If you need to scan the ports of computers and devices from Windows in local network or online, then one of the best options is a bundle of Nmap and Zenmap (a GUI for Nmap).
Nmap has a large number of scan options, and Zenmap's graphical user interface makes it extremely easy to use.
Nmap features include:
- port scan
- determining the operating system of a remote host
- service definition, software and their versions on the remote host
Using Nmap scripts, you can check remote hosts for vulnerabilities, weak passwords, collect certain information, look for services that allow anonymous login, and perform other tasks related to the actions of a network administrator or penetration tester.
Run the downloaded Nmap installer, in addition to the main program, it will also install several components that are necessary for Nmap to work on Windows.
When everything is ready, a shortcut to the program will appear on the desktop:
The main program window looks like this:
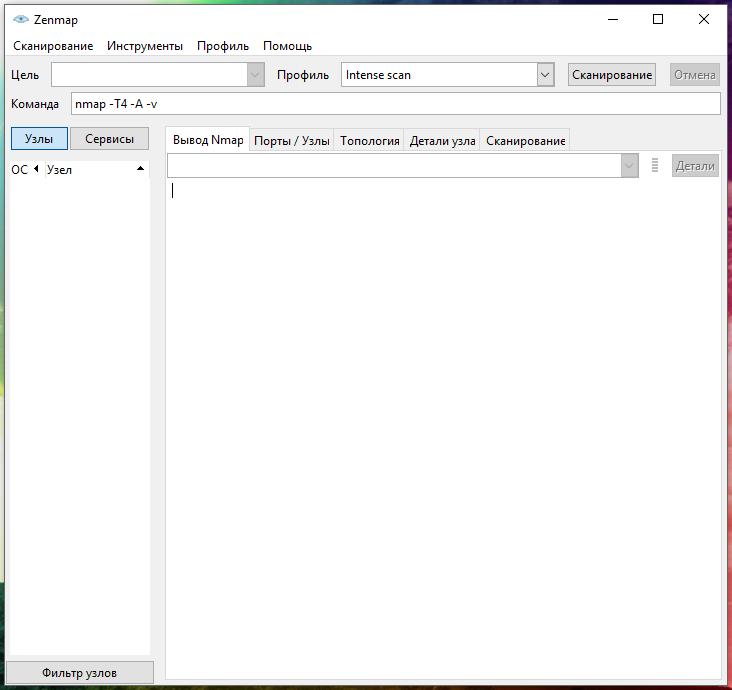
In field Target you need to specify the site address (URL), IP or range of IP addresses to be scanned.
In field Profile select the desired profile from the drop-down list.
How to Specify Target in Zenmap (Nmap)
Website addresses should be specified without a protocol, for example:
- mi-al.ru
- suip.biz
It would be incorrect to indicate the form https://mi-al.ru
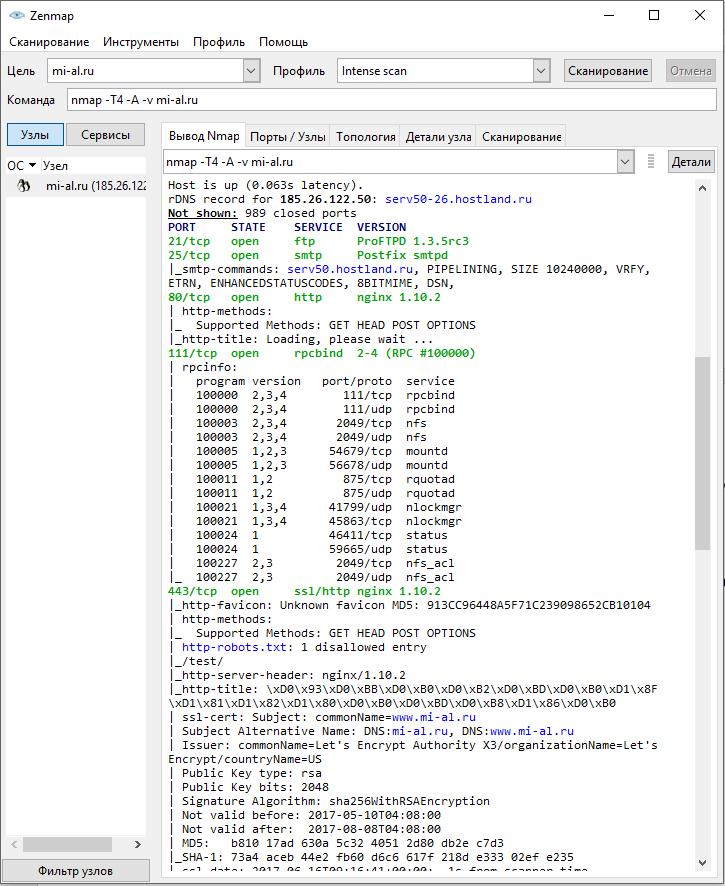
IP addresses can be specified one by one, for example, 192.168.0.1; using CIDR addressing, for example, 192.168.0.1/24; as well as specifying ranges in one or more octets, for example, 192.168.0.1-100, or 192.160-170.50-100.1
What do Profiles mean in Zenmap
Profiles in the main Zenmap window are a set of options for typical scans. Consider all Zenmap profiles.
- intensive scan(Intensive scan)
Intensive all-round scanning. Option -A includes several other options at once: OS version detection ( -O), determining the versions of running services ( -sV), scanning using scripts ( -sC) and tracing ( --traceroute). Without administrator privileges, only version detection and scripted scanning are launched. This is considered an intrusive (intrusive) scan.
- intensity scan plus UDP(Intensive scanning plus UDP)
Makes OS detection ( -O), version detection ( -sV), scanning with scripts ( -sC) and tracing ( --traceroute) in addition to TCP and UDP port scanning.
- Intense scan, all TCP ports(Intensive scanning, all TCP ports)
Scans all TCP ports, then does OS detection ( -O), version detection ( -sV), script scanning ( -sC) and tracing ( --traceroute).
- Intense scan, no ping(Intensive scanning without ping)
Performs an intensive scan without first checking if the targets are working. This can be useful when targets ignore normal host discovery probes.
- ping scan(ping)
This scan only determines which targets are running and does not perform a port scan.
- Quick scan(Quick scan)
This scan is faster than a normal scan because it uses an aggressive timing pattern and scans fewer ports.
- Quick scan plus(Quick scan plus)
Quick scan plus OS detection
- Quick traceroute(Quick trace)
Traces paths to targets without performing a full port scan on them.
- regular scan(Normal Scan)
Basic scanning without additional options.
- Slow comprehensive scan(Slow all-around scan)
This is a comprehensive, slow scan. Every TCP and UDP port is scanned. OS detection in progress ( -O), version definition ( -sV), script scanning ( -sC) and tracing ( --traceroute). Many probe requests are sent to discover hosts. This is a very intrusive scan.
For example, if I want to know which subnet hosts are being pinged, then I choose the profile ping scan.
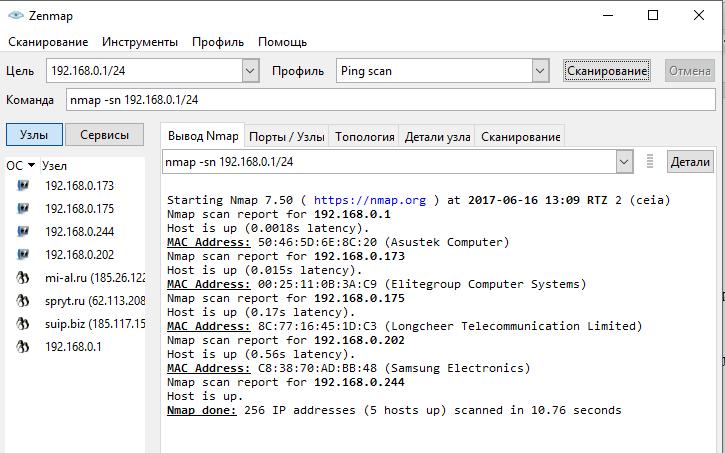
With the user-friendly profile editor, you can edit and create new profiles.

Although using the profile editor contains a description of the actions to be performed and therefore does not require knowledge of Nmap options, for a deeper understanding of the program, you can read the description of all Nmap options at https://kali.tools/?p=1317
If you want to scan all TCP ports, then specify the target and enter as a command nmap -p 1-65535

Scan results
The results obtained from the last scan are visible in the tab Output nmap. On the left side you can switch between knots and Services. When you click on a specific node, you will see the previous scan results. When you click on a service, you will see the nodes where the service was discovered:
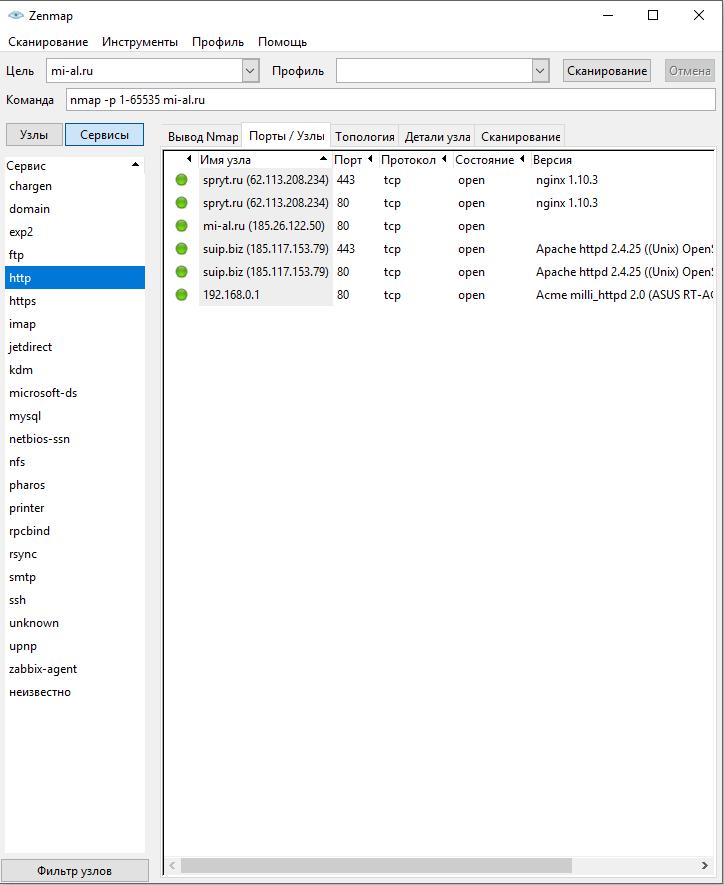
To view generalized information on a node, click on it and select the tab Node details:
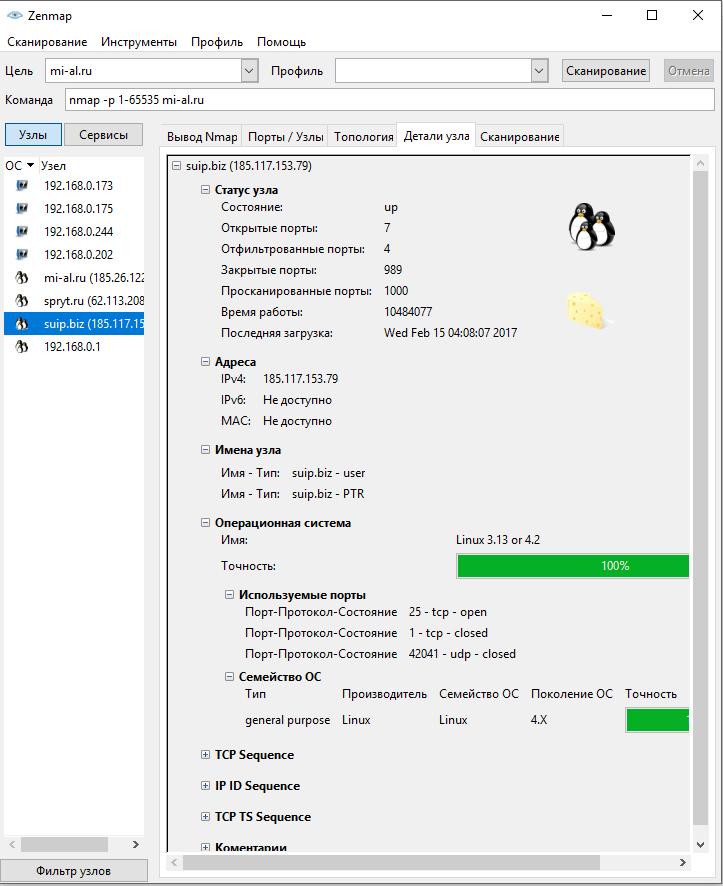
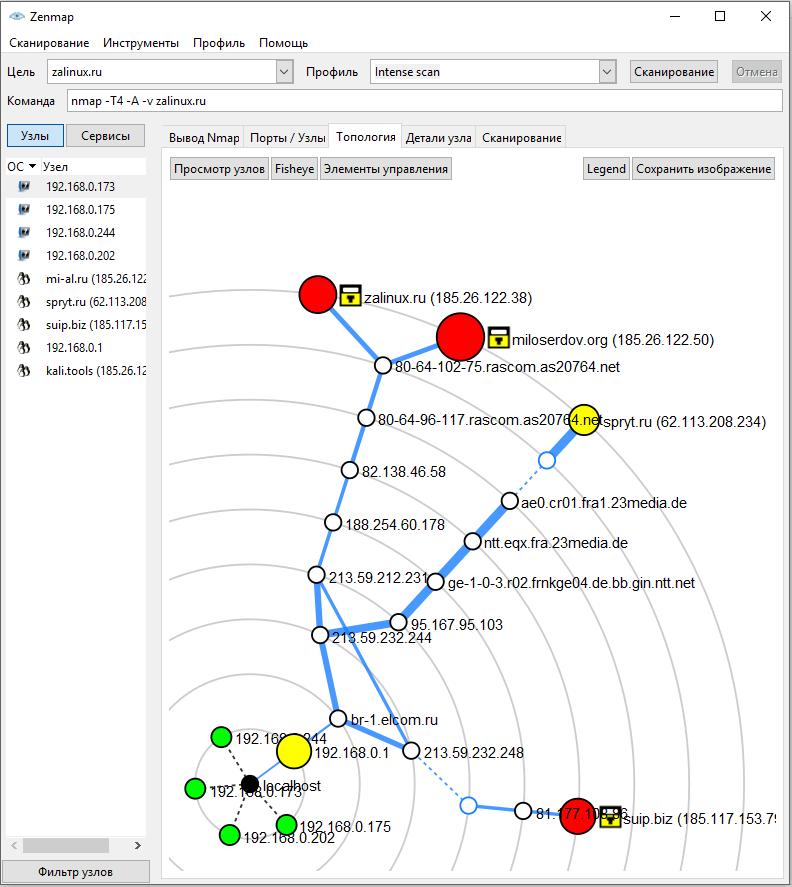
In the tab Topology you will see information about connections between scanned/discovered nodes:
Using Nmap on Windows at the Command Line
If you need a console version of Nmap, then you can use it on Windows just as you would on Linux. When installing Nmap, it adds the path to the Nmap executable to the environment variables, so in command line you just need to specify the name of the program:
Conclusion
Nmap allows Windows to scan computers and other devices for open ports. It is also able to determine the services running on a remote host, their version.
The graphical interface makes it easier to use the program, but it is recommended that you familiarize yourself with all the options of the program in order to gain skills in various scanning techniques.
In addition to their main functions - scanning ports and determining the versions of installed software - Nmap scripts allow you to perform various other tasks, including checking for vulnerabilities, weak passwords, and collecting information.
What is a port scan? What are the methods of scanning. What threats does it pose?
In today's article I will try to talk about what open port scanning is, I will talk about the methods used in port scanning and how to protect yourself from it all.
Scanning is a set of procedures that allows you to identify nodes, ports and services of the target system. Network scanning allows an attacker to collect a profile of the attacked machine.
According to the Ethical Hacking and Countermeasures EC-Council guidelines, the following types of scanning are distinguished:
- network scanning - determination of nodes located in the network;
- port scanning - identifying open ports and functioning services;
- System security scan - Identification of known system vulnerabilities.
At first glance, there is no harm in scanning, however, it is difficult to agree with this approach, because scanning precedes the attack, allowing the attacker to find out which services are running on the target system, and therefore prepare and conduct a targeted attack against the identified services and their vulnerabilities. Therefore, it is necessary to fight the intelligence of intruders.
Port Scan Purposes
At the same time, it would be useful to note that scanning itself is not always a malicious action, it all depends on its goals. Services information security or IT staff may well resort to scanning to find out infrastructure vulnerabilities or visibility of services from an external network.
In fact, it often starts with network scanning, it is this that allows you to identify weak nodes of their IP addresses, open ports, determine the operating system, which means that theoretically possible vulnerabilities become clear, which is not so little for the organizer of the attack.
Port Scan Methods
We reveal the structure of the network. The easiest way to scan is ICMP scanning. The principle of operation is based on the ICMP protocol, and this type of scanning allows you to find out the "live" nodes in the network and build a network diagram with a list of its nodes. The essence of the method is to send ICMP requests to network nodes, if a computer or other device working with the TCP / IP protocol stack is active, then a response will be sent. This is the so-called ping sweep or ICMP sweep. There are a huge number of tools that allow you to perform such a scan.
Port scanning. The next step is to identify open ports. In essence, this makes it possible to determine which services are running on a remote host, the list of which we have already received as a result of the previous scan. In addition, from the analysis of the received packets, you can also identify the operating system and a number of other important parameters(the presence of a packet filter, for example).
Here we are talking about TCP Scan. Its principle is based on the peculiarities of TCP operation. In essence, a very similar mechanism of interaction is adopted in aviation during negotiations between pilots and the controller, including a request, a response with an indication, confirmation of the received instruction. Such a method of interaction, if not completely eliminating the possibility of misunderstanding, then at least significantly reduces such a probability.
It could look like this:
- Pilot: Sheremetyevo-Taxiing, Aeroflot 502, clear for preliminary.
- Dispatcher: Aeroflot 502, 25 right 1 on RD2 10, highway, RD5 preliminary permission.
- Pilot: Aeroflot 502, 25 right, on taxiway 10, highway, taxiway 5 preliminary cleared.
What's going on here? The pilot turned to the controller with a request for taxiing permission and his route. The dispatcher allowed taxiing and determined the route.
The pilot confirmed the route and permission of the dispatcher. Everything, you can move - the route is received.
A very similar thing happens in TCP communication. It uses a three-way-handshake or “three-way” negotiation scheme, and the term “three-way handshake” is also found, which allows you to synchronize the transmitting and receiving nodes and establish a session, which is essentially identical to the example with radio conversations.
Using this legal algorithm, an attacker can find out which ports are open on the server, that is, to understand what services are used in the system, what operating system. To do this, there are several effective methods.
Full Connect Scan
Some port scanning techniques. The most efficient and uncomplicated scanning method is Full Connect Scan (Full Open Scan). Its principles are shown in Figure 3. An attempt is made to perform a three-way handshake with the nodes of interest to the researcher. If the desired port is open, then we receive a SYN + ACK message from it, after that we send RST to the node (session reset), if it is closed, then we receive RST from the node being checked. It should be noted that this method of scanning is easily identified, therefore, it is not difficult to resist it.
stealth scan
Another network scanning method is called Stealth Scan (Half-open Scan). In this case, the attacker tries to bypass the firewall protection and disguise itself as normal network traffic in order to avoid fixing the scan event in the system logs. Here we are not talking about negotiation, the researcher simply sends a SYN packet to the port of interest on the required server. If the response is SYN+ACK, then the port is open; if RST, then the port is closed.
This method of scanning is more sophisticated, but modern intrusion prevention systems must be able to counter it.
Xmas Scan
No less well-known scanning methods are Xmas Scan and Null Scan, however, we will not consider them due to the fact that protection against them is implemented within modern Microsoft operating systems, so they will not be of great interest to us. A feature of these types of scanning is the stealth mode of operation, that is, without setting up a session. However, you can see the details in the Ethical Hacking course or in the book "Network Security Test Lab". These types of scans are only effective on operating systems where the TCP stack is based on RFC 793. All modern operating systems from Windows Vista and older are not at risk.
Idle Scan
Perhaps the most interesting scanning method is Idle Scan. The main idea is that an attacker can scan the victim without showing him his IP address, that is, from the point of view of the scanned host, the attacker does not seem to communicate with him. A “dummy” node is used, which can be identified by intrusion countermeasures systems as a source of attack. This is a very reasonable technique, the so-called spoofing, when the sender's address is replaced with the address of another device. I must say that a computer that has certain vulnerabilities can become a "dummy" node or "zombie". OS, as a rule, should be updated, but this is not always the case, and the attacker can always find "helpers", in addition, as a "zombie" can be used network printer or other network device that works with the basic functionality of the TCP/IP stack.
This scan uses the Identification field in the IP header (IPID). The IPID value increases by one in each next packet that the host sends. In essence, this is a vulnerability, since it becomes possible to predict how many packets were transmitted between the two packets that were received. Modern operating systems use a random value for the IPID field, however, as mentioned above, a solution can always be found. For modern Unix and Windows systems from Windows Vista and older, this problem has already lost its relevance.
Consider Figures 4 and 5. In the first step (1), the attacker accesses a rogue device with a standard SYN packet. The device responds with a SYN ACK (2) or SYN RST packet, which is more likely, but the IPID becomes visible to the attacker from the packet header. This is what you need to remember (3). Next, the attacker accesses the server of interest to him (4), while replacing his IP address with the address of a dummy host, that is, masking himself using spoofing (address spoofing). In response to this request, the server, if the port is open, sends a SYN/ACK to the spoofed address (5). We've made the change. Not knowing what to do with this packet, the rogue computer will respond by sending a RST (session reset) and incrementing its IPID. In our case, it will become equal to 30132 (6). If the port is closed, the server will send a session reset (RST) - see Figure 5(5).
Idle scanning (server port open)Idle scanning (server port closed)
The IPID of the dummy node remained unchanged, in our case 30131, because the "zombie" did not send anything to anyone else. Now it remains to turn to the “zombie” again, as we did above, to identify its IPID, compare it with the value we have. If the IPID has increased by 2, then the port is open.
Another important point that I would like to note is that operating systems have their own specifics when working with the TCP / IP stack. Using these features when analyzing packets received during scanning, it is quite possible to find out which OS we are dealing with, Banner Grabbing scanning techniques are built on these principles. The task is to reveal information about the computer system and its vulnerabilities, which will allow the attacker to use this knowledge for their subsequent destructive actions. Any modern scanner will provide the attacker with this information.
Operating systems usually need to be updated, but this is not always the case, and the attacker can find "helpers", in addition, a network printer or other network device that works with the basic functionality of the TCP / stack can be used as a "zombie" IP
It is easy to see that all the considered scanning methods are based on the normal behavior of nodes, which means that any computer or other network device is potentially vulnerable.
An attacker has the ability to collect and analyze the information received about the network structure, services, and system vulnerabilities. This provides a potential opportunity to prepare a targeted attack against certain nodes and services.
The argument to the --scanflags option can be a numeric value, such as 9 (PSH and FIN flags), but using symbolic names is much simpler. Use any combination of URG , ACK , PSH , RST , SYN and FIN . For example, --scanflags URGACKPSHRSTSYNFIN will set all flags, although this is not very useful for scanning. The order in which the flags are set does not matter.
In addition to setting the desired flags, you can also specify the type of TCP scan (for example, -sA or -sF). This will tell Nmap how to interpret the responses. For example, in a SYN scan, no response indicates a filtered port, while in a FIN scan, it indicates an open|filtered port. Nmap will implement for given type scanning, but using the TCP flags you specify instead of the default ones. If you do not specify a scan type, SYN will be used by default.
-sI <зомби_хост> [: <порт> ] ("lazy" idle scan)In addition to being invisible (by its nature), this type of scan also allows you to define IP-based trust relationships between machines. Open ports list shows open ports from the perspective of a zombie machine. So you can try to scan the target using various zombie machines that you think might be trusted (via router/packet filter rules).
You can add the port number after the colon to the zombie host if you want to use a specific port. Port 80 will be used by default.
Ports can also be given names, which they correspond to in the nmap-services file. You can even use the wildcards * and ? in names. For example, to scan ftp and all ports starting with http use -p ftp,http* . In such cases, it is better to quote the -p arguments.
Port ranges are enclosed in square brackets; ports from this range, found in nmap-services , will be scanned. For example, the following option will scan all ports in nmap-services equal to or less than 1024: -p [-1024] . In such cases, it is better to quote the -p arguments.
-sO (IP protocol scan)This type of scan allows you to determine which IP protocols (TCP, ICMP, IGMP, etc.) are supported by the target machines. Technically, such a scan is not a type of port scan, because it cycles through IP protocol numbers instead of TCP or UDP port numbers. Although it still uses the -p option to select which protocol numbers to scan, the results are in port table format, and it even uses the same scanning engine as the various port scan options. Therefore, it is quite close to port scanning and is described here.
In addition to its usefulness in its own field of application, this type of scanning also demonstrates the full power of open source software (open-source software). While the basic idea is quite simple, I never thought to include such a feature in Nmap, nor have I received any requests to do so. Then, in the summer of 2000, Gerhard Rieger developed this idea, wrote an excellent patch to embody it, and sent it to nmap-hackers newsletter. I included this patch in Nmap and released it the next day new version. Only a handful of commercial software can boast users who are enthusiastic enough to develop and deliver their improvements!
The way this type of scanning works is very similar to that implemented in UDP scanning. Instead of changing the field containing the port number in the UDP packet, the headers of the IP packet are sent, and the 8-bit field of the IP protocol is changed. The headers are usually empty, containing no data or even the correct header for the required protocol. The exceptions are TCP, UDP and ICMP. Including the correct header for these protocols is necessary because otherwise, some systems will not send them, and Nmap has all the necessary functions to create them. Instead of expecting an ICMP port unreachable message in response, this type of scan expects an ICMP unreachable message. protocol. If Nmap receives any response from any protocol, then the protocol is marked open. An ICMP protocol unreachable error (type 3, code 2) marks the protocol as closed. Other ICMP unreachable errors (type 3, code 1, 3, 9, 10, or 13) mark the protocol as filterable (at the same time they indicate that the ICMP protocol is open). If no response is received after several requests, the protocol is marked open|filtered
. -bAn interesting feature of the FTP protocol (RFC 959) is the support for so-called proxy FTP connections. This allows the user to connect to one FTP server and then ask him to transfer files to another. This is a gross violation, which is why many servers have stopped supporting this feature. Using this function, it is possible to carry out port scanning of other hosts using this FTP server. Just ask the FTP server to send the file to each port of interest on the target machine in turn. The error message will indicate if the port is open or not. This good way bypassing firewalls, because organizational FTP servers usually have more access to other internal hosts than any other machine. In Nmap, this type of scan is specified with the -b option. It is passed as an argument <имя_пользователя> : <пароль> @ <сервер> : <порт> . <Сервер> - it network name or the IP address of the FTP server. As with regular URLs, you can omit <имя_пользователя> : <пароль> , then anonymous data will be used (user: anonymous password: [email protected]). The port number (and the colon preceding it) can also be omitted; then the default FTP port (21) will be used to connect to <серверу> .
This vulnerability was widespread in 1997 when Nmap was released, but has now been patched almost everywhere. Vulnerable servers still exist, so if nothing else helps, then it's worth a try. If your goal is to bypass the firewall, then scan the target network for open port 21 (or even for any FTP services if you use version detection) and then try that type of scan with each one found. Nmap will tell you if the host is vulnerable or not. If you're just trying to cover your tracks, then you don't need (and, in fact, shouldn't) limit yourself to just the hosts on the target network. Before you start scanning random Internet addresses for a vulnerable FTP server, keep in mind that many system administrators won't like it.
Buy residential proxies on SOAX.