Generalized structure of a computer network
Computer networks are the highest form of multi-machine associations. Let us single out the main differences between a computer network and a multicomputer complex.
The first difference is the dimension. The composition of a multicomputer complex usually includes two, maximum three computers, located mainly in the same room. A computer network can consist of tens and even hundreds of computers located at a distance from each other from several meters to tens, hundreds and even thousands of kilometers,
The second difference is the division of functions between computers. If in a multicomputer complex the functions of data processing, data transmission and system control can be implemented in one computer, then in computer networks these features
distributed among different computers.
The third difference is the need to solve the problem of message routing in the network. A message from one computer to another in the network can be transmitted along different routes depending on the state of the communication channels connecting the computers to each other.
Combining into one complex of computer technology, communication equipment and
data transmission channels imposes specific requirements on the part of each element of a multi-machine association, and also requires the formation of special terminology.
Network subscribers- objects generating or consuming information in the network.
Subscribers networks can be individual computers, computer complexes, terminals, industrial robots, machine tools with numerical control, etc. Any network subscriber is connected to the station.
Station- equipment that performs functions related to the transmission and reception of information.
The set of subscriber and station is called subscriber system. To organize the interaction of subscribers, a physical transmission medium is required.
Physical transmission medium- communication lines or space in which electrical signals propagate, and data transmission equipment.
On the basis of the physical transmission medium is built communication network
which provides information transfer between subscriber systems.
This approach allows us to consider any computer network as a set of
subscriber systems and communication network. Generalized structure of a computer network
shown in Figure 6.3.
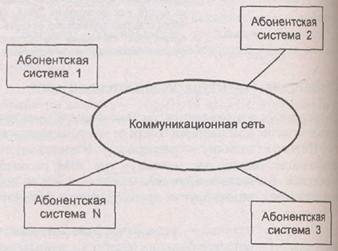 |
Rice. 63. Generalized structure
computer network
8.1. The concept of an algorithm and properties of an algorithm
248. The essence of such a property of the algorithm as efficiency is that:
249. The essence of such a property of the algorithm as mass character is that:
The algorithm must have a discrete structure (must be broken down into a sequence of individual steps)
When writing an algorithm for a specific performer, you can use only those commands that are included in the system of his commands.
The algorithm should provide a solution not to one specific problem, but to a certain class of problems of this type for all admissible values of the initial data
With the exact execution of all the commands of the algorithm, the process must stop in a finite number of steps, leading to a certain result
250. The essence of such a property of the algorithm as discreteness is that:
- the algorithm must have a discrete structure (must be broken down into a sequence of individual steps)
When writing an algorithm for a specific performer, you can use only those commands that are included in the system of his commands.
The algorithm should provide a solution not to one specific problem, but to a certain class of problems of a given type
With the exact execution of all the commands of the algorithm, the process must stop in a finite number of steps, leading to a certain result
251. The essence of such a property of the algorithm as understandability is that:
The algorithm must have a discrete structure (must be broken down into a sequence of individual steps)
- the record of the algorithm should not allow ambiguous interpretation
The algorithm should provide a solution not to one specific problem, but to a certain class of problems of a given type
With the exact execution of all the commands of the algorithm, the process must stop in a finite number of steps, leading to a certain result
252. The algorithm is:
Rules for performing certain actions
Directed graph indicating the order of execution of some set of instructions
A clear and precise order to the performer to perform a sequence of actions aimed at achieving the set goals
Computer command set
253. Specify the most complete list of ways to write algorithms:
- verbal, graphic, pseudocode, software
Verbal
Graphic, software
Verbal, software
8.2. Basic algorithmic constructions
254. An algorithm for solving a certain subproblem that is executed repeatedly is called:
Linear
branching
- cyclical
Auxiliary
255. The algorithm is called cyclic:
- if it is designed in such a way that its implementation involves repeated repetition of the same actions
If the course of its implementation depends on the truth of certain conditions;
If it is presented in tabular form
256. The algorithm is called linear:
If it is designed in such a way that its implementation involves repeated repetition of the same actions
If the order of its execution depends on the truth of certain conditions
If his commands are executed in their natural sequence, regardless of any conditions
If it includes an auxiliary algorithm
257. The algorithm includes branching if:
If it is designed in such a way that its implementation involves repeated repetition of the same actions
If the course of its execution depends on the truth of certain conditions
If his commands are executed in their natural sequence, regardless of any conditions
- if it includes an auxiliary algorithm
8.3. Examples of problem solving
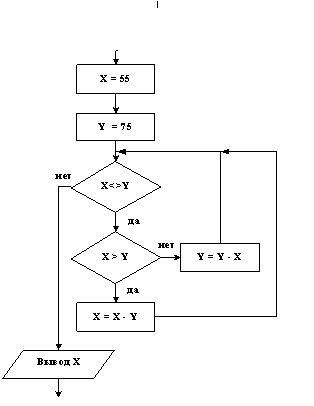
258. The result of the execution of the algorithm shown in the figure, for the value of the variable X=10 will be the number ...
259. The result of executing the algorithm shown in the figure for the value of the variable X=-10 will be the number…
260. The result of executing the algorithm shown in the figure for the value of the variable X=0 will be the number ...
261. In the above fragment of the flowchart, ...
- exchange of values of variables A and B
- exchange of values of variables B and C
- comparison of variables A, B, C
- exchange of values of variables A and C
262. After the execution of the following fragment of the algorithm, the value of the integer variable X will be equal to ...
8.4. Programming systems
263. Programming systems:
Provide a direct solution to user tasks;
- allow you to create new programs in programming languages;
Ensure the operation of all computer hardware devices and user access to them;
Provide protection from computer viruses
264. Of the following software products, programming systems are:
D) Borland Delphi
- C, D, D
265. The subroutine is called:
Independent software module
Arbitrary program fragment
A set of statements following the GOSUB statement in the program
- part of a program that serves to solve some auxiliary problem
266. Programming languages, sets of operators and visual means of which significantly depend on the features of the computer (internal language, memory structure, etc.) are called ...
- machine-oriented languages
High level programming languages
Embedded programming languages
Algorithmic languages
267. High-level programming languages do NOT include:
Algorithmic (Basic, Pascal, C),
Logic (Prolog, Lisp),
Object-oriented (ObjectPascal, C++, Java)
- machine-oriented languages
Database
9.1. Basic concepts of database theory
268. The MSAccess database management program is a software product that is part of:
operating system;
systemic software;
Database programming systems;
Application software;
Unique software.
269. Entering, editing and formatting text data allows _________ software.
- office (service)
- systemic
- instrumental
- applied
270. There is no _______ database model:
- tire
- hierarchical
- network
- relational
271.
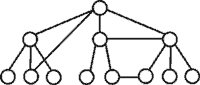
- combined
- hierarchical
- network
- relational
272. The figure shows the database model:
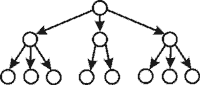
- combined
- hierarchical
- network
- relational
273. The figure shows the database model:
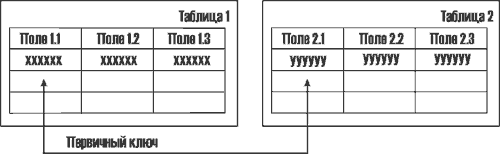
- combined
- hierarchical
- network
- relational
274. MS Access is a software product that is part of:
operating system
System software
programming systems
- application software
Unique software
9.2. Database objects. Data types.
275. The database cannot exist without an object...
- form
- report
- request
- table
276. Data sampling in the Access database management system is carried out using ...
- request
- forms
- constructor
- tables
277. The figure shows…
- subform
- report in design mode
- query in design view
- table in design view
278. The figure shows…
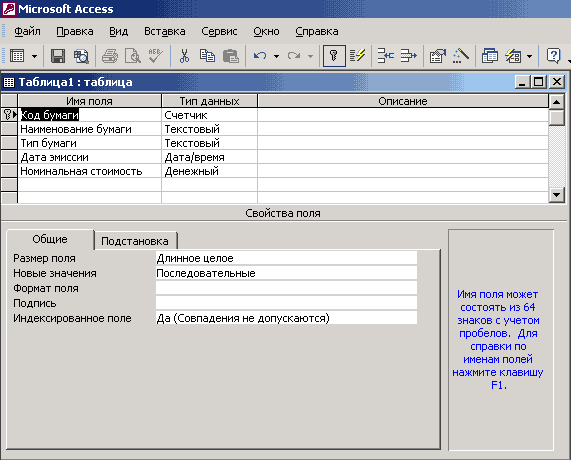
- subform
- report
- cross query
- table in design view
279. The "form" database object is for...
- data entry and visual display on the screen
- create a calculated field
- presenting table or query data in a printable format
- visual display of relationships between tables
280. To display the results of a print query, the Access database management system uses the object ...
- table
- request
- report
- page
9.3. Information-logical database model
281. The dialog box shown in the figure allows...
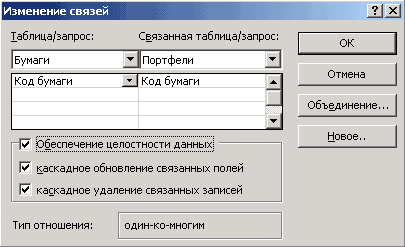
- create a cross query
- create a database report
- create a new table
- set the type of connection between database objects
282.
283. The figure shows the relationship between objects A and B, in which ...
- each instance of the first object (A) corresponds to only one instance of the second object (B) and vice versa, each instance of the second object (B) corresponds to only one instance of the first object (A)
- each instance of one object (A) can correspond to several instances of another object (B), and each instance of the second object (B) can only correspond to one instance of the first object (A)
- each instance of one object (A) can correspond to several instances of the second object (B) and vice versa, each instance of the second object (B) can also correspond to several instances of the first object (A)
284. The figure shows the relationship between objects A and B, in which ...
- each instance of the first object (A) corresponds to only one instance of the second object (B) and vice versa, each instance of the second object (B) corresponds to only one instance of the first object (A)
- each instance of one object (A) can correspond to several instances of another object (B), and each instance of the second object (B) can only correspond to one instance of the first object (A)
- each instance of one object (A) can correspond to several instances of the second object (B) and vice versa, each instance of the second object (B) can also correspond to several instances of the first object (A)
9.4. Practical tasks on the topic
285. The database "School" is presented. A query to display a list of students in grades 11, born in 1987, with grades of at least 4, contains the expression ...
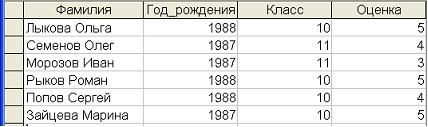
§ (Score >=4) AND (Year of Birth =1987) AND (Grade =11)
- (Score >4) AND (Year of Birth =1987) AND (Grade =11)
- (Grade =11) OR (Grade >=4) OR (Year of Birth =1987)
- (Grade >10) AND (Year of Birth =1987) AND (Score =5) AND (Score =4)
286. The database "Magic Lands" is presented. After sorting, information about NARNII will move one line down. This is possible if the sorting is done in order...
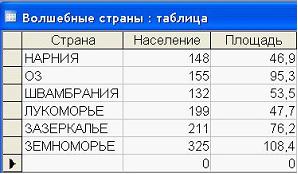
- Ascending on the AREA field
- ascending by field COUNTRY
- descending across the field AREA
- ascending in the POPULATION field
287. The figure shows the data schema:
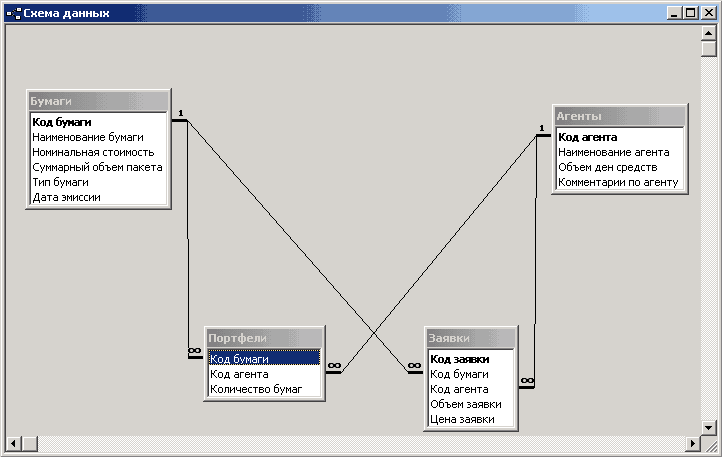
Choose the correct statements that characterize the data schema shown ...
- Paper and Ticket objects are related in a one-to-many relationship
- Papers and Agents tables do not use data from other tables
- The Securities table uses the Securities Code from the Orders table
- In the Orders table, the combination of the Securities Code and Agent Code fields is the key
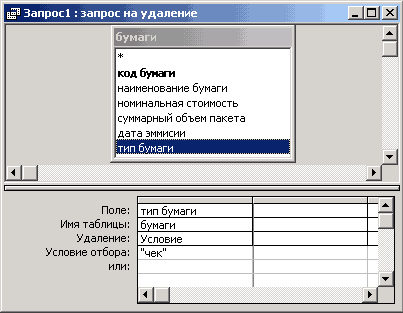
288. The picture shows:
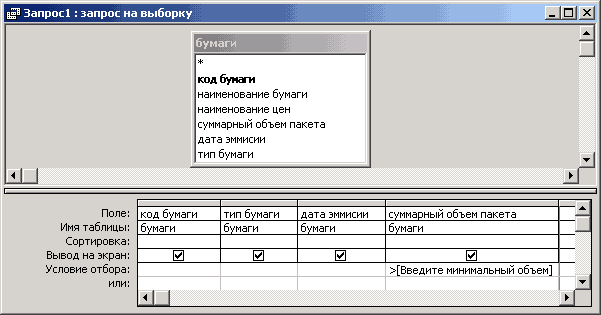
Forming a query with a parameter in design mode
Forming a request to delete records in design mode
Displaying the result of a select query
- formation of a cross query in the "Query Wizard" mode
10. Local and global computer networks.
10.1. Computer networks: concept, structure, characteristics.
289. Complex of hardware and software tools that allow computers to exchange data are:
Interface
Highway
Data buses
- computer network
290. The hardware component of a computer network means:
Programs that control network hardware
Types of hardware connections in the network
- network computers, network devices, communication lines
Network computers only (servers and workstations)
291. The client is:
The computer containing the database
- computer (program) using the corresponding resource
A computer that uses an operating system autonomously
Program for providing network services
292. The server is:
- a personal computer connected to a network that provides a user with access to its resources
Computer connected to a local or global network
User's personal computer
Computer program that uses the corresponding resource
293. A computer that provides part of its resources to network clients is called
- server
Work station
294. The technological mode of remote access to information resources of the network with delayed issuance of the result of the request is called:
- off-line
network
Consistent
295. The technological mode of remote access to network information resources in real time is called:
- Online
one time
Consistent
296. A computer that provides its resources when working together is called:
common station
- server
resource server
Client
297. A group of computers connected by information transmission channels and located within a territory limited by small sizes: rooms, buildings, enterprises, is called:
global computer network
information system with hyperlinks
- local computer network
Regional computer network
298. A computing (computer) network is used to ...
- providing independent communication between several pairs of computers
- ensuring the sharing of data, as well as hardware and software resources
- signaling from one port to other ports
- connections personal computer to Internet services and viewing web-documents
299. To store files for public access network users, is used:
- file server
client-server
Work station
Switch
10.2. Kinds computer networks and features of network information technologies.
300. Computing systems according to their territorial principle are divided into:
- local, regional, global
Terminal, administrative, mixed
Digital, commercial, enterprise
301. According to the type of organization of data transmission, computer networks are distinguished:
Local, regional, global
Computing, informational, mixed
Circuit-switched, message-switched, packet-switched
Homogeneous and heterogeneous
302. The network, where each computer can play the role of both a server and a workstation, has a ___________ architecture
peer-to-peer
star-shaped
- server
303. According to the possibility of access to information resources, computer networks are divided into:
- specialized (owned by organizations and departments) and public
Local and global
Homogeneous and hybrid
Peer-to-Peer and Dedicated File Server
304. According to the location of information resources in the network, computer networks are divided into:
Specialized (owned by organizations and departments) and public
- local and global
Homogeneous and hybrid
Centralized storage of information and distributed storage of information
10.3. Topology of local computer networks.
305. The generalized geometric characteristic of a computer network is called ....
- network operating system
- logical network architecture
- network card
- network topology
306. The network topology is determined by:
- method of connecting network nodes by communication channels
The type of cable used to connect computers on the network
Software structure
Characteristics of connected workstations
307. Ring, tire, star - these are the types:
Network protocols
Access Methods
network software
- network topologies
308. What kind of connection of computers does a star LAN topology imply?
Each computer with each in a ring
All computers are directly connected to one device - a hub
All computers are connected to the same bus
- all of the above answers are correct
309. The configuration (topology) of a local computer network, in which all workstations are connected directly to the server, is called:
Annular
- radially
treelike
Radial annular
10.4. Standardization of computer networks.
310. A computer network protocol is:
- network node connection scheme
- program for connecting individual network nodes
- software suite
- a set of rules that govern how information is exchanged over a network
311. The OSI reference model characterizes:
- interaction 7 network layers messaging
- properties of data channels
- computer network software composition
- all of the above is correct
312. The basic OSI model uses the following data transfer layers:
- physical, link, network, transport, session, representative, application
- transmission of characters, messages, packets
- local, regional, global
- physical, channel, network, application
313. The picture shows:
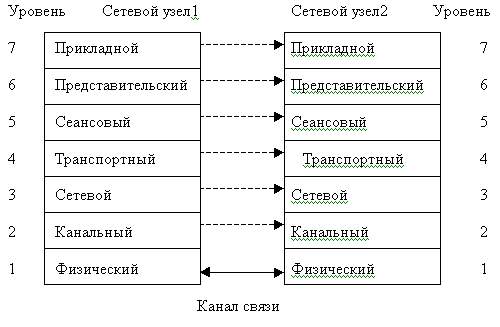
OSI Reference Model
Types of protocols for global computer networks
Types of topologies local networks
Types of data channels
©2015-2017 site
All rights belong to their authors. This site does not claim authorship, but provides free use.
Applied Informatics a set of information technologies used to process information related to practical activities. Technology activities related to the application of the results of scientific research for the creation and use of material and spiritual values. Informatization of society is the process of creating optimal conditions for meeting the information needs of citizens and organizations based on the use of information technologies. Computer universal device for information processing.
Share work on social networks
If this work does not suit you, there is a list of similar works at the bottom of the page. You can also use the search button
Other similar works that might interest you.wshm> |
|||
| 10929. | Subject and basic concepts of computer science | 13.39KB | |
| Informatics is a complex technical science that systematizes the methods of creating, preserving, reproducing, processing and transmitting data by means of computer technology, as well as the principles of operation of these tools and methods for managing them. The emergence of informatics is due to the emergence and spread of new technology collection, processing and transmission of information related to the fixation of data on machine media. As part of the main task today, it is possible to single out such main areas of informatics for practical application ... | |||
| 4464. | Basic concepts and methods of the theory of computer science and coding | 31.67KB | |
| Signals, data, information; information as a subject of study of informatics; information properties; information classification. The concept of economic information, its properties. The structure of economic information. Classification of economic information. | |||
| 7974. | BASIC INFORMATION ABOUT MEASUREMENTS. BASIC CONCEPTS AND DEFINITIONS | 39.54KB | |
| Definition of concepts metrology standardization certification Metrology is the science of measurements about ways to achieve the required accuracy and reliability of correct recording of results to ensure the uniformity of measurements. Technical measurements using working measuring instruments. Metrological measurements using standards and exemplary measuring instruments. They cannot be applied in the area to which the requirement of uniformity of measurements applies. | |||
| 10419. | The concept of informatics. Subject and tasks of informatics | 17.64KB | |
| There is a lot of information in the world: written, spoken, visual. Until recently, the carriers of information were language, various material surfaces, paper, etc. Now we are gradually moving to digital storage of information. Why it is needed First, the storage of information becomes less voluminous. | |||
| 6303. | Basic requirements for the selection and synthesis of catalysts. The composition of the contact masses. Main types of promoters. The concepts of the active component, carrier (matrix) and binder of heterogeneous catalysts and adsorbents | 23.48KB | |
| In addition to the chemical composition, an active catalyst requires a high specific surface area and an optimal pore structure. Note that a high specific surface area is not necessary to obtain a highly selective catalyst. Among other things, it is desirable to minimize the deposition of coke on the catalyst surface in organic reactions and to maximize the period of catalyst operation before regeneration. The preparation of the catalyst must be highly reproducible. | |||
| 8399. | Inheritance. Basic concepts | 41.01KB | |
| Each object is a specific member of a class. Objects of the same class have different names but the same data types and internal names. Objects of the same class have access to the same class functions and the same operations configured to work with class objects to process their data. And new classes are formed on the basis of base derived classes by descendants of child classes. | |||
| 6723. | Basic concepts of labor physiology | 34.25KB | |
| Labor and work. Labor is the expedient activity of people for the creation of use values. Being a social category, labor is determined by social, economic and industrial relations in society. | |||
| 14763. | Basic concepts of project management | 17.7KB | |
| Basic concepts of project management A project is a set of time-distributed activities or activities aimed at achieving a set goal. Achieving this result means the successful completion and completion of the project. For example, for a building construction project, the result is the building itself accepted for operation. As well as the beginning, the end of the project can be set directively or calculated when drawing up the work plan. | |||
| 2194. | Basic concepts of the psychology of creativity | 225.11KB | |
| Creativity from English. Initially, creativity was considered as a function of the intellect and the level of development of the intellect was identified with the level of creativity. Subsequently, it turned out that the level of intelligence correlates with creativity up to a certain limit, and too high intelligence hinders creativity. At present, creativity is considered as a function of a holistic personality, irreducible to intelligence, dependent on the whole complex of its psychological characteristics. | |||
| 2131. | Basic concepts of component technologies | 231.84KB | |
| This is a rather arbitrary and abstract element of the system structure, allocated in a certain way among the environment, solving some subtasks within the framework of the general tasks of the system and interacting with the environment through a certain interface. Component diagrams in the UML often depict components that are assembly and configuration management units; files with code in some language; binary files; any documents included in the system. Sometimes components appear there, which are deployment units ... | |||
Local and global networks. Basic concepts. Network and distributed operating systems.
When two or more computers are physically connected, a computer network is formed.
In general, the creation of computer networks requires a special Hardware
· - network hardware
· and special software - network software.
Already now there are areas of human activity that fundamentally cannot exist without networks (for example, the work of banks, large libraries, etc. Networks are also used in the management of large automated industries, gas pipelines, power plants, etc. Computers use a wide variety of physical channels, commonly referred to as transmission medium.
The purpose of all types of computer networks is determined by two functions:
Ensuring the sharing of hardware and software resources of the network;
· Sharing access to data resources.
For example, all members of the local network can share one common printing device - network printer or, for example, resources hard drives one dedicated computer - file server. Similarly, software can be shared. If the network has a special computer dedicated to the sharing of network members, it is called file server.
Groups of employees working on the same project within the local network are called working groups . Within the same local network, several workgroups can work. Members of workgroups can have different rights to access network shares.
The set of techniques for separating and restricting the rights of participants in a computer network is called network policy .
Network policy management is called network administration.
Face, organization manager the work of participants in a local computer network is called system administrator .
Main characteristics and classification of computer networks
According to the territorial prevalence of the network can be:
local,
global,
and regional.
Local area network (LAN - Local Area Network) - a network within an enterprise, institution, one organization.
Regional network (MAN - Metropolitan Area Network) - a network within a city or region.
Wide area network (WAN - Wide Area Network) - a network on the territory of a state or a group of states.
According to the speed of information transfer, computer networks are divided into:
· low- up to 10 Mbps ,
· medium up to 100 Mbps
· and high speed - over 100 Mbps
According to the type of transmission medium, networks are divided into:
Wired (coaxial cable, twisted pair, fiber optic);
· wireless with information transmission via radio channels or in the infrared range.
According to the way of organizing the interaction of computers, networks are divided into:
peer-to-peer
and with a dedicated server (hierarchical networks).
All computers in a peer-to-peer network are equal. Any network user can access data stored on any computer.
The main advantage of peer-to-peer networks is the ease of installation and operation. The main disadvantage is that in the conditions of peer-to-peer networks it is difficult to solve information security issues. Therefore, this method of organizing a network is used for networks with a small number of computers and where the issue of data protection is not a matter of principle.
IN hierarchical network when installing the network, one or more servers are pre-allocated - computers that manage the exchange of data over the network and the distribution of resources.
Any computer that has access to the server's services is called network client or workstation .
A server in hierarchical networks is a persistent store of shared resources. The server itself can only be a client of a server at a higher level in the hierarchy.
Servers they are usually high-performance computers, possibly with several processors working in parallel, large-capacity hard drives and a high-speed network card.
The hierarchical network model is the most preferable, as it allows creating the most stable network structure and more rationally allocating resources. Also, the advantage of a hierarchical network is a higher level of data protection.
The disadvantages of a hierarchical network, compared to peer-to-peer networks, include:
1. The need for an additional OS for the server.
2. Higher complexity of network installation and upgrade.
3. The need to allocate a separate computer as a server.
According to the technology of using the server, networks with a file-server architecture and networks with a client-server architecture are distinguished. The first model uses a file server that stores most programs and data. At the request of the user, they are sent required program and data. Information processing is performed at the workstation.
In systems with a client-server architecture, data is exchanged between the client application and the server application. Data is stored and processed on a powerful server that also controls access to resources and data. The workstation receives only the results of the query.
The main characteristics of networks are:
Bandwidth- the maximum amount of data transmitted by the network per unit of time. Throughput is measured in Mbps.
Network response time- the time spent by the software and devices of the network to prepare for the transmission of information over this channel. Network response time is measured in milliseconds.
Network topologies
A network topology refers to the physical or electrical configuration of the cabling and network connections.
In network topology, several specialized terms are used:
· network node - computer or network switching device;
· network branch - a path connecting two adjacent nodes;
· end node - a node located at the end of only one branch;
· intermediate node - a node located at the ends of more than one branch;
· adjacent nodes - nodes connected by at least one path that does not contain any other nodes.
There are only 5 main types of network topology:
1. Topology “Common Bus”. In this case, the connection and data exchange is carried out through a common communication channel, called a common bus:
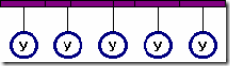
The shared bus is a very common topology for LANs. The transmitted information can be distributed in both directions. The use of a common bus reduces the cost of wiring and unifies the connection of various modules.
The main advantages of such a scheme are the low cost and ease of cabling around the premises. The most serious disadvantage of the common bus is its low reliability: any defect in the cable or any of the many connectors completely paralyzes the entire network. Another disadvantage of the shared bus is its low performance, since with this connection method, only one computer at a time can transmit data to the network. Therefore, the bandwidth of the communication channel is always divided here between all network nodes.
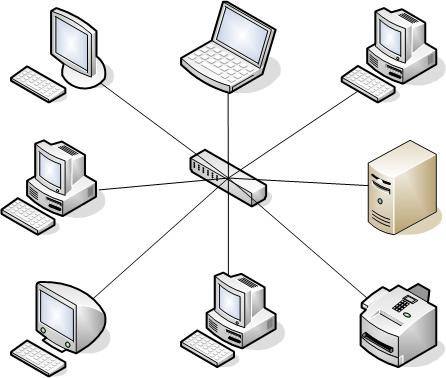
2. Topology "Star". In this case, each computer is connected by a separate cable to a common device, called a hub, which is located in the center of the network:
The function of the hub is to direct the information transmitted by the computer to one or all other computers on the network. The main advantage of this topology over a common bus is significantly greater reliability. Any trouble with the cable concerns only the computer to which this cable is connected, and only a malfunction of the hub can disable the entire network. In addition, the concentrator can play the role of an intelligent filter of information coming from nodes to the network and, if necessary, block transfers prohibited by the administrator.
The disadvantages of a star topology include the higher cost network equipment due to the need to purchase a concentrator. In addition, the ability to increase the number of nodes in the network is limited by the number of hub ports. Currently, the hierarchical star is the most common type of link topology in both local and wide area networks.
3. Topology “Ring”. In networks with a ring topology, data in the network is transmitted sequentially from one station to another along the ring, usually in one direction:
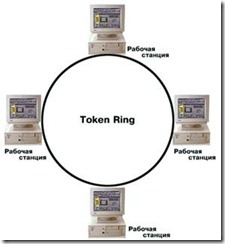
If the computer recognizes the data as intended for it, then it copies it to itself in an internal buffer. In a network with a ring topology, special measures must be taken so that in the event of a failure or disconnection of a station, the communication channel between the other stations is not interrupted.
The advantage of this topology is the ease of management, the disadvantage is the possibility of failure of the entire network if there is a failure in the channel between two nodes.
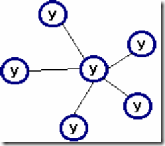
4. Cell topology. A mesh topology is characterized by a computer connection scheme in which physical communication lines are installed with all nearby standing computers:
In a network with a mesh topology, only those computers between which intensive data exchange takes place are directly connected, and for data exchange between computers that are not connected by direct connections, transit transmissions through intermediate nodes are used. Mesh Topology Allows Connection a large number computers and is typical, as a rule, for global networks.
The advantages of this topology are in its resistance to failures and overloads, since there are several ways to bypass individual nodes.
5. Mixed topology. While small networks, as a rule, have a typical topology - a star, a ring or a common bus, large networks are characterized by the presence of arbitrary connections between computers. In such networks, it is possible to single out separate arbitrarily subnets with a typical topology; therefore, they are called networks with a mixed topology.
Modern humanity practically cannot imagine its life without computers, but they appeared not so long ago. Over the past twenty years, computers have become an integral part of all fields of activity, from office needs to educational needs, thus creating a need to develop capabilities and develop related software.
Networking computers has made it possible not only to increase but also to reduce the cost of maintaining them, as well as to reduce time. In other words, computer networks have two goals: sharing software and hardware, as well as providing open access to data resources.
The construction of computer networks occurs on the principle of "client-server". At the same time, the client is an architectural component that, using the login and password, uses the capabilities of the server. The server, in turn, provides its resources to the rest of the network participants. This can be storage, creating a shared database, using I/O facilities, etc.
Computer networks are of several types:
Local;
Regional;
Global.
Here it will be fair to note on what principles various
Organization of local computer networks
Typically, such networks unite people who are at a close distance, therefore they are most often used in offices and enterprises for storing and processing data, transmitting its results to other participants.
There is such a thing as "network topology". Simply put, it is a geometric scheme for connecting computers to a network. There are dozens of such schemes, but we will consider only the basic ones: bus, ring and star.
- A bus is a communication channel that connects nodes in a network. Each of the nodes can receive information at any convenient moment, and transmit - only if the bus is free.
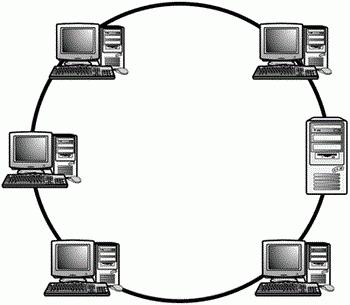
- Ring. With this topology, the work nodes are connected in series in a circle, that is, the first station is connected to the second, and so on, and the last one is connected to the first, thereby closing the ring. The main disadvantage of this architecture is that if even one element fails, the entire network is paralyzed.
- A star is a connection in which the nodes are connected by rays to the center. This connection model has come from those distant times, when computers were quite large and only the host machine received and
As for global networks, then everything is much more complicated. Today there are more than 200 of them. The most famous of them is the Internet.
Their main difference from the local ones is the absence of the main administrative center.
Such computer networks operate on two principles:
Server programs located on network nodes that are engaged in user service;
Client programs hosted on user PCs and using server services.
Global networks give users access to various services. There are two ways to connect to such networks: through a dial-up telephone line and through a dedicated channel.
