops required to transfer the packet to the target node. Routers that work with only one protocol (such as TCP/IP) maintain only one address database. A multiprotocol router maintains an address database for each supported protocol (for example, databases for TCP/IP and IPX/SPX networks).
Two protocols are commonly used to communicate between routers in the local system: RIP and OSPF.
RIPprotocol
Routers use the Routing Information Protocol (RIP) to determine the minimum number of hops between them and other routers, after which this information is added to each router's table. The information about the number of hops is then used to find the best route to forward the packet.
RIP protocol belongs to the group of protocols "distance vector routing », who operates hops(relay "jumps") asrouting metrics . The RIP protocol uses the following routing table construction scheme. Initially, each router's routing table includes routes only for those subnets that are physically connected to the router. Using the RIP protocol, a router periodically sends advertisements to other routers containing information about the contents of its own routing table. RIP uses broadcast IP packets to send announcements. Each router sends these announcements periodically at 30 second intervals.
Advantages:
- ease of configuration.
Flaws:
The presence of a hard limit on the size of the network, protocol R I P can be used in a network with no more than 15 routers.
- Each default RIP router broadcasts its full routing table to the network once every 30 seconds, loading low-speed communication lines quite heavily.
OSPF
Open Shortest Path First (OSPF) is a protocol for dynamic routing , which is based on link state tracking technology and uses to find the shortest pathDijkstra's algorithm . OSPF belongs to the Link State Protocols group.
Description of the protocol
1. Routers exchange hello packets through all interfaces on which OSPF is enabled. Routers that share a common data link become neighbors when they agree on certain parameters specified in their hello packets.
2. At the next stage of the protocol, routers will try to enter the adjacency state with routers that are within direct communication with it (at a distance of one hop). The transition to the adjacency state is determined by the type of routers exchanging hello packets and the type of network over which the hello packets are transmitted. OSPF defines several types of networks and several types of routers. A pair of routers in an adjacency state synchronizes the link state database with each other.
3. Each router sends a link-state advertisement to the routers with which it is in an adjacency state.
4. Each router that receives an advertisement from an adjacent router records its information in the router's link state database and sends a copy of the advertisement to all other adjacent routers.
5. When advertising across a zone, all routers build an identical router link state database.
6. Once the database is built, each router uses Dijkstra's algorithm to compute a loop-free graph that will describe the shortest path to every known destination, with itself as the root. This graph is a shortest path tree.
7. Each router builds a routing table from its shortest path tree.
One of its main advantages (compared to RIP ) is that when it is used, the router forwards only that part of the routing table that belongs to its nearest links, such a sending is called a "router link state message".
ARP(address Resolution Protocol- address determination protocol) - a network layer protocol designed to determine MAC addresses by known IP address.
Principle of operation.
1. The host that needs to map its IP address to local address, generates an ARP request, attaches it to the frame of the link layer protocol, indicating a well-known IP address in it, and broadcasts the request.
2. All nodes on the local network receive an ARP request and compare the IP address specified there with their own.
3. If they match, the node generates an ARP response, in which it indicates its IP address and its local address, and sends it already directed, since the sender specifies his local address in the ARP request.
Address translation is done by looking up the table. This table, called the ARP table, is stored in memory and contains rows for each host on the network. The two columns contain the IP and Ethernet addresses. If an IP address needs to be converted to an Ethernet address, then the entry with the corresponding IP address is looked up.
routing table.
Methods for building a routing table.
static routing. All routes are registered and changed manually by the system administrator. This is the easiest way to organize routing. However, it is suitable only for small networks, the changes in the structure of which occur quite rarely.
dynamic routing. The routing table is built using special routing protocols. The administrator's participation in this process is minimal and comes down to the initial configuration of the routers.
|
Destination network address |
Port address next. router |
Router output port address |
Distance |
|
LAN 1 |
M3(1) |
||
|
GAN 1 |
M1(1) |
M3(1) |
|
|
LAN 2 |
M4(1) |
M3(1) |
|
|
GAN 2 |
M3(2) |
0 V1 |
|
|
LAN3 |
M6(1) |
M3(2) |
0 v 2 |
There are also other columns in the routing table:
5 - column with mask.
6 - route lifetime - this is the time after which (if the information was not updated by routers) it is no longer valid.
7 - record source;
8 - route state
Network layer functions:
The networks that make up the internetwork can be built on the basis of various network technologies. Each network technology is quite sufficient to organize the exchange of information within one subnet, but does not allow the interaction of computers on this subnet with computers on subnets based on other technologies. This is due to the possible incompatibility of protocols and addressing methods defined by different technologies. Therefore, to ensure the functioning of interconnected networks, tools are required that are a "superstructure" over link layer, allowing you to abstract from specific solutions embedded in network technologies. The network layer of the OSI model acts as such an add-on.
It is obvious that devices of this level, designed to combine networks, must be much more complex than link-level devices. Secondly, these devices must provide targeted data transfer between subscribers across the subnets of the composite network (that is, determine the data path) so as not to cause congestion of the composite network. The process of determining the path of data through the subnets of a composite network is called routing, and the devices that connect networks and solve the listed tasks are called routers.
So, for successful information exchange in interconnected networks, network-level tools must solve the following tasks:
- provide a unified addressing system independent of network technology that allows addressing individual networks and nodes;
- determine the path (sequence of networks) that data must follow in order to reach the recipient;
- provide end-to-end data transmission through networks with different technologies.
Currently, there are various network layer protocols. The main protocol used on the Internet is IP.
IP protocol
IP (Internet Protocol) is part of the TCP / IP protocol stack and is the main network layer protocol used on the Internet and provides a single logical addressing scheme for devices on the network and data routing
There are several versions of the IP protocol, reflecting the changing requirements for functions with the development of the Internet. Currently, version 4 is used as the standard, although version 6 is gradually being introduced. This section discusses the technological solutions of the standard version 4.
To perform its functions, the protocol defines its own format package. The main information fields of the packet header are:
- IP addresses sender and recipient – designed to identify the sender and recipient (see IP addressing);
- Packet lifetime(Time To Live, TTL) - determines the time that an IP packet can be in the network, and is designed to prevent "cluttering" the network with "stray packets";
- fields intended for packet fragmentation (see IP fragmentation);
- fields intended to control packet processing (packet and header length, header checksum, type of service, etc.).
From the point of view of the IP protocol, the network is considered as a logical collection of interconnected objects, each of which is represented by a unique IP address, called knots(IP nodes) or hosts(host). The key word here is "logical", since the same physical device (computer, router, etc.) can have several IP addresses, i.e. correspond to several nodes of the logical network. This situation usually occurs if the physical device has several data devices (network adapters or modems), since at least one unique IP address must be configured for each of them. Although it is not uncommon for a computer (or other device) that has a single network adapter or modem to have multiple IP addresses assigned to it.
If a physical device has multiple IP addresses, then it is said to have multiple interfaces, i.e. multiple "logical connections" to the network.
IP addressing
IP address is a unique numeric address that uniquely identifies a node, group of nodes, or network. An IP address is 4 bytes long and is usually written as four numbers (so-called "octets") separated by periods - W.X.Y.Z , each of which can take values in the range from 0 to 255, for example, 213.128.193.154.
In order for a computer to participate in network communication using the IP protocol, it must be assigned a unique IP address.
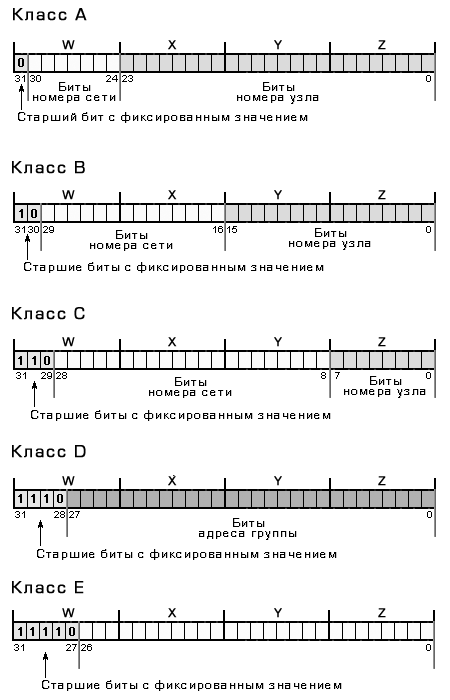
IP address classes
They wrote about classes and IP addressing.
There are 5 classes of IP addresses - A, B, C, D, E. An IP address belongs to one class or another is determined by the value of the first octet (W). The correspondence between the values of the first octet and the address classes is shown below.
IP addresses of the first three classes are intended for addressing individual hosts and individual networks. Such addresses consist of two parts - the network number and the host number. This scheme is similar to that of postal codes - the first three digits encode the region, and the rest - the post office within the region.
The advantages of the two-level scheme are obvious: firstly, it allows you to address entirely separate networks within the composite network, which is necessary to ensure routing, and secondly, to assign numbers to nodes within the same network independently of other networks. Naturally, computers that are part of the same network must have IP addresses with the same network number.
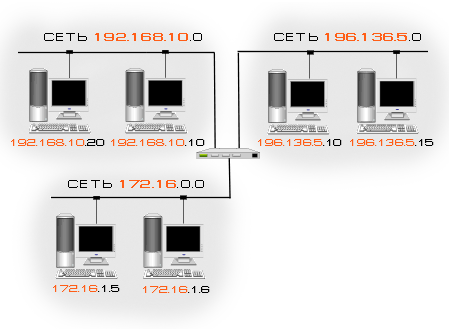
If two computers have IP addresses with different network numbers (even if they belong to the same physical network), then they will not be able to communicate with each other directly: they need a router to communicate (see the IP Routing section).
IP addresses of different classes differ in the bitness of the network and host numbers, which determines their possible range of values. The following table shows the main characteristics of class A, B and C IP addresses.
For example, the IP address 213.128.193.154 is a class C address, and belongs to node number 154 located on the network 213.128.193.0.
The addressing scheme, defined by classes A, B, and C, allows data to be sent either to a single host or to all computers on a single network (broadcast). However, there is a network software, which needs to send data to a specific group of nodes that are not necessarily included in the same network. In order for programs of this kind to function successfully, the addressing system must provide for so-called group addresses. Class D IP addresses are used for these purposes.
The Class E address range is reserved and is not currently in use.
Binary notation for IP addresses
Along with the traditional decimal form of IP addresses, the binary form can also be used, which directly reflects the way the address is represented in the computer's memory. Since an IP address is 4 bytes long, it is represented in binary form as a 32-bit binary number (i.e. a sequence of 32 zeros and ones). For example, the binary form of 213.128.193.154 is 11010101 1000000 11000001 10011010. Using the binary form of an IP address, it is easy to determine the IP address class schemes:
Special IP addresses
The IP protocol assumes the presence of addresses that are treated in a special way. These include the following:
1. Addresses whose first octet value is 127. Packets directed to such an address are not actually transmitted to the network, but are processed by the software of the sending host. Thus, the node can send data to itself. This approach is very convenient for testing network software in conditions where it is not possible to connect to the network.
2. Address 255.255.255.255. A packet whose destination contains the address 255.255.255.255 must be sent to all nodes of the network where the source is located. This type of broadcast is called limited broadcast. In binary form, this address is 11111111 11111111 11111111 11111111.
3. Address 0.0.0.0. It is used for service purposes and is treated as the address of the node that generated the packet. The binary representation of this address is 00000000 00000000 00000000 00000000
Additionally, addresses are interpreted in a special way:
Using Masks for IP Addressing
The scheme of dividing an IP address into a network number and a host number, based on the concept of an address class, is rather rough, since it involves only 3 options (classes A, B and C) for distributing address bits to the corresponding numbers. Let's consider the following situation as an example. Let's say that some company connecting to the Internet has only 10 computers. Since Class C networks are the lowest possible number of hosts, this company would have to obtain a range of 254 addresses (one Class C network) from the IP address distribution organization. The inconvenience of this approach is obvious: 244 addresses will remain unused, since they cannot be allocated to computers of other organizations located in other physical networks. If the organization in question had 20 computers distributed over two physical networks, then it would have to be allocated a range of two class C networks (one for each physical network). In this case, the number of "dead" addresses will double.
For a more flexible definition of the boundaries between the digits of the network and host numbers within the IP address, so-called subnet masks are used. The subnet mask is a special 4-byte number that is used in conjunction with an IP address. The "special form" of the subnet mask is as follows: the binary bits of the mask corresponding to the bits of the IP address reserved for the network number contain ones, and the bits corresponding to the bits of the host number contain zeros.
The subnet mask must be specified when configuring the IP protocol plug-in on each computer along with the IP address
The use of a subnet mask in conjunction with an IP address eliminates the use of address classes and makes the entire IP addressing system more flexible. So, for example, the mask 255.255.255.240 (11111111 11111111 11111111 11110000) allows you to split the range of 254 IP addresses belonging to the same class C network into 14 ranges that can be allocated to different networks.
For the standard division of IP addresses into the network number and host number defined by classes A, B and C, the subnet masks are:
IP address distribution
Since each Internet node must have a unique IP address, it is certainly important to coordinate the distribution of addresses to individual networks and nodes. The Internet Corporation for Assigned Names and Numbers (ICANN) performs this stewardship role.
Naturally, ICANN does not solve the problem of allocating IP addresses to end users and organizations, but distributes address ranges between large Internet Service Provider organizations, which, in turn, can interact with smaller providers as well as with end users. So, for example, ICANN delegated the functions of distributing IP addresses in Europe to the RIPE Coordination Center (RIPE NCC, The RIPE Network Coordination Center, RIPE - Reseaux IP Europeens). In turn, this center delegates part of its functions to regional organizations. In particular, Russian users are served by the Regional Network information Center"RU-CENTER".
IP routing
IP Routing– the process of choosing a path for transmitting a packet in a network. A path (route) is a sequence of routers that a packet passes through on its way to its destination. An IP router is a special device designed to connect networks and determine the path of packets in a composite network. The router must have several IP addresses with network numbers corresponding to the numbers of the networks being combined.
An IP router can be a computer whose system software allows IP routing. In particular, the router can be organized on the basis of a computer running any of the operating systems of the family Microsoft Windows server.
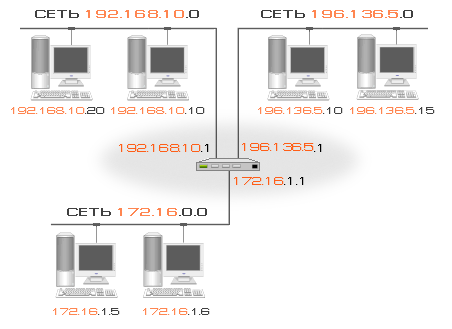
Routing is done at the source host at the time the IP packet is sent, and then at the IP routers.
The principle of routing on the sender node looks quite simple. When it is required to send a packet to a host with a specific IP address, the sending host allocates network numbers using a subnet mask from its own IP address and the IP address of the recipient. Next, the network numbers are compared, and if they match, then the packet is sent directly to the recipient, otherwise, to the router whose address is specified in the IP protocol settings.
If the host does not have a router address configured, it will not be possible to deliver data to a recipient located on a different network.
The path selection on the router is based on the information provided in the routing table. The routing table is a special table that maps the IP addresses of networks to the addresses of the following routers to which packets should be sent in order to deliver them to these networks. A mandatory entry in the routing table is the so-called default route, which contains information on how to route packets to networks whose addresses are not present in the table, so there is no need to describe routes for all networks in the table. Routing tables can be built "manually" by the administrator or dynamically, based on the exchange of information that routers carry out using special protocols.
IP fragmentation
As you know, for different network technologies, the MTU value defined for data frames may differ. Therefore, when transforming frames on a router, it may be necessary to split the nested IP packets into smaller packets.
To divide packets into fragments, the IP module installed on the router creates a number of new packets based on it (according to the length of the original packet and the MTU value for the network where the data should be transmitted). In order for the data to be correctly collected by the recipient, a special numeric identifier is placed in the headers of new IP packets, which makes it possible to unambiguously determine that these packets are fragments of one large packet. In addition, the headers also indicate the position of the fragments in the source package, which helps ensure that the recipient is in the correct order of assembly.
Auxiliary Protocols of the Network Layer of the TCP/IP Stack
The main functions of the IP protocol are to provide a single addressing scheme, independent of the addressing principles determined by network technologies (link layer addressing), as well as data transmission over a composite network (routing and packet fragmentation). However, this is not enough to organize real interaction - there are still a number of problems.
The first problem is the following. In order to transmit data over a network, the IP protocol software creates a packet and passes it to the data link layer. At the same time, the link layer means for forming a data frame needs a recipient address, and not a logical IP address, but a MAC address that can be correctly recognized network adapter receiving computer. However, the IP protocol specification does not provide a mechanism for determining the correspondence between hardware and IP addresses. This function is performed by the auxiliary network layer protocol ARP (Address Resolution Protocol), which is part of the TCP / IP protocol family.
Another serious problem is that if there are any problems during the processing of an IP packet on the router, for example, the "packet time to live" has expired, then the sender will not know about them, since the "feedback" mechanism is also not provided for by the IP protocol specification. . To solve this problem, a special network layer protocol ICMP (Internet Control Message Protocol) is used, which is part of the TCP / IP protocol stack, and provides the transfer of control information and error information.
The TCP/IP family of protocols also provides a number of other support protocols, such as dynamic routing protocols, that allow information to be exchanged between routers to automate the building of routing tables.
Summary
- The network layer is a functional add-on over the link layer, which provides the ability to combine networks based on different network technologies;
- The main functions of the network layer are: providing unified system addressing, independent of the addressing methods determined by a particular network technology, routing of data packets transmitted over the network, as well as ensuring end-to-end data transmission through a composite network;
- devices designed to combine networks at the network level are called routers;
- the main network layer protocol is the IP protocol;
- the IP protocol defines the addressing scheme of network nodes and provides routing and packet fragmentation;
- An IP address is a 4-byte number that uniquely identifies a network node and consists of two parts - a network number and a node number;
- depending on how many digits within the IP address are allocated for network and host numbers, addresses are divided into classes;
- for flexible separation of the IP address into network and host numbers, a subnet mask can be used - a 4-byte number of a special form;
- when sending an IP packet, each network node compares the recipient's network number with its own, and if these numbers match, the packet is sent directly to the recipient, otherwise to the router;
- the router determines the path along which the packet should be transmitted using the routing table;
- to successfully transfer data between networks built on the basis of different technologies, IP routers can fragment packets in accordance with the restrictions set by the network technology of the destination network;
- to provide real interaction with the IP protocol, auxiliary protocols of the network layer are used.
THEME: Network layer of data transfer. Network layer protocols.
network layer (networklayer) - level of interconnection(internetworking) – (the third level of the OSI model), serves to form a single transport subsystem that combines several networks. At the same time, networks can use completely different principles for transmitting messages between end nodes and have an arbitrary communication structure.
Data that enters the network layer and that needs to be sent over the composite network is provided with a network layer header.
The data together with the header form a packet. The network layer packet header carries information about the number of the network to which the packet is intended, as well as other service information necessary for the successful transition of the packet from a network of one type to a network of another type. Such information may include, for example:
Packet fragment number required for successful assembly operations - disassembly of fragments when connecting networks with different maximum packet sizes;
Packet lifetime, indicating how long it travels over the internet, this time can be used to kill "lost" packets;
Quality of Service is a route selection criterion for inter-network transmissions - for example, a node - a sender may require a packet to be transmitted with maximum reliability, possibly at the expense of delivery time.
The main network layer protocols are network protocols (for example, IP or IPX) and routing protocols ( RIP, OSPF, BGP and etc.).
An auxiliary role is played by such protocols as - the protocol of inter-network control messages ICMP ( Internet Control Message Protocol ) , which is designed to exchange information about errors between network routers and the source node of the packet. With the help of special messages, ICMP reports about the impossibility of delivering a packet or about a packet timeout, about a change in the forwarding route, about the state of the system, etc. Group control protocol IGMP and address resolution protocol ARP.
Network Protocols and routing protocols are implemented as software modules on end nodes - computers, often called hosts and on intermediate nodes - routers, called gateways.
Network protocols are designed to transfer user data, while routing protocols collect and transmit over the network only service information about possible routes. Network protocols actively use the routing table in their work, but they do not build it or maintain its contents. These functions are performed by routing protocols. Routing protocols can be built on the basis of different algorithms that differ in the way they build routing tables, how to choose the best route, and other features of their work. There are single-hop and multi-hop routing algorithms.
At the network level, a correspondence is also established between the IP address and the hardware address (MAC address). The establishment is carried out by the address resolution protocol - ARP, which for this purpose looks through the ARP - tables. If the desired address is missing, then a broadcast ARP request is performed.
Network layer functions.
The functions of the network layer include the following tasks:
1. Packet transmission between end nodes in composite networks. The network layer acts as a coordinator that organizes the work of all subnets that lie in the path of the packet's progress through the composite network. A composite network (Internet) is a collection of several networks, also called subnets, that are interconnected by routers.
2. The choice of the packet transmission route, the best according to some criterion.
3. Negotiation of different link layer protocols used in separate subnets of the composite network. To move data within subnets, the network layer refers to the technologies used on those subnets.
4. At the network level, one of the most important functions of the router is performed - traffic filtering. Routers allow administrators to set different filtering rules. For example, to prohibit the passage of all packets to the corporate network, except for packets coming from the subnets of the same enterprise. Filtering in this case occurs by network addresses. The router software can implement various packet queuing disciplines, as well as various priority service options.
5. At the network level, the checksum is checked, and if the packet arrived damaged, then it is discarded (the network level does not deal with error correction). The packet lifetime is also checked - whether it exceeds the allowable value (if it exceeded, then the packet is discarded).
Routing principles.
The network layer provides the ability to move packets through the network using the route that is currently more rational.
A route is a sequence of routers that a packet must traverse from the sender to the destination. In complex multilayer networks, there are almost always multiple alternative routes for packets to travel between two end nodes. The task of choosing a route is solved by both end nodes - computers and intermediate nodes - routers based on routing tables. Routers usually automatically create routing tables by exchanging overhead information; for end nodes, routing tables are often created manually by administrators and stored as permanent files on disks. Routers have multiple ports for connecting networks, each router port has its own network address and its own local address. If the router has a control unit, then this unit has its own address, at which it is accessed by a central control station located somewhere in the composite network.
Routers use routing protocols to map links in varying degrees of detail. Based on this information, for each network number, a decision is made about which next router should forward packets destined for this network in order for the route to be rational. The results of these decisions are entered in the routing table.
Routing protocols include protocols such as RIP, OSPF, BGP; ICMP Internet Control Message Protocol.
Large networks are divided into autonomous systems, autonomous systems are networks attached to the backbone, having their own administration and their own routing protocols.
Routing protocols are divided into external and internal. External protocols (EGP, BGP) carry routing information between autonomous systems, while internal protocols (RIP, OSPF) are used within a particular autonomous system.
The BGP protocol allows you to recognize the presence of loops between autonomous systems and exclude them from intersystem routes.
The RIP protocol (Routing Internet Protocol) is one of the earliest protocols for the exchange of routing information and is still extremely common due to the simplicity of routing. The RIP protocol has several versions, for example, for the IP protocol, there is a version of RIPv1 that does not support masks and a version of RIPv2, this is a protocol that conveys information about network masks. Using the RIP protocol, a routing table is built. The first column of the table lists the numbers of networks included in the Internet. On each line, the network number is followed by the network address of the port of the next router to which the packet should be sent in order for it to move towards the network with this number along a rational route. The third column indicates the output port number of this router. The fourth column indicates the distance to the destination network.
Table 1. Routing table
As a distance to the destination network, the RIP protocol standards allow various kinds of metrics: hops, metrics that take into account throughput, latency, and network reliability. The simplest metric is the number of hops, that is, the number of intermediate routers that a packet needs to traverse to reach its destination network. The RIP protocol works successfully in relatively small networks with up to 15 routers.
OSPF (Open Shortest Path Fist) protocol was developed to efficiently route IP packets in large networks with complex topology, including loops. It is based on a link state algorithm that is highly resistant to network topology changes. When choosing an OSPF route, routers use a metric that takes into account the throughput of the constituent networks. The OSPF protocol takes into account the quality of service bits, a separate routing table is built for each type of quality. The OSPF protocol has a high computational complexity, so it most often runs on powerful hardware routers.
Over the past few decades, the size and number of networks have grown significantly. There were many types of networks in the 80s. And practically each of them was built on its own type of hardware and software, often incompatible with each other. This led to significant difficulties when trying to connect several networks (for example, a different type of addressing made these attempts almost hopeless).
This problem was considered by the International Organization for Standardization ( ISO ) and it was decided to develop a network model that could help developers and manufacturers network equipment and software work together. As a result, in 1984, the OSI model was created - open systems interaction model(Open Systems Interconnected). It consists of seven levels into which the task of organizing network interaction is divided. They are schematically presented in table 16.1.
| Level number | Level name | Unit of information |
|---|---|---|
| Layer 7 | Application layer | data |
| Layer 6 | Executive level | data |
| Layer 5 | Session level | data |
| Layer 4 | transport layer | Segment |
| Layer 3 | network layer | package |
| Layer 2 | Data transfer layer | frame |
| Layer 1 | Physical layer | Bit (bit) |
Although there are various models of networks today, most developers adhere to this generally accepted scheme.
Consider the process of transferring information between two computers. Software generates a layer 7 (application) message consisting of a header and payload. The header contains service information that is necessary for the destination application layer to process the information being sent (for example, it can be information about the file that needs to be transferred, or the operation that needs to be performed). After the message has been generated, the application layer sends it "down" to the presentation layer (layer 6). The received message, consisting of the layer 7 overhead and payload, is presented as a single unit to layer 6 (although layer 6 can read the layer 7 overhead). The presentation layer protocol performs the necessary actions based on the data received from the application layer header and adds its layer header, which contains information for the corresponding (6th) destination layer. The resulting message is passed further "down" to the session layer, where overhead is also added. The padded message is passed on to the next transport layer etc. at each subsequent level (this is schematically shown in Fig. 16.1). In this case, service information can be added not only to the beginning of the message, but also to the end (for example, at the 3rd level, Fig. 16.2). The result is a message containing service information of all seven levels.
Rice. 16.1.
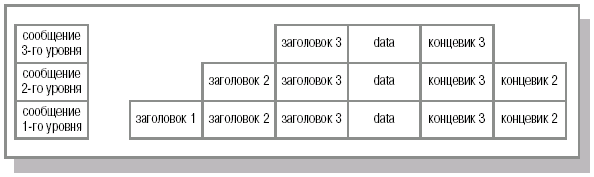
Rice. 16.2.
The process of "wrapping" transmitted data with overhead information is called encapsulation ( encapsulation).
This message is then transmitted through the network in the form of bits. A bit is the smallest piece of information that can be either 0 or 1 . Thus, the entire message is encoded as a set of zeros and ones, for example, 010110101 . In the simplest case, at the physical layer for transmission, a electrical signal, consisting of a series of electrical impulses (0 - no signal, 1 - there is a signal). It is this unit adopted to measure the speed of information transfer. Modern networks usually provide channels with a throughput of tens and hundreds of Kbps and Mbps.
The recipient at the physical layer receives the message in the form of an electrical signal (Fig. 16.3). Next, a process occurs that is the reverse of encapsulation, decapsulation ( decapsulation). At each level, service information is parsed. After decapsulating the message at the first level (reading and processing of the service information of the 1st level), this message containing the service information of the second level and data in the form of payload data and service information of higher levels is transmitted to the next level. At the channel (2nd) level, the system information is analyzed again and the message is transmitted to the next level. And so on until the message reaches the application layer, where it is transmitted as final data to the receiving application.
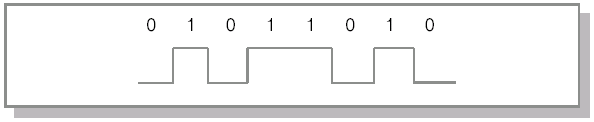
Rice. 16.3.
An example is a browser call to a web server. The client application - the browser - generates a request to receive a web page. This request is passed by the application to layer 7 and then sequentially to each layer of the OSI model. Having reached the physical layer, our initial request "acquires" the service information of each layer. After that, it is transmitted over the physical network (cables) in the form of electrical impulses to the server. The server parses the corresponding system information of each level, as a result of which the sent request reaches the web server application. There it is processed, after which a response is sent to the client. The process of sending a response is similar to sending a request, except that the message is sent by the server and received by the client.
Because each layer of the OSI model is standardized, consumers can share hardware and software various manufacturers. As a result web server running the Sun Solaris operating system can serve an HTML page to an MS Windows user.
Of course, compatibility can only be ensured up to a certain level. If one machine transmits data in the form of radio waves, and the other in the form of light pulses, then their interaction without the use of additional equipment is impossible. Therefore, the concept of network-independent and network-dependent levels was introduced.
The three lower layers - physical, channel and network - are network-dependent. For example, changing Ethernet to ATM entails a complete change in the protocol of the physical and data link layers.
The top three levels - applications, representative and session - are focused on application tasks and practically do not depend on the physical technology of building a network. Thus, the transition from Token Ring to Ethernet does not require changes in the listed levels.
transport layer is intermediate between the network-dependent and network-independent levels. It hides all the details of the functioning of the lower levels from the upper ones. This allows the application developer not to think about technical means implementation of network message transport.
Together with the name message (message) in ISO standards, the term is used to denote a unit of data protocol data unit(Protocol Data Unit , PDU ). In different protocols, other names are used, fixed by the standards, or simply traditional. For example, in the TCP / IP family of protocols, the TCP protocol divides the data stream into segments, the UDP protocol works with datagrams (or datagrams, from datagram ), the IP protocol itself uses the term packets. Often the same is said about frames or frames.
For a deeper understanding of the principles of the network, we will consider each level separately.
physical layer (layer 1)
As can be seen from the general layout of layers in the OSI model, the physical layer ( physical layer) the very first. This layer describes the communication medium. Standardized physical devices, responsible for the transmission of electrical signals (connectors, cables, etc.) and the rules for the formation of these signals. Let's take a look at all the components of this level in order.
Most of the networks are built on a cable structure (although there are networks based on the transmission of information using, for example, radio waves). Now there are different types of cables. The most common ones are:
- telephone wire;
- coaxial cable ;
- twisted pair;
- optical fiber .
The telephone cable has been used to transmit data since the advent of the first computers. The main advantage of telephone lines was the presence of an already created and developed infrastructure. With its help, you can transfer data between computers located on different continents, as easily as talking to people who are many thousands of kilometers apart. To date, the use of telephone lines also remains popular. Users who are satisfied with a small transmission speed data can access the Internet from their home computers. The main disadvantages of using a telephone cable is the small transmission speed, because the connection does not occur directly, but through telephone exchanges. At the same time, the requirement for the quality of the transmitted signal in data transmission is much higher than in the transmission of "voice". And since most analog PBXs do not cope with this task (the level of "noise" or interference, and the signal quality leaves much to be desired), the data transfer rate is very low. Although when connected to modern digital exchange you can get high reliable speed connections.
Coaxial cable used in networks a few years ago, but today it is a rarity. This type of cable is almost identical in structure to a conventional television cable. coaxial cable– the central copper core is separated by a layer of insulation from the braid. There are some differences in electrical characteristics (a TV cable uses a cable with wave resistance 75 Ohm, in the network - 50 Ohm).
The main disadvantages of this cable is the low transmission speed data (up to 10 Mbps), exposure to external interference. In addition, the connection of computers in such networks occurs in parallel, which means that the maximum possible bandwidth is divided among all users. But, compared to a telephone cable, coaxial allows you to connect closely spaced computers with much better communication quality and higher data transfer rates.
twisted pair (" twisted pair") is the most common means for transferring data between computers. In this type The cable uses a copper wire twisted in pairs, which reduces the amount of interference and interference, both when transmitting a signal through the cable itself, and when exposed to external interference.
There are several categories of this cable. Let's list the main ones. Cat 3 - was standardized in 1991, electrical characteristics allowed to support transmission frequencies up to 16 MHz, was used for data and voice transmission. The higher category, Cat 5, was specifically designed to support high speed protocols. Therefore, its electrical characteristics lie in the range up to 100 MHz. Data transfer protocols of 10, 100, 1000 Mbps work on this type of cable. To date, Cat5 cable has almost supplanted Cat 3. The main advantage of twisted pair cable over telephone and coaxial cables- higher transmission speed data. Also, the use of Cat 5 in most cases allows, without changing the cable structure, to increase performance networks (transition from 10 to 100 and from 100 to 1000 Mbps).
Optical fiber used to connect large network segments that are far apart, or in networks that require a large bandwidth, noise immunity. An optical cable consists of a central conductor of light (core) - a glass fiber surrounded by another layer of glass - a sheath that has a lower refractive index than the core. Spreading through the core, the rays of light do not go beyond its limits, being reflected from the covering layer of the shell. The light beam is usually formed by a semiconductor or diode laser. Depending on the distribution of the refractive index and on the size of the diameter of the core, they are distinguished.
