Instruction
To find out the port, use the netstat command in the operating system console. To do this, select the "Run" command from the "Start" menu, in the window that appears, write cmd and press the Enter key. Or select Start->All Programs->Accessories->Command Prompt. In the console that opens, type netstat, then press Enter. You will see a list of IP addresses and ports in use on your computer.
All this happens in the background and is usually invisible to the user. By the way, your router also has a firewall feature that effectively prevents attacks from the Internet. After a few seconds, it will display the results. However, if you select "Scan All Ports" next to "Scan Type", it is likely that the software will detect open ports which it cannot display.
Enter the port number and click "Search". The database stores preferred port numbers from hundreds of applications, as well as Trojan viruses. However, the message "Unable to get owner information" usually appears several times. In most cases, open ports are harmless.
To explore the capabilities of the command more fully, enter netstat /? and review the information provided. For example, if you enter the netstat command with the -a option, all connections will be displayed on the screen, as well as the ports in use. The netstat -o command will additionally display the ID of the process that is responsible for any connection. Typing netstat -n will show the real IP addresses and port numbers. By default, DNS names and common aliases are shown.
However, they are also used by hackers to track the configuration of someone else's machine. Therefore, in many companies and university networks they are banned, they are threatened with warnings and layoffs. The port scan run is only performed on your private network. The Hypertext Transfer Protocol is the protocol used in every transaction on the Web.
How they are used
It is a transaction oriented protocol and follows a request-response pattern between client and server. The client that makes the request is known as the "user agent". Resources can be files, the result of running a program, a database query, automatic document translation, and so on.
If you do not want to use the command line, download the TCPView utility from the official Microsoft website at http://technet.microsoft.com/en-us/sysinternals/bb897437. It provides the same functionality, but with a graphical interface. After downloading the program, run it and agree to the license agreement. In the program window, you will see a process using network connection, protocol, name and port, destination port or address, status.
Developing web applications often requires persistence of state. Likewise, some computer experts advise that a fairly simple procedure can be followed to have port 80 signs. So you can have port 80 signs located on the server that receives requests from remote computers.
Application in URLs
But then you can change it without further problems, and that's it. They can work simultaneously on the Internet. Each of these programs works with a protocol. Sometimes a team needs to be able to distinguish between different data sources. Therefore, to facilitate this process, each of these applications can be assigned a unique computer address encoded in 16 bit:port.
There are also other programs with which you can determine the open ports of the computer. For example, Nmap (http://nmap.org), Advanced Port Scanner (http://www.radmin.ru/products/previousversions/portscanner.php), etc.
The next option is to use specialized Internet services that check ports. The site http://2ip.ru can serve as an example. Go to http://2ip.ru/port-scanner/ in your browser to check for potentially dangerous open ports. At http://2ip.ru/check-port/ you can check any particular port.
Thus, when the equipment receives information directed to a port, the data is sent to the appropriate application. If it is a request sent to an application, the application is called a server application. If this is the answer, we are talking about the client application.
These operations can be performed through a port, i.e. a number associated with the type of application, which, in combination with one, allows you to uniquely identify the application running on specific computer. Ports 0 to 023 are known or reserved ports. In general terms, they are reserved for system processes or programs executed by privileged users. However network administrator can connect services to ports of its choice. Ports 024 to 151 are registered ports.
Verify ports on computer possible in several ways. Open and not used by system processes or local network the port can be the reason for the penetration of dangerous software into the system, access to your computer from the outside.
Instruction
First of all, such a situation should be prevented by protection systems: antivirus and firewall. If you do not have them installed, then you need to install and check the system. Moreover, it is desirable to install an effective and optimal protection tool (for example, Kaspersky Internet Security). But if such software has not been used before, then perhaps malicious, open port has long been actively used by dangerous applications.
On the client side, the operating system chooses a port among those that are available at random. What are ports and what is port forwarding? Ports are virtual cables that allow computers and devices to communicate and send information over the Internet.
Port routing can improve connection speed, room latency, and game play in general, especially for the host. Now that you know the basics, you are ready to forward ports. Follow the links below depending on the platform you are using.
The easiest way to check the availability of such a port is with a simple text that can be carried out online at the link: http://2ip.ru/port-scanner/. If during the analysis of your computer, an open port is found (potentially dangerous for the system), the program will show it in red. If such a port is found during the check, write down its name separately, since it urgently needs to be closed.
Most proxy servers, firewalls, and other Internet connection methods can restrict access to ports. Your configuration may restrict data packets from unknown sources. Make sure you have set the following ports. To set up a firewall for your operating system, select it below.
Enter a name for this rule.
- Click "Next" Domain, public and private are checked.
- Click "Next" Next.
- Click next.
- Select the "Allow Connection" button.
- Make sure the "Domains", "Publication" and "Private" boxes are checked.
You can close such a port with the help of many programs. But the simplest is Windows Worms Doors Cleaner, which is only 50 kb in size and does not require installation (you can download it at: http://2ip.ru/download/wwdc.exe). After downloading it, you just need to start and close the malicious port, which was revealed by the analysis of the computer after verification. Then you need to restart your computer. However, this is rather a quick action, so to speak, since over time the port can be opened again. Therefore, it is advisable to install a firewall (for example, Outpost Firewall) and keep the status quo after closing the dangerous port.
This makes it easier to use firewall protection and prevents unwanted applications from controlling network ports. For example, receiving and sending messages Email, web browsing, file transfer, are different processes in which each of them will use different software. These local addresses are used to direct the various activities that exist on the Internet to the appropriate on-premises software.
Think of your computer as a building of a building with multiple rooms and rooms for different functions. In fact, in the standard format, one section is reserved for a designated port. Special attention It is emphasized that there are no conflicts between ports. Other ports are called "dynamic" or "private ports". These ports are not regulated.
It also does not hurt to check your computer with a free AVZ utilities(you can download from the link: http://www.z-oleg.com/secur/avz). In the course of a quick test, it is necessary to identify errors in the system settings, possibly brought down using the same port. For example, if "anonymous user" is allowed, disable it and restart the computer.
For a more extensive list of existing ports, please click here. Ensuring port security. Applications or services "listen" on the port assigned to them. If precautions are not taken in this eavesdropping, the port will be open to incoming signals and may be vulnerable from the outside. We can avoid this problem with a firewall. The firewall will monitor incoming signals and block those that your system did not specifically request. Many firewalls can also monitor outbound traffic, preventing unauthorized outbound connections.
Sources:
- checking ports for opening
Name computer is selected by the user during system installation and can be changed at any time. It is necessary to identify the computer on the network and cannot contain more than fifteen printable characters, spaces, and special characters such as punctuation marks. If you need to know the full computer name, refer to the system components.
This is very useful when we want to protect ourselves from Trojans or other activities such as spyware or adware. There is no unprotected computer on the Internet, so we are fully confident that our equipment is at risk.
Even if you have a good firewall installed, it's a good idea to scan your computer to see how they appear online. This good way find out the state of our computer in relation to the Internet. No other additional configuration not required, but the following requirements must be met.

Instruction
Press the start button or Windows key on keyboard. Select "Control Panel" from the menu. In the Performance and Maintenance category, left-click on the System icon. The System Properties component opens. If the control panel has classic look, select desired icon straightaway.
Click "Next" and continue through the remaining screens until the installation is complete. 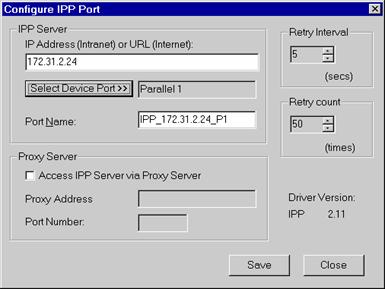
- This will launch the Add Printer Wizard.
- Follow the instructions to complete the process.
- The retry interval sets the time interval between connection attempts.
- If the connection is poor or the remote server is very busy, increase this number.
- The retry counter sets the number of connection attempts.
You can call the System Properties component in several other ways. Open the Start menu and find My Computer. Click on it right click mouse and select context menu The last item is "Properties". The same can be done from the desktop by selecting the "My Computer" item.
In the System Properties window, click the Computer Name tab. In the "Full Name" field, you will see the name that is assigned to the computer and is currently in use. To change the name, on the same tab, click the Change button. An additional "Change computer name" window will open.
Other parts of the toolbar
Computers connected to the Internet are called clients and servers. A simplified diagram of interaction with requests and responses looks something like this. Clients are typical Internet users connected to the Internet and Internet access programs available on these devices. When a client device wants to access a page, a copy of it is downloaded from the server to the client machine, which will be displayed in the browser. Servers are computers that store pages or applications. . The client and server we describe do not tell the whole story.
When choosing a new name, remember: the shorter it is, the better. Also, you cannot give a computer a name that is already in use on the network. This can lead to conflicts in network interaction. After entering a new name, click on the OK button and apply the new settings.
You can also find out the full computer name using the System Information component. To call it, click the "Start" button and select "Run" from the menu. Enter msinfo32.exe in the empty line of the window that opens and press the Enter key or the OK button.
There are many other parties involved and we will describe them below. For now, let's pretend the Internet is a road. At one end of the road we have a client who is like his house. On the other hand, we have a server which is like a store where you want to buy something.
So what's going on?
It's like transport mechanisms that let you walk into a mall, place an order, and buy. This is similar to the language you use to place your order and talk to the person delivering your order. The website is made up of many different files that are part of your purchase from the store.
- Internet connection: Allows you to send and receive data from the Internet.
- component files.
A new dialog box will open. Select with the mouse the line "System Information" in the left part of the window. Find in the "Element" group in the right part of the window the position "System name". The Value group will contain the name of the computer. The Username line also contains information about the computer name. The entry might look like [computer name]/user account.
That's it, and then it starts sending the site's files to the browser as a series of small chunks called data packets. The browser mounts small fragments to the full website and shows you. . Real internet addresses aren't cool, it's easy to remember the texts you type in the address bar to find your favorite websites. They are sets of numbers, e.g.
However, this is not easy to remember, is it? That's why the Domain Name Service was invented. These are special servers for linking the web address entered in the browser to the actual website address. You may have heard of port scanning. But not many people know exactly what it is.
The software port is a conditional number from 1 to 65535 that indicates which application the data packet is addressed to. The port that works with the program is called open. It must be borne in mind that at the current moment any port can work with only one program.

The port is the address of the application on the machine. When you enter a site name to connect to in your browser, it will automatically request port 80 of the requested server. By default, most computers, whether acting as a server or a client, have ports open.
What are the connection states?
There are different ways, the simplest is to get into command line. But it must be used with certain read options. So, we can see that my machine has a nice packet of open ports! The application really duplicates! This is what we see below.
Instruction
If your computer is not permanently connected to the Internet, connect it to the global network, for example, by turning on the modem and running the program that serves it. Also, launch the browser or program that you want to connect to the server on a port you do not know in advance. Try entering the site address in the address bar of the browser: if after that a colon and a port number are automatically added to it, further actions can be omitted - it will become known to you anyway.
The second line shows that the connection is established on port 22 between machine 254 and the server. We also see that machine 254 is also listening on the port. In fact, this is a port randomly chosen by the client's browser to receive responses from the server. The client sends its requests to port 80 of the server, and the latter replies to it on a random port that it chose during connection initialization.
Now we know what a port is, and we have seen that our machines have open ports. Those who listen because we have services for others AND those who are installed because we are in the process of communicating with another machine. So, back to our sheep.
Open the console. AT operating system For Linux, run rxvt, xterm or Konsole for this. In Windows, use the cmd program ("Start" - "Run" - enter cmd - "OK").
When the console opens, start the process of connecting the program you are interested in to the Internet, or start updating the page you are interested in in the browser, and then immediately (until the connection is closed) enter the netstat -ano command into the console (there is a space before the minus, but not after it).
Two tables will be displayed on the screen. Pay attention to the column External address» (or Foreign Address) of the first of these tables. It will list the IP addresses, after each of which the port will be indicated with a colon. It usually has the number 80, which is open to all providers. If you see other ports, call the provider's support service, name your tariff and ask if such ports are open for you. You can also set the appropriate password in the provider's support forum. If it turns out that the ports are closed, if possible, reconfigure the program so that it connects to the server on a different port. You can view the contents of the page using the Opera Turbo, Skweezer or similar service. As a last resort, switch to a more expensive tariff, having previously found out whether the port you need will then be open. Please note that opening some ports poses a security risk to the system.
The software port is a conditional number from 1 to 65535 that indicates which application the data packet is addressed to. The port that works with the program is called open. It must be borne in mind that at the current moment any port can work with only one program.
Instruction
You can get a list of open ports and their associated applications different ways. If you want to use Windows tools, call the command line with the Win + R hotkey combination and enter the cmd command. In the console window that opens, type netstat -a -n -o
The program will display a list of active connections. In the column " Local address” indicates the network address of your computer and, separated by a colon, the port number that is occupied by some application. IP is displayed in the column "External address" remote computer and the port number that this application communicates with. The PID column contains the process identification number. Find the port you are interested in and write down the PID associated with it.
Apply the hot key combination Ctrl+Alt+Delete and in the opened window « Windows Security» Click Task Manager. This service can be started in another way: call the command window with the Win + R combination and enter the taskmgr command. In the "View" menu, check the "Select Columns" option and check the box next to "Process Identifier (PID)". Look in the PID column for the process number you are interested in, and in the Image Name column for the name of the program that uses the corresponding port.
You can find out active ports and their associated applications using software port scanners such as TCPView. It's spreading
